SOC Signature Block For Free




Users trust to manage documents on pdfFiller platform
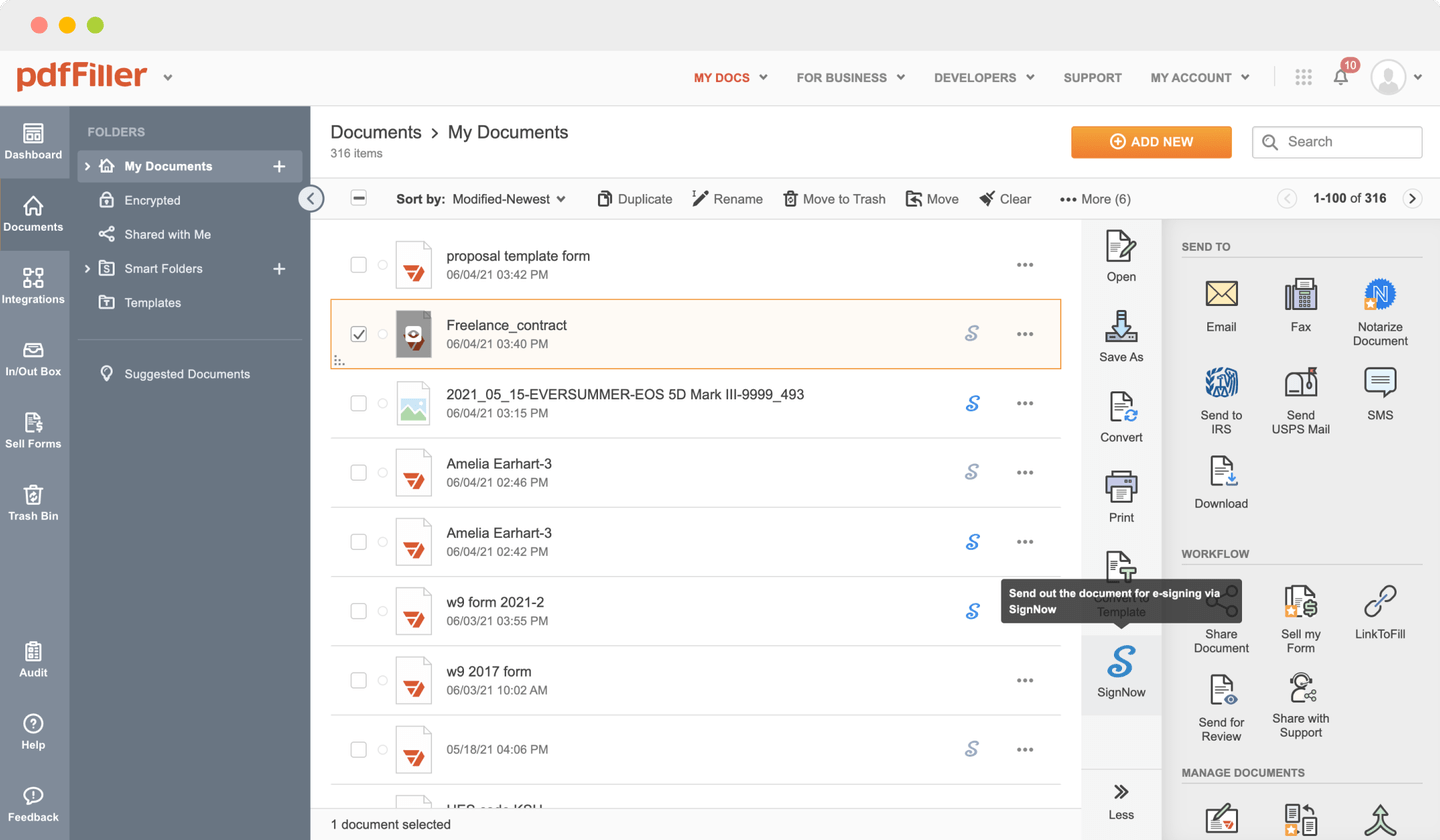
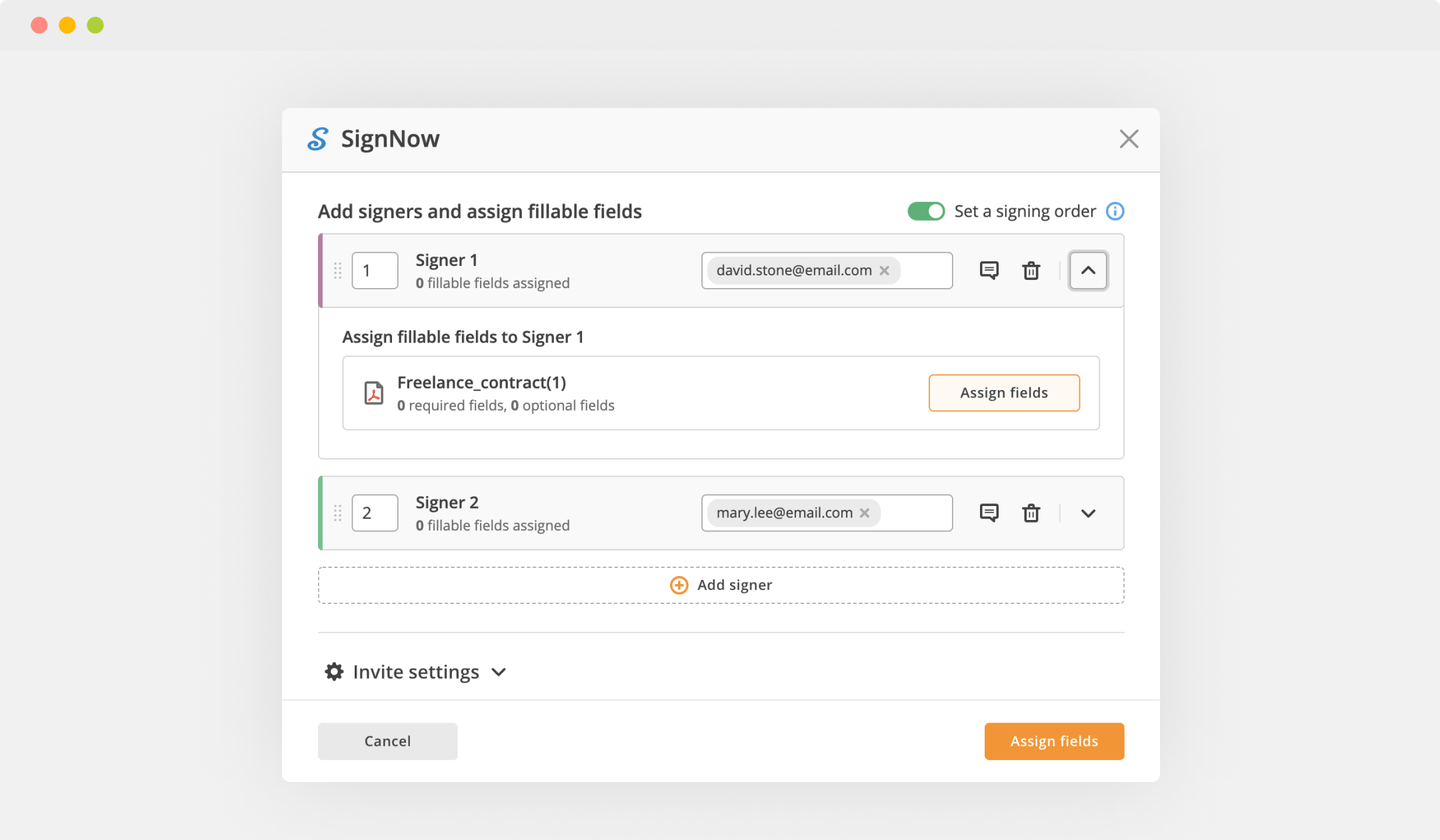
Send documents for eSignature with signNow
Watch a short video walkthrough on how to add an SOC Signature Block
pdfFiller scores top ratings in multiple categories on G2
Create a legally-binding SOC Signature Block with no hassle
pdfFiller enables you to deal with SOC Signature Block like a pro. No matter the platform or device you run our solution on, you'll enjoy an user-friendly and stress-free way of executing documents.
