Get the free Coordinated Entry Vulnerability Assessment Tool
Show details
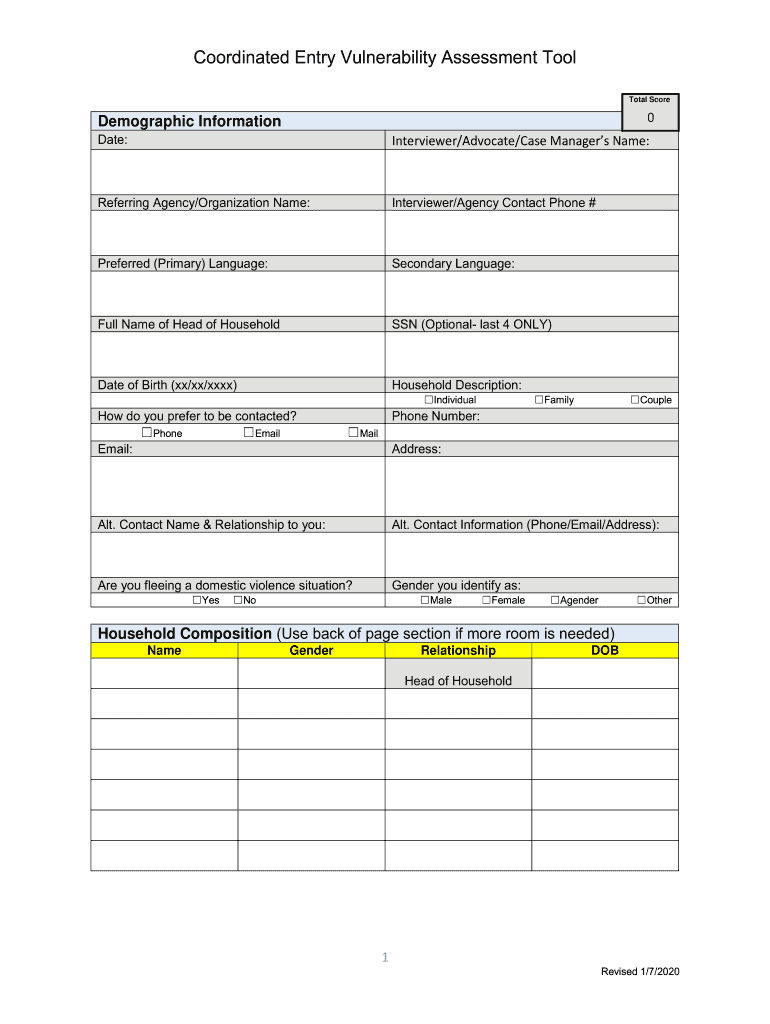
Coordinated Entry Vulnerability Assessment Tool
Total Score0Demographic Information
Date:Interviewer/Advocate/Case Managers Name:Referring Agency/Organization Name:Interviewer/Agency Contact Phone
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign coordinated entry vulnerability assessment

Edit your coordinated entry vulnerability assessment form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your coordinated entry vulnerability assessment form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing coordinated entry vulnerability assessment online
Use the instructions below to start using our professional PDF editor:
1
Log into your account. In case you're new, it's time to start your free trial.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit coordinated entry vulnerability assessment. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
With pdfFiller, it's always easy to work with documents.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out coordinated entry vulnerability assessment

How to fill out coordinated entry vulnerability assessment
01
To fill out a coordinated entry vulnerability assessment, follow these steps:
02
Start by gathering all the necessary information about the person being assessed, such as their personal details, housing history, and any relevant documentation.
03
Begin the assessment by asking a series of questions related to the individual's current housing situation, income, disabilities, and any other factors that may contribute to their vulnerability.
04
Use a standardized scoring system or rating scale to evaluate the individual's vulnerability level for each category. This may include assigning points or levels based on their answers to the assessment questions.
05
Document the individual's responses, scores, and any additional comments or observations in the assessment form.
06
Review the completed assessment with the individual to ensure accuracy and provide an opportunity for them to clarify any information.
07
Share the assessment results with the appropriate agencies or organizations involved in the coordinated entry system.
08
Update the assessment as needed or when there are significant changes in the individual's circumstances.
09
Continuously monitor and reassess the individual's vulnerability over time to ensure appropriate services and support are provided.
10
Remember to adhere to any guidelines or protocols established by your local coordinated entry system or governing body while conducting the vulnerability assessment.
Who needs coordinated entry vulnerability assessment?
01
Coordinated entry vulnerability assessments are typically required for individuals who are experiencing homelessness or at risk of homelessness.
02
This assessment helps identify individuals who are most vulnerable and in need of immediate assistance and prioritizes them for housing and support services.
03
It is often conducted by agencies or organizations involved in a coordinated entry system, such as homeless service providers, housing authorities, or community outreach programs.
04
Anyone seeking access to housing resources and support services through the coordinated entry system may need to undergo a vulnerability assessment.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I modify coordinated entry vulnerability assessment without leaving Google Drive?
Simplify your document workflows and create fillable forms right in Google Drive by integrating pdfFiller with Google Docs. The integration will allow you to create, modify, and eSign documents, including coordinated entry vulnerability assessment, without leaving Google Drive. Add pdfFiller’s functionalities to Google Drive and manage your paperwork more efficiently on any internet-connected device.
How can I send coordinated entry vulnerability assessment for eSignature?
Once your coordinated entry vulnerability assessment is ready, you can securely share it with recipients and collect eSignatures in a few clicks with pdfFiller. You can send a PDF by email, text message, fax, USPS mail, or notarize it online - right from your account. Create an account now and try it yourself.
How do I complete coordinated entry vulnerability assessment online?
pdfFiller has made filling out and eSigning coordinated entry vulnerability assessment easy. The solution is equipped with a set of features that enable you to edit and rearrange PDF content, add fillable fields, and eSign the document. Start a free trial to explore all the capabilities of pdfFiller, the ultimate document editing solution.
What is coordinated entry vulnerability assessment?
Coordinated entry vulnerability assessment is a standardized tool used to assess the vulnerability of individuals and families experiencing homelessness in order to prioritize them for housing assistance.
Who is required to file coordinated entry vulnerability assessment?
Service providers and agencies working with homeless populations are required to conduct and file coordinated entry vulnerability assessments.
How to fill out coordinated entry vulnerability assessment?
Coordinated entry vulnerability assessments can be filled out electronically or manually by trained staff members using the standardized tool provided by the local Continuum of Care.
What is the purpose of coordinated entry vulnerability assessment?
The purpose of coordinated entry vulnerability assessment is to accurately assess and prioritize the needs of individuals and families experiencing homelessness in order to efficiently allocate housing resources.
What information must be reported on coordinated entry vulnerability assessment?
Coordinated entry vulnerability assessments typically include demographic information, housing history, health and disability status, and current living situation.
Fill out your coordinated entry vulnerability assessment online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Coordinated Entry Vulnerability Assessment is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.


















