PKI Byline For Free




Users trust to manage documents on pdfFiller platform
Watch a short video walkthrough on how to add an PKI Byline
pdfFiller scores top ratings in multiple categories on G2
Add a legally-binding PKI Byline with no hassle
pdfFiller enables you to handle PKI Byline like a pro. Regardless of the platform or device you run our solution on, you'll enjoy an intuitive and stress-free method of executing documents.
The whole pexecution process is carefully protected: from adding a file to storing it.
Here's the best way to generate PKI Byline with pdfFiller:
Select any available way to add a PDF file for signing.
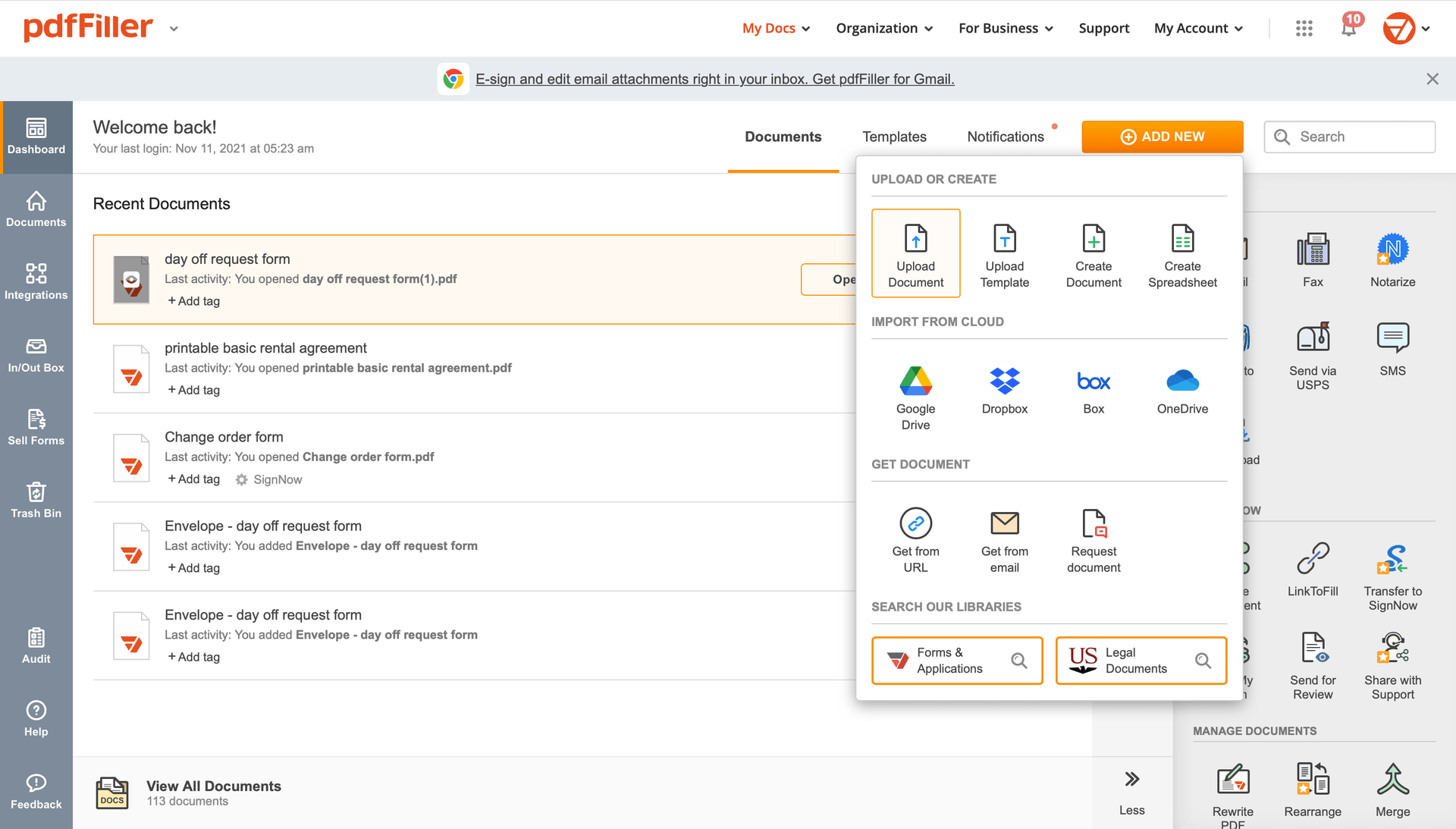
Use the toolbar at the top of the page and choose the Sign option.