The whole pexecution flow is carefully protected: from uploading a document to storing it.
Here's the best way to create SOC Signature Block with pdfFiller:
Choose any available option to add a PDF file for signing.
Utilize the toolbar at the top of the interface and choose the Sign option.
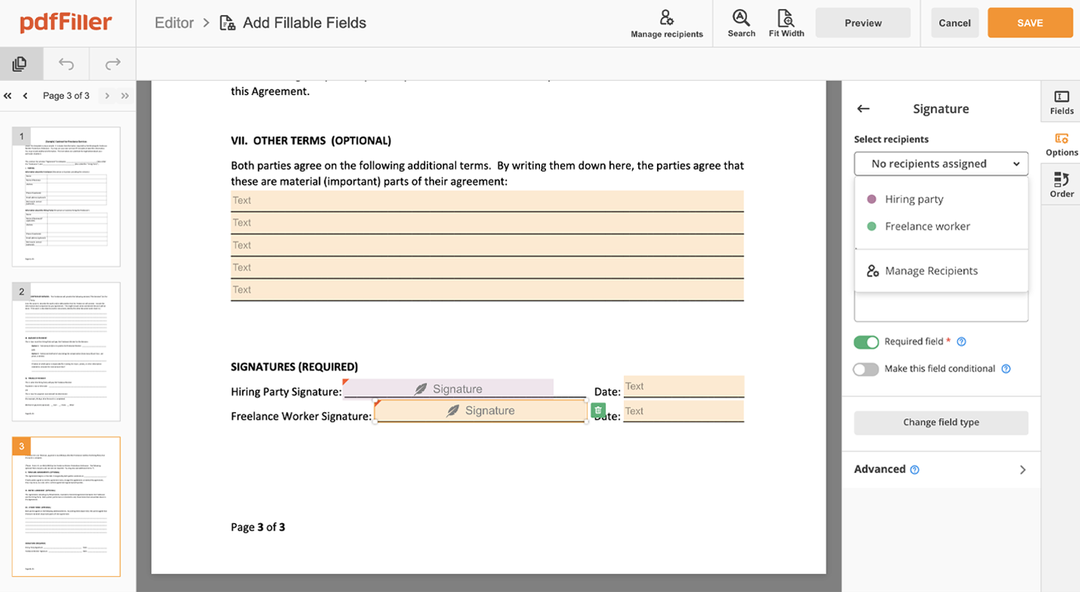
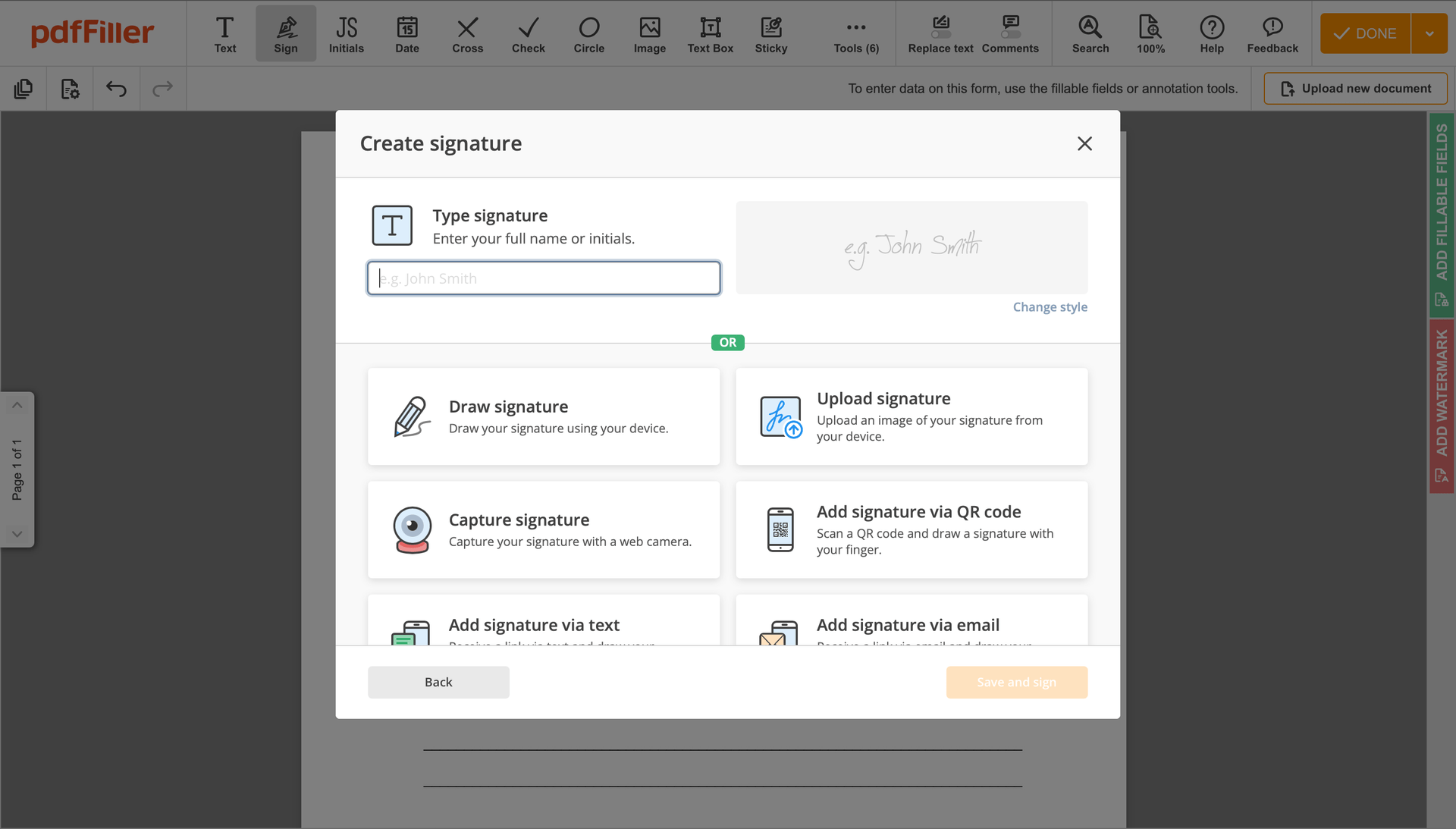
You can mouse-draw your signature, type it or upload a photo of it - our solution will digitize it in a blink of an eye. As soon as your signature is set up, hit Save and sign.
Click on the form place where you want to put an SOC Signature Block. You can move the newly created signature anywhere on the page you want or change its settings. Click OK to save the changes.
