Protected Recommended Field Certificate मुफ़्त में
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

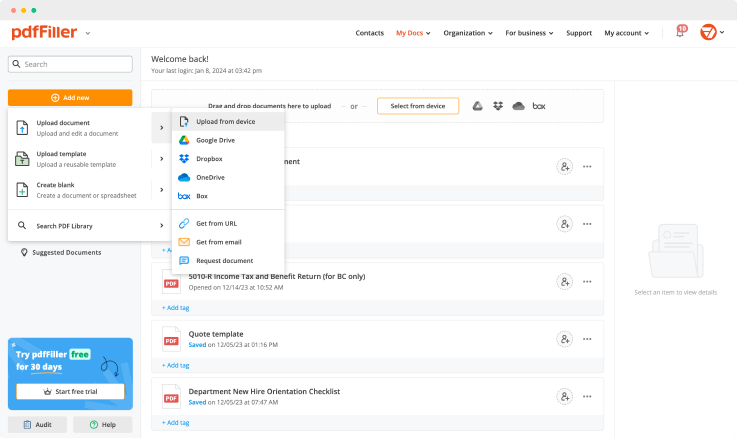
Upload a document

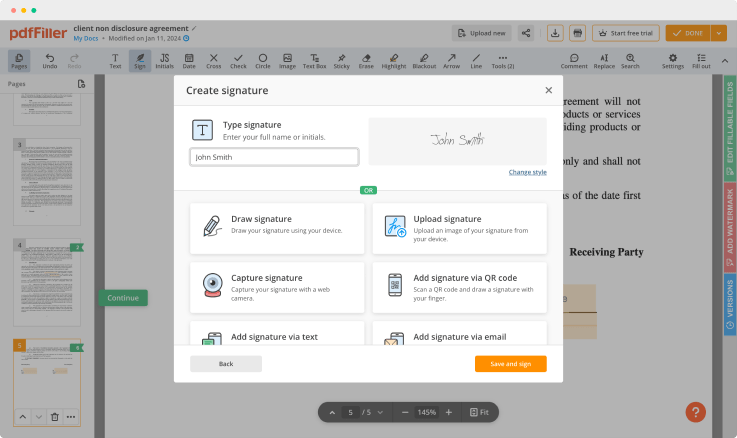
Generate your customized signature

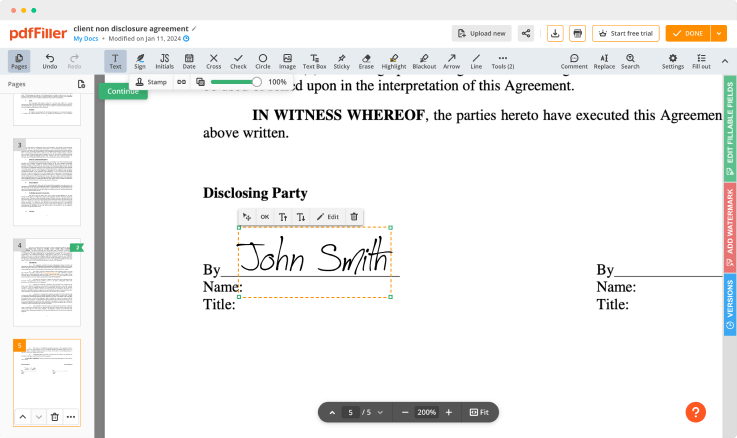
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Protected Recommended Field Certificate
The Protected Recommended Field Certificate is your reliable solution for ensuring secure and compliant operations in your fieldwork. With this feature, you can confidently validate and manage recommendations while protecting sensitive information.
Key Features
Ensures data integrity and security
Streamlines compliance with industry standards
Facilitates seamless sharing of recommendations
Provides real-time updates and notifications
Supports easy integration with existing workflows
Potential Use Cases and Benefits
Ideal for industries needing strict adherence to regulations, such as agriculture and environmental services
Helps organizations maintain professional credibility through transparent documentation
Enhances collaboration among teams by providing a centralized reference for recommendations
Reduces the risk of data breaches with advanced encryption and access controls
Improves efficiency by minimizing time spent on manual data entry and verification
By implementing the Protected Recommended Field Certificate, you can address common challenges like compliance risks, data security, and inefficiencies in documentation. This feature empowers you to focus on your core operations while ensuring that your recommendations are safe, secure, and easily accessible.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
Does radius require certificate?
RADIUS Server Requirements The server must host a certificate from a Certificate Authority (CA) trusted by clients on the network. The RADIUS server must have a user base to authenticate against.
How do I get a Radius server certificate?
0:12 2:53 Suggested clip How To Set up Radius Server :: Configuring Certificates — Part 2 of 4 YouTubeStart of suggested client of suggested clip How To Set up Radius Server :: Configuring Certificates — Part 2 of 4
How do I configure a Radius server certificate?
0:12 2:53 Suggested clip How To Set up Radius Server :: Configuring Certificates — Part 2 of 4 YouTubeStart of suggested client of suggested clip How To Set up Radius Server :: Configuring Certificates — Part 2 of 4
What is Radius server IP address?
The radius server IP is the IP address of the CIITIX-WiFi server and the port is always 1812 and the shared secret is the password you created when we were adding a NAS device.
How do I add a trusted certificate to NPS?
Click Computer account, and then click Next. In Select Computer, ensure that Local computer (the computer this console is running on) is selected, click Finish, and then click OK. In the left pane, double-click Certificates (Local Computer), and then double-click the Trusted Root Certification Authorities folder.
Does PEAK require certificate?
PEAK/MSCHAPv2 doesn't typically use client certificates, nor does it directly use any CA certificates in establishing a TLS connection (*see below). However, it certainly requires the use of a server certificate (PEAK is a TLS tunneled EAP protocol).
Is PEAK MSCHAPv2 secure?
If you are using PEAPv0 with EAP-MSCHAPv2 authentication then you should be secure as the MSCHAPv2 messages are sent through a TLS protected tunnel. If you would not use a protected tunnel, then you are indeed vulnerable.
What is PEAK credentials?
PEAK (Protected Extensible Authentication Protocol) is a version of EAP, the authentication protocol used in wireless networks and Point-to-Point connections. PEAK is designed to provide more secure authentication for 802.11 WLANs (wireless local area networks) that support 802.1X port access control.
Ready to try pdfFiller's? Protected Recommended Field Certificate मुफ़्त में
Upload a document and create your digital autograph now.