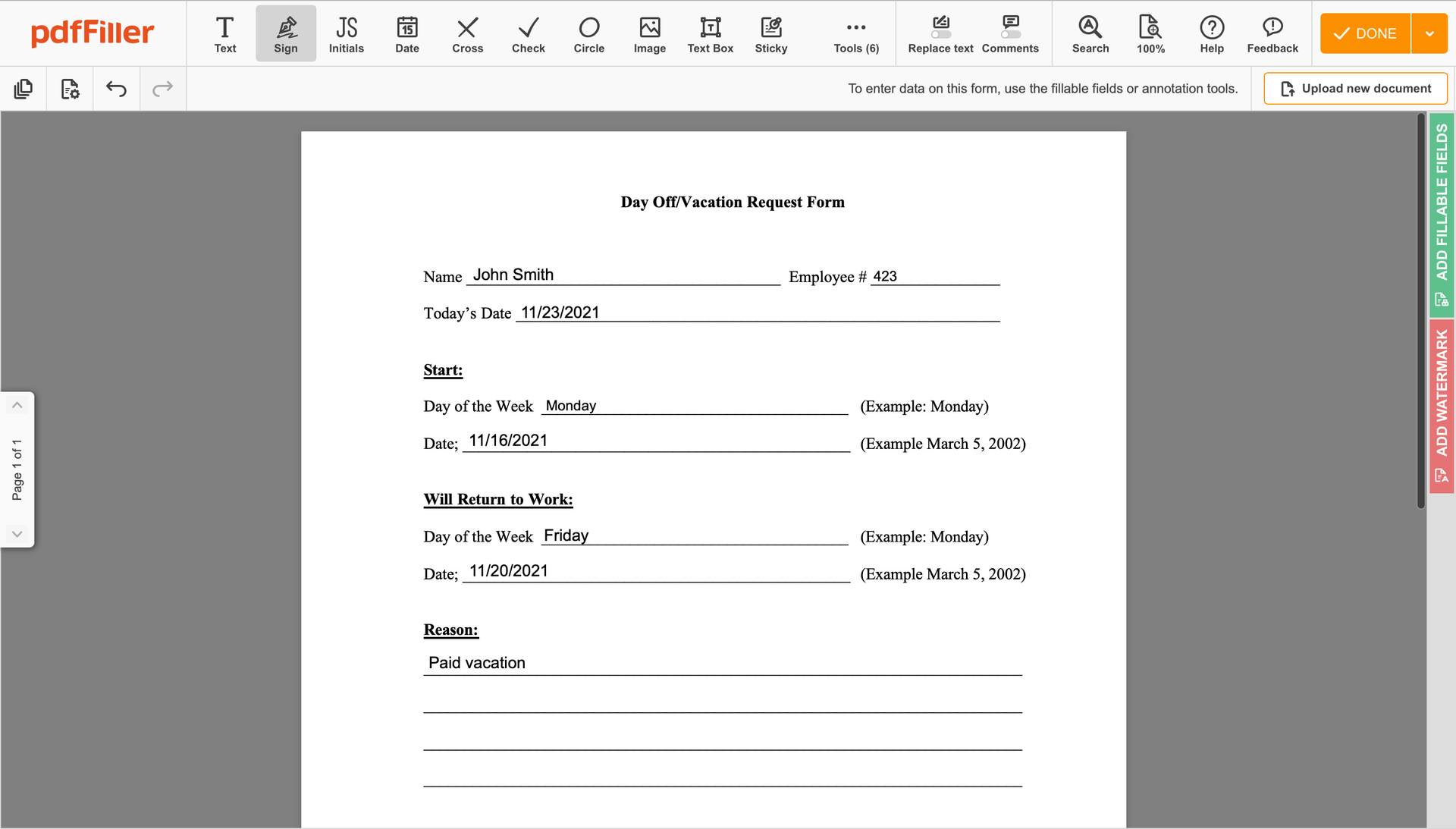
You can mouse-draw your signature, type it or add an image of it - our solution will digitize it automatically. As soon as your signature is created, hit Save and sign.
