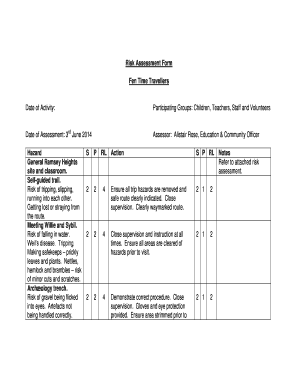
What is Threat And Risk Assessment Template?
A Threat And Risk Assessment Template is a document that helps organizations identify and assess potential threats and risks to their assets, operations, and information. It provides a structured framework for evaluating the likelihood and impact of various threats and risks, allowing organizations to prioritize and implement appropriate mitigation measures.
What are the types of Threat And Risk Assessment Template?
There are several types of Threat And Risk Assessment Templates available, designed to cater to different industries and organizational needs. Some common types include:
Physical Threat And Risk Assessment Template: Used to assess potential physical threats such as natural disasters, security breaches, or accidents.
Cybersecurity Threat And Risk Assessment Template: Focuses on evaluating cybersecurity risks associated with data breaches, hacking attempts, or system vulnerabilities.
Financial Threat And Risk Assessment Template: Helps organizations assess potential financial risks, such as economic downturns, market fluctuations, or financial fraud.
Operational Threat And Risk Assessment Template: Used to evaluate operational risks related to business processes, supply chain disruptions, or equipment failures.
How to complete Threat And Risk Assessment Template
Completing a Threat And Risk Assessment Template involves the following steps:
01
Identify assets: Determine the assets or resources that are important to your organization.
02
Identify threats: Identify potential threats that could harm or impact your assets.
03
Assess vulnerabilities: Evaluate the vulnerabilities or weaknesses in your organization that could be exploited by threats.
04
Determine likelihood and impact: Determine the likelihood and impact of each threat on your assets.
05
Prioritize risks: Prioritize the risks based on their likelihood and impact.
06
Develop mitigation strategies: Create strategies to mitigate or minimize the identified risks.
07
Implement and monitor mitigation measures: Implement the mitigation strategies and regularly monitor their effectiveness.
08
Review and update: Regularly review and update the Threat And Risk Assessment Template to ensure its relevancy and accuracy.
pdfFiller empowers users to create, edit, and share documents online. Offering unlimited fillable templates and powerful editing tools, pdfFiller is the only PDF editor users need to get their documents done.