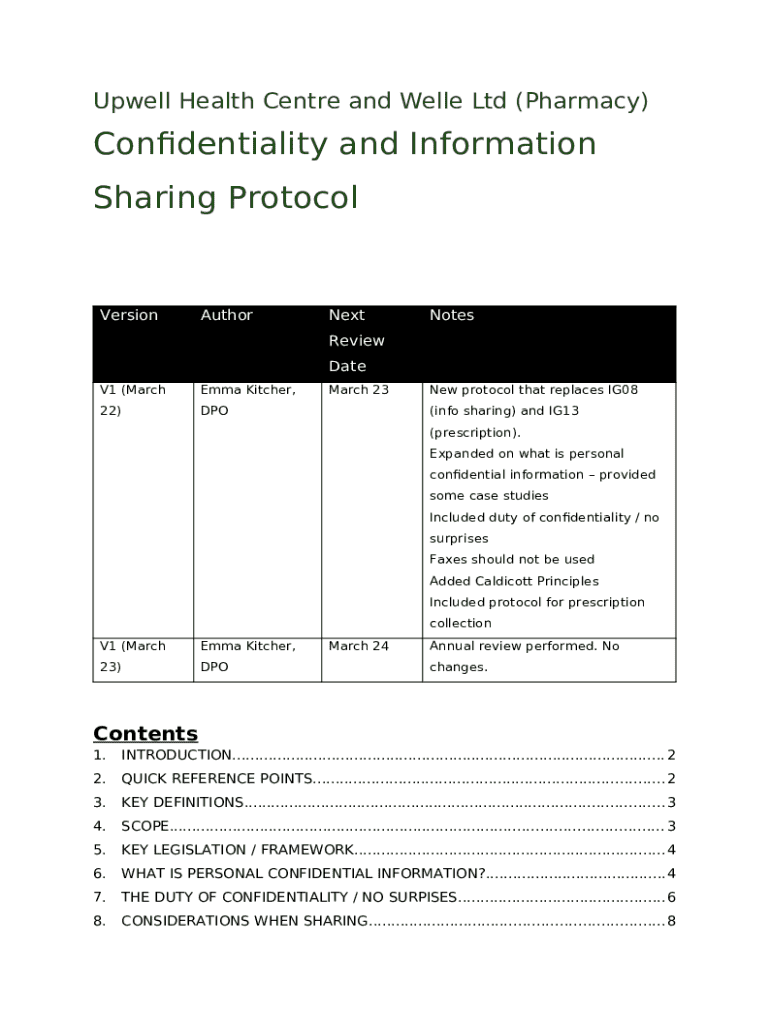
Confidentiality and information sharing form: A comprehensive how-to guide
Understanding confidentiality and information sharing
Confidentiality refers to the obligation to protect personally identifiable information or proprietary material from unauthorized access and disclosure. In various environments, whether business or personal, safeguarding sensitive information builds trust and ensures compliance with legal and ethical standards. A confidentiality and information sharing form establishes parameters around what can and cannot be disclosed, serving as a critical tool in any organization’s risk management strategy.
Definition of Confidential Information: This includes any data that is not publicly available, which might harm an individual or organization if disclosed.
Importance in Business Context: Confidentiality protects trade secrets, enhances client trust, and overall supports competitive advantage.
Overview of Information Sharing: While sharing information can promote collaboration and innovation, it presents risks such as data breaches and loss of intellectual property.
Types of confidentiality agreements
Different types of confidentiality agreements cater to diverse needs. The most common is the Non-Disclosure Agreement (NDA), which prevents parties from sharing sensitive information. NDAs vary in terms; some are mutual, meaning both parties are bound, while others are unilateral, binding only one party. Confidentiality agreements can also be embedded in employment contracts, which delineate employees’ obligations to protect the company's trade secrets and other proprietary information.
Non-Disclosure Agreement (NDA): Essential for collaborations and investments, crucial in defining confidentiality obligations.
Confidentiality Agreements in Employment Contracts: Vital for ensuring that employees do not disclose sensitive corporate data.
Specific Uses: Tailored agreements in industries such as healthcare, where patient information confidentiality is mandated by law.
Key elements of a confidentiality and information sharing form
A robust confidentiality and information sharing form consists of several key elements that clarify the expectations and obligations of all parties involved. Essential clauses ensure that confidentiality parameters are well understood and legally binding. Commonly included sections cover definitions of what constitutes confidential information, obligations of each party regarding that information, and the duration for which confidentiality must be maintained.
Definitions of Confidential Information: Clear demarcation of what materials are deemed confidential.
Obligations of the Parties: Defines the responsibilities of each party concerning the handling of confidential information.
Duration of Confidentiality: Specifies the length of time that confidentiality must be preserved.
Permitted Disclosures: Outlines under what circumstances information may be shared, such as legal requirements.