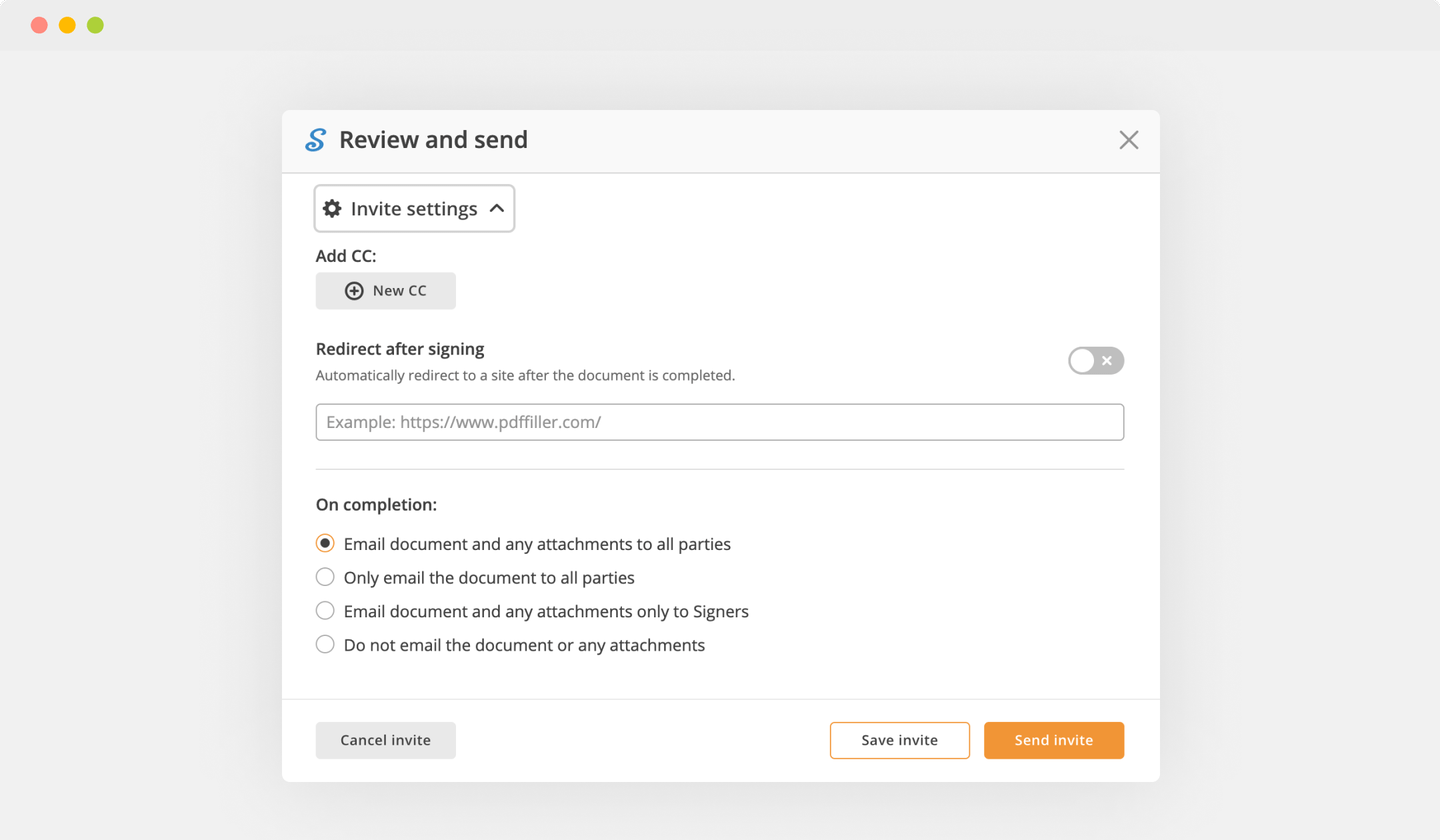
Once your document is all set, hit the DONE button in the top right corner.
As soon as you're done with certifying your paperwork, you will be taken back to the Dashboard.
Utilize the Dashboard settings to download the executed form, send it for further review, or print it out.
Stuck with different applications for creating and signing documents? Use this solution instead. Document management becomes simpler, fast and smooth using our editor. Create document templates from scratch, modify existing form sand many more useful features, within one browser tab. You can use SOC Signature Block directly, all features, like orders signing, alerts, requests , are available instantly. Have the value of full featured tool, for the cost of a lightweight basic app. The key is flexibility, usability and customer satisfaction. We deliver on all three.
How to edit a PDF document using the pdfFiller editor:
How to Send a PDF for eSignature
What our customers say about pdfFiller