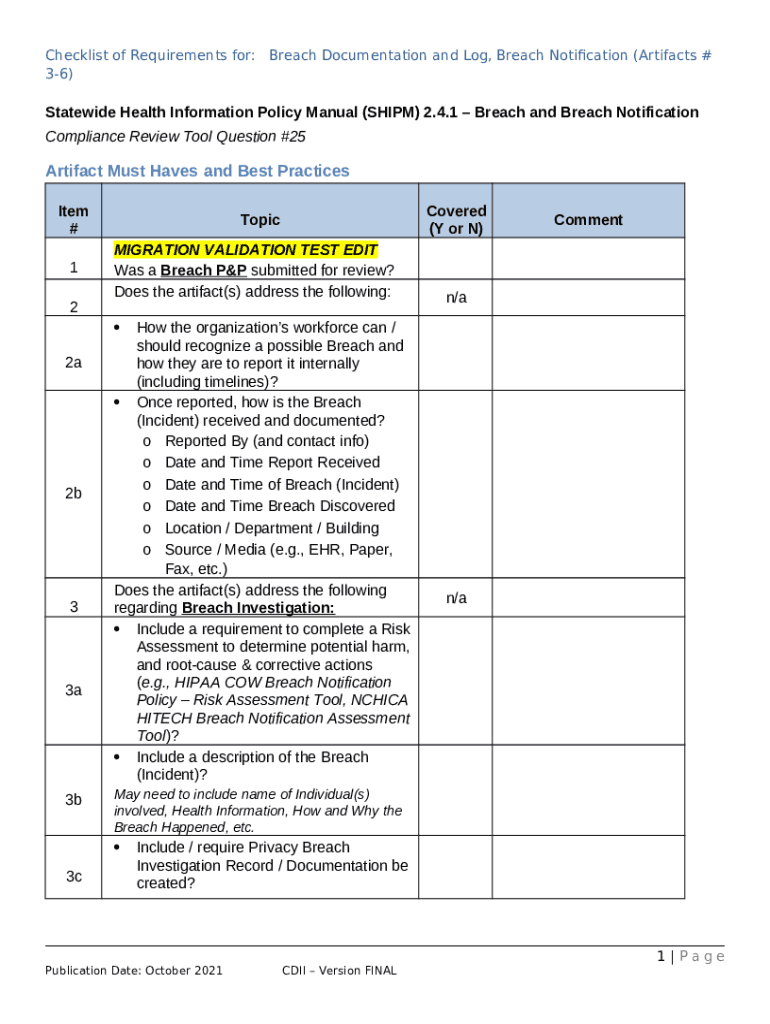
What is Breach Documentation and Log, Breach Notification ( ... Form?
The Breach Documentation and Log, Breach Notification ( ... is a Word document needed to be submitted to the specific address in order to provide certain information. It has to be filled-out and signed, which is possible manually in hard copy, or by using a certain software like PDFfiller. This tool allows to fill out any PDF or Word document directly from your browser (no software requred), customize it according to your needs and put a legally-binding electronic signature. Right after completion, the user can send the Breach Documentation and Log, Breach Notification ( ... to the appropriate individual, or multiple recipients via email or fax. The editable template is printable as well from PDFfiller feature and options offered for printing out adjustment. Both in digital and physical appearance, your form should have a neat and professional appearance. Also you can save it as the template for later, without creating a new document from scratch. You need just to edit the ready document.
Instructions for the form Breach Documentation and Log, Breach Notification ( ...
Once you're about filling out Breach Documentation and Log, Breach Notification ( ... form, remember to prepared enough of information required. This is a very important part, since some typos may trigger unwanted consequences beginning from re-submission of the whole entire word form and filling out with missing deadlines and even penalties. You should be observative filling out the figures. At a glimpse, you might think of it as to be quite easy. Nonetheless, it's easy to make a mistake. Some use such lifehack as storing everything in another file or a record book and then insert it's content into sample documents. Anyway, come up with all efforts and present valid and correct data with your Breach Documentation and Log, Breach Notification ( ... word template, and check it twice during the filling out the required fields. If it appears that some mistakes still persist, you can easily make some more corrections when you use PDFfiller editor and avoid missing deadlines.
How to fill out Breach Documentation and Log, Breach Notification ( ...
To start submitting the form Breach Documentation and Log, Breach Notification ( ..., you will need a template of it. When using PDFfiller for filling out and submitting, you can find it in several ways:
- Look for the Breach Documentation and Log, Breach Notification ( ... form in PDFfiller’s filebase.
- Upload the available template with your device in Word or PDF format.
- Create the writable document from scratch in PDF creation tool adding all required objects via editor.
No matter what choice you prefer, you'll get all the editing tools under your belt. The difference is that the template from the library contains the required fillable fields, you will need to add them by yourself in the second and third options. Yet, it is quite easy and makes your form really convenient to fill out. The fields can be placed on the pages, as well as deleted. There are many types of these fields based on their functions, whether you enter text, date, or place checkmarks. There is also a electronic signature field if you need the writable document to be signed by other people. You also can sign it yourself via signing feature. Once you're done, all you have to do is press the Done button and proceed to the submission of the form.