How to create a confidentiality and information sharing form
Creating an effective confidentiality and information sharing form requires careful consideration of the specific needs and context of the information being protected. Start by identifying the purpose of the agreement, clarifying why the information needs to be safeguarded. Then, ensure that confidential information is defined explicitly to avoid ambiguity. Following this, outline the rights and responsibilities of each party and determine how long the agreement will remain in effect.
Identify the Purpose: Clearly define the intent behind sharing the information.
Define Confidential Information Clearly: Use precise language to describe the information that requires protection.
Outline Rights and Responsibilities: Specify what each party can and cannot do with the confidential materials.
Specify the Duration: State how long the confidentiality obligations are active.
Include Additional Provisions: Consider clauses regarding the return of materials post-agreement.
Use Our Interactive Template Tool for Customization: Leverage pdfFiller’s tools to facilitate the process.
Filling out the confidentiality and information sharing form
Completing the confidentiality and information sharing form accurately ensures that all parties are aligned with the terms of the agreement. Start with entering the names and relevant details of the parties involved. Next, detail the nature of the confidential information being shared to establish clarity. Clearly outline the expectations and obligations of each party within the document to avoid misunderstandings. Lastly, it's critical to review the completed agreement with legal counsel to ensure compliance with applicable laws and best practices.
Entering the Parties' Information: Clearly list all parties’ names and contact details.
Detailing the Nature of the Confidential Information: Describe what information is to be kept confidential.
Outlining Specific Obligations: Define what each party must do to protect the confidentiality.
Review with Legal Counsel: Ensure that the agreement meets all necessary legal criteria.
Best practices for managing confidentiality agreements
Effective management of confidentiality agreements can mitigate the risk of breaches and ensure that all participants are adhering to their obligations. Regularly reviewing and updating your agreements will help to keep pace with changing laws and organizational needs. Additionally, securing digital copies of agreements using cloud-based storage solutions offers added protection and facilitates easy access for authorized personnel. Empowering staff through training on the significance of confidentiality and best practices ensures everyone understands their responsibilities.
Regular Review and Updating of Agreements: Regular evaluations help maintain legal compliance.
Securing Digital Copies: Use cloud solutions to protect and manage document access.
Strategies for Enforcing Confidentiality: Create systems to monitor adherence and address breaches proactively.
Training Teams: Periodic trainings on policies foster an informed organizational culture.
Challenges in information sharing and how to overcome them
Navigating the landscape of information sharing is fraught with challenges, particularly around balancing the need for transparency with the necessity of maintaining confidentiality. Avoiding breaches of agreement requires rigorous adherence to the defined terms, and it is important to understand the legal consequences of mishandling confidential information. Organizations must develop clear policies and employ technology solutions that enhance both security and oversight.
Balancing Transparency and Confidentiality: Find a middle ground to foster collaboration without compromising data.
Avoiding Breaches of Agreement: Reinforce the importance of compliance among all involved parties.
Legal Consequences: Educate teams about potential repercussions of breaches to enhance awareness.
Interactive tools available on pdfFiller
pdfFiller provides users with an array of powerful tools to facilitate the customization and management of their confidentiality and information sharing forms. The pdfFiller Document Editor allows for seamless editing, ensuring that documents align with specific needs. Users can take advantage of eSigning features to secure the legal validity of agreements while maintaining a secure environment. Collaboration tools enable teams to work collectively while easily tracking and managing document versions, providing clarity and organization throughout all stages of document handling.
Utilizing the pdfFiller Document Editor: Easily create and format confidentiality agreements.
eSigning Features: Ensure legal validity while keeping documents secure.
Collaboration Tools: Enable team participation in document editing and revision processes.
Tracking and Management of Document Versions: Stay organized with version control, ensuring all parties access the latest documents.
Frequently asked questions (FAQs)
Addressing common questions surrounding confidentiality agreements can provide clarity for potential signers. For instance, if a confidentiality agreement is breached, it is crucial to consult legal counsel for appropriate recourse. Furthermore, these agreements can often be enforceable post-employment, depending on the terms outlined within the agreement. Lastly, organizations must have protocols in place to manage compelled disclosure requests, ensuring compliance with legal standards while protecting sensitive information.
What to do if a confidentiality agreement is breached? Consult legal counsel to discuss potential remedies.
Can confidentiality agreements be enforced post-employment? Yes, depending on the agreement's terms.
How to handle compelled disclosure requests? Have clear procedures in place to balance obligations.
Real-life applications of confidentiality agreements
Examining real-life examples underscores the importance of confidentiality agreements across diverse industries. For instance, in the healthcare sector, patient confidentiality is safeguarded by federal legislation like HIPAA, which mandates strict adherence to privacy protocols. In the technology field, companies often rely on NDAs when sharing innovative ideas to protect intellectual property. Learning from instances of breaches helps organizations refine their practices, ensuring better compliance and better mechanisms to thwart unauthorized disclosures.
Case Studies: Analyze successful implementations in various industries to understand best practices.
Lessons Learned from Breaches: Review incidents of data breaches to identify vulnerabilities.
Best Practices for Prevention: Develop strategies informed by past challenges to mitigate future risks.