Protected Limited Field Paper For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
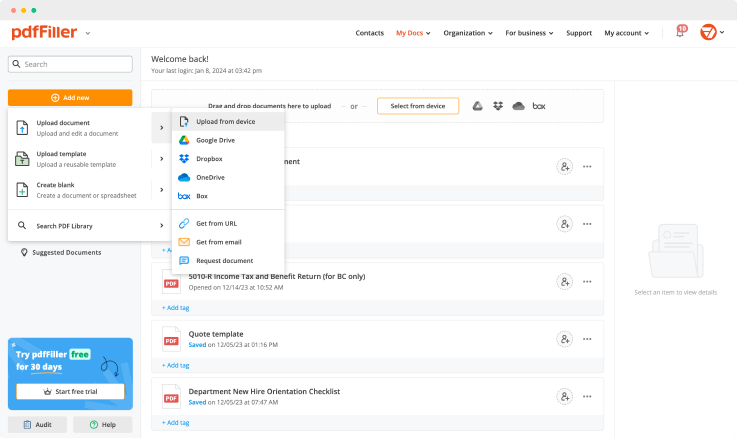
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

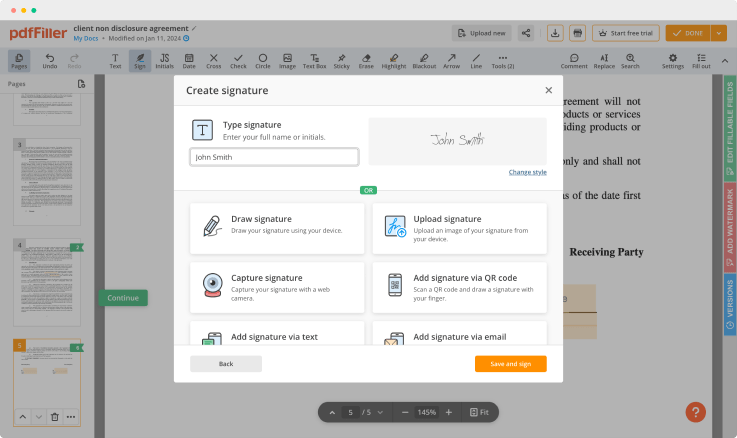
Generate your customized signature

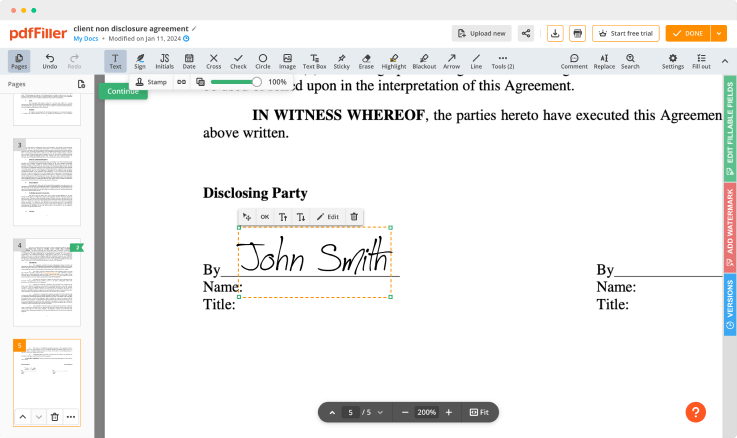
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Protected Limited Field Paper: Enhance Your Documentation Efficiency
Discover the benefits of Protected Limited Field Paper, designed to meet your documentation needs while ensuring data security and privacy. This product serves as a reliable solution for those who require controlled environments for sensitive information.
Key Features
Durable, high-quality material that withstands wear and tear
Limited access fields to protect sensitive data
Customizable options to fit specific requirements
User-friendly design for easy data entry
Compatible with various writing instruments
Potential Use Cases and Benefits
Ideal for medical professionals managing patient records
Perfect for legal documentation that requires confidentiality
Useful for businesses maintaining sensitive client information
Great for educational institutes handling student data
Suitable for researchers needing to protect proprietary information
By using Protected Limited Field Paper, you can effectively safeguard your important information from unauthorized access. This product simplifies your documentation process while keeping your data secure and organized. With its various applications across different industries, it addresses your need for confidentiality and efficiency.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What are the three rules of HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) regulations are divided into several major standards or rules: Privacy Rule, Security Rule, Transactions and Code Sets (TCS) Rule, Unique Identifiers Rule, Breach Notification Rule, Omnibus Final Rule, and the HITCH Act.
What are HIPAA rules?
The HIPAA Privacy Rule establishes national standards to protect individuals' medical records and other personal health information and applies to health plans, health care clearinghouses, and those health care providers that conduct certain health care transactions electronically.
What are the 4 main purposes of HIPAA?
What are the four main purposes of HIPAA? Privacy of health information, security of electronic records, administrative simplification, and insurance portability. Provides detailed instructions for handling a protecting a patient's personal health information.
What are HIPAA requirements?
The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance.
What are the 5 main components of HIPAA?
This addresses five main areas in regard to covered entities and business associates: Application of HIPAA security and privacy requirements. Establishment of mandatory federal privacy and security breach reporting requirements. Creation of new privacy requirements and accounting disclosure requirements and
What are the 3 rules of HIPAA?
HIPAA Rules and Regulations lay out three types of security safeguards required for compliance: administrative, physical, and technical. For each of these types, the Rule identifies security standards, and for each standard, it names both required and addressable implementation specifications.
What is the correct order of steps that must be taken if there is a breach of HIPAA information or data?
Stop the breach. Terminate improper access to PHI. Retrieve any PHI that was improperly disclosed. And obtain assurances from recipients that they have not used or disclosed the PHI, and/or will not, further use or disclose PHI that was improperly accessed. Document your actions and the recipient's response.
What is the correct order of steps that must be taken if there is a breach of HIPAA information or data?
Stop the breach. Terminate improper access to PHI. Retrieve any PHI that was improperly disclosed. And obtain assurances from recipients that they have not used or disclosed the PHI, and/or will not, further use or disclose PHI that was improperly accessed. Document your actions and the recipient's response.
Ready to try pdfFiller's? Protected Limited Field Paper
Upload a document and create your digital autograph now.