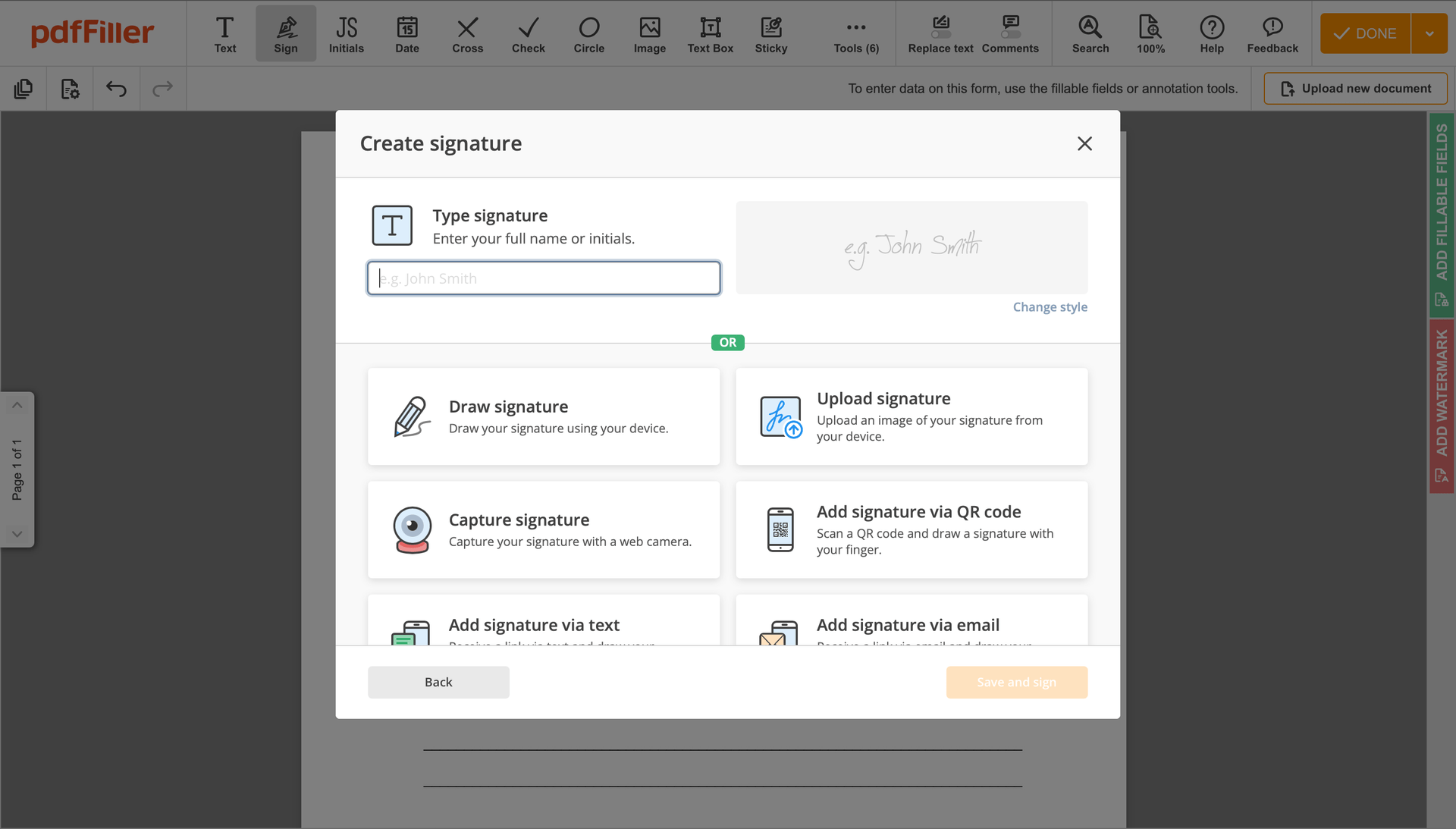
Click on the form area where you want to put an PKI Byline. You can move the newly created signature anywhere on the page you want or change its configurations. Click OK to save the adjustments.
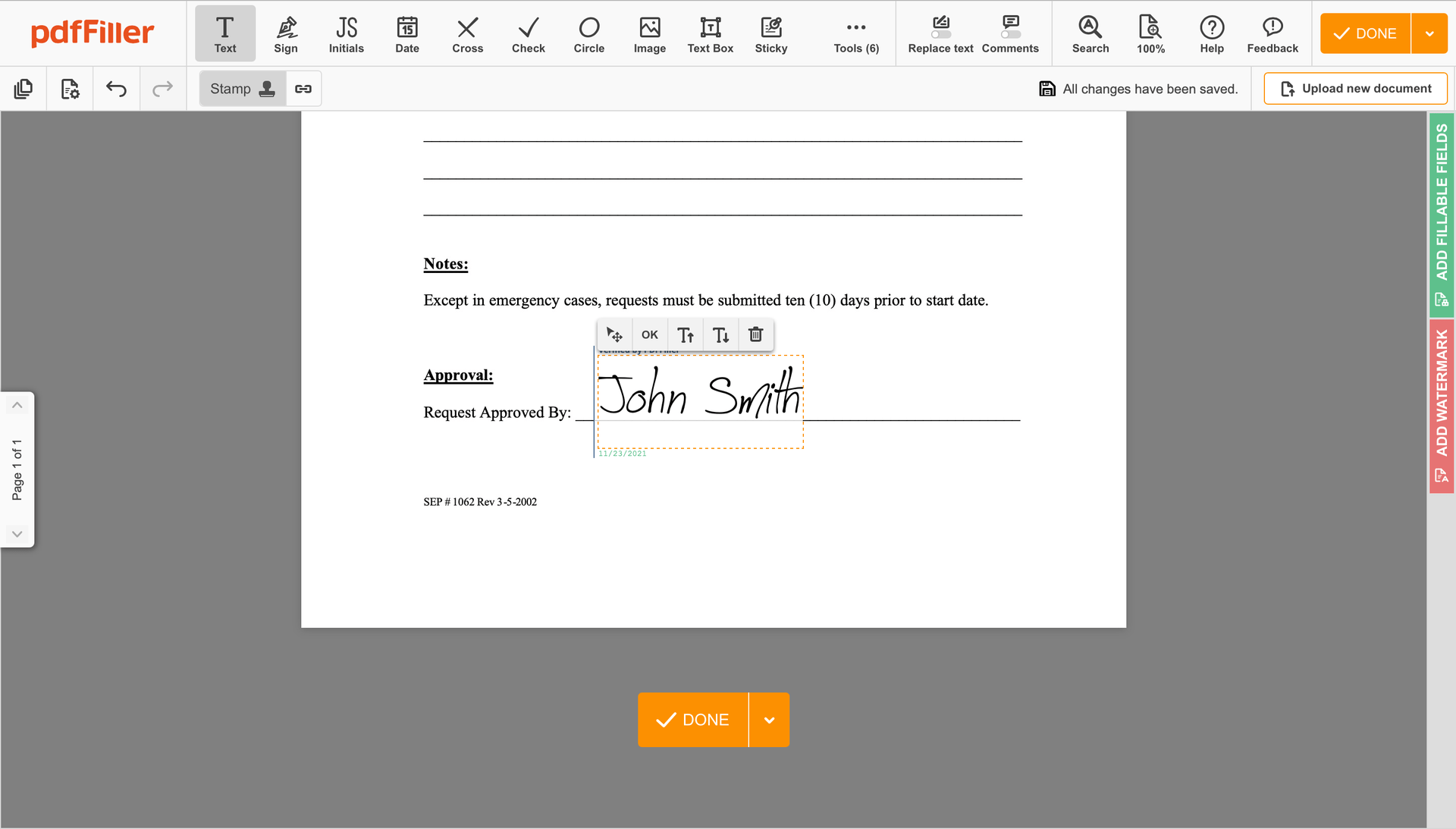
Once your form is good to go, hit the DONE button in the top right corner.
Once you're done with signing, you will be redirected to the Dashboard.
Utilize the Dashboard settings to get the completed copy, send it for further review, or print it out.
Still using different applications to manage and edit your documents? Try this all-in-one solution instead. Use our document management tool for the fast and efficient work flow. Create fillable forms, contracts, make document template sand more features, without leaving your account. Plus, you can use PKI Byline and add unique features like orders signing, reminders, attachment and payment requests, easier than ever. Get the value of full featured tool, for the cost of a lightweight basic app. The key is flexibility, usability and customer satisfaction.
How to edit a PDF document using the pdfFiller editor:
How to Send a PDF for eSignature
What our customers say about pdfFiller

















