Cloud Security Trust Sign For Free




Join the world’s largest companies
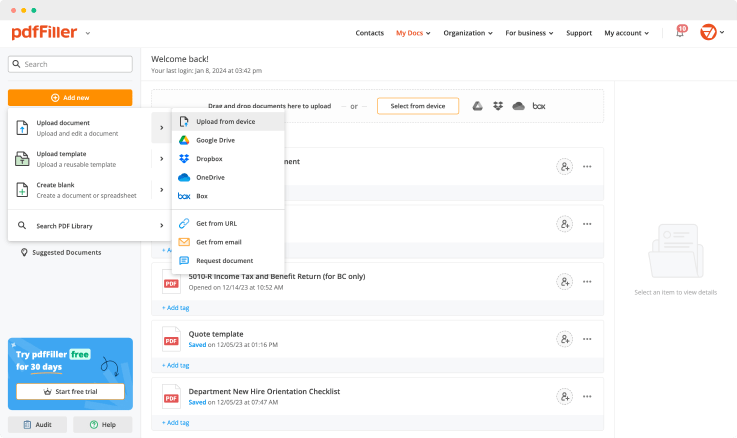
How to Send a PDF for eSignature









Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution

Unlimited document storage

Widely recognized ease of use

Reusable templates & forms library
The benefits of electronic signatures

Efficiency

Accessibility

Cost savings

Security

Legality

Sustainability
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance

SOC 2 Type II Certified

PCI DSS certification

HIPAA compliance

CCPA compliance
Cloud Security Trust Sign Feature
The Cloud Security Trust Sign feature enhances your cloud services by building trust and ensuring compliance throughout your organization. This feature simplifies the process of demonstrating adherence to industry standards and regulations, making your cloud security efforts more transparent.
Key Features
Potential Use Cases and Benefits
This feature addresses your concerns about cloud security and compliance by providing a structured approach to manage your security posture. With Cloud Security Trust Sign, you gain peace of mind knowing that you can demonstrate your commitment to security and compliance, reduce risks, and improve operational efficiency.
Add a legally-binding Cloud Security Trust Sign in minutes
pdfFiller enables you to deal with Cloud Security Trust Sign like a pro. No matter what platform or device you run our solution on, you'll enjoy an intuitive and stress-free method of executing paperwork.
The whole pexecution process is carefully safeguarded: from adding a file to storing it.
Here's how you can create Cloud Security Trust Sign with pdfFiller:
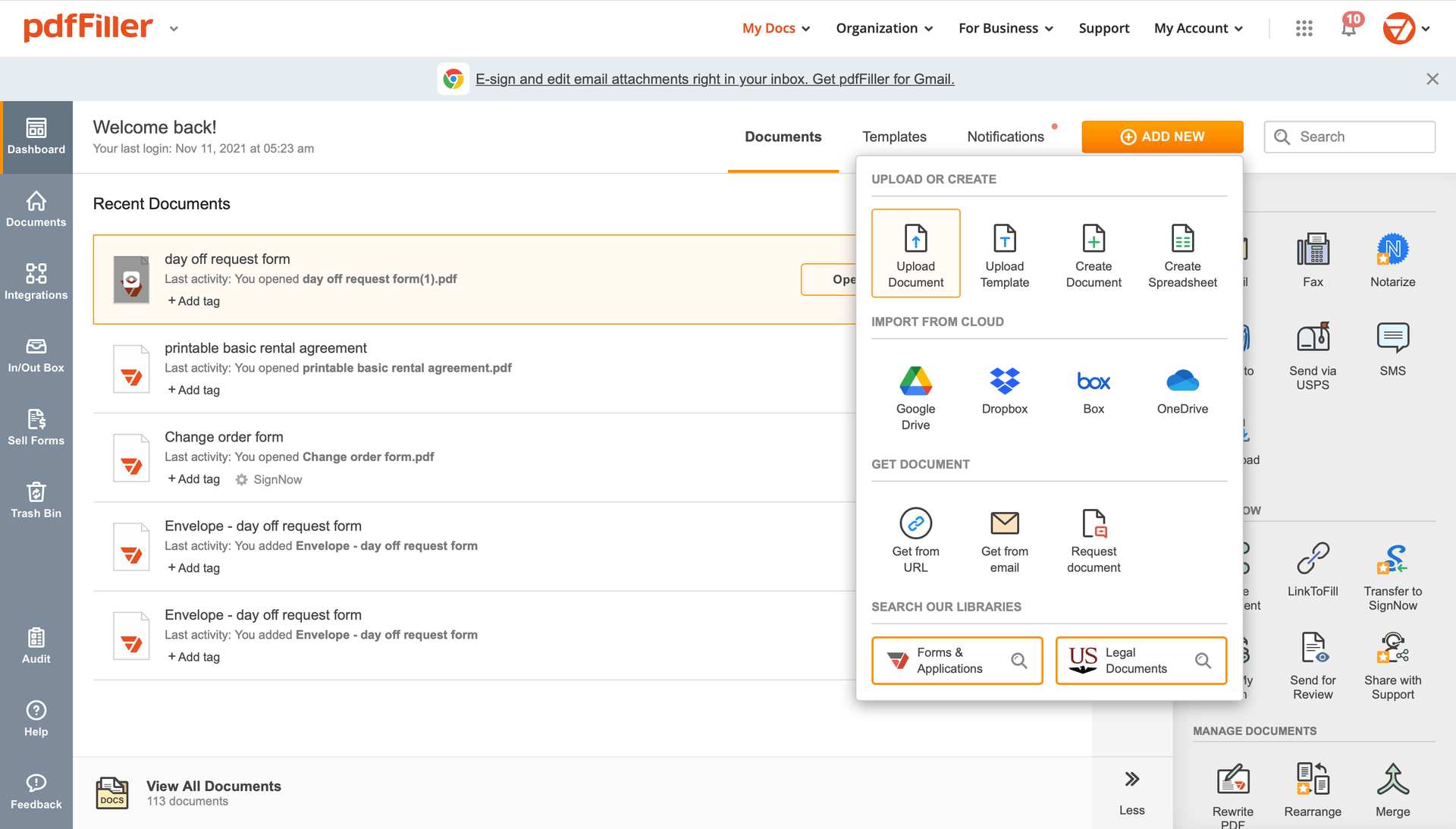
Choose any readily available way to add a PDF file for completion.
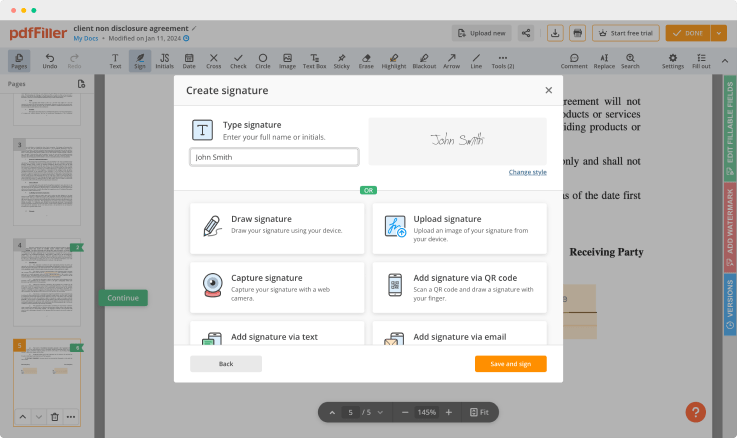
Utilize the toolbar at the top of the page and choose the Sign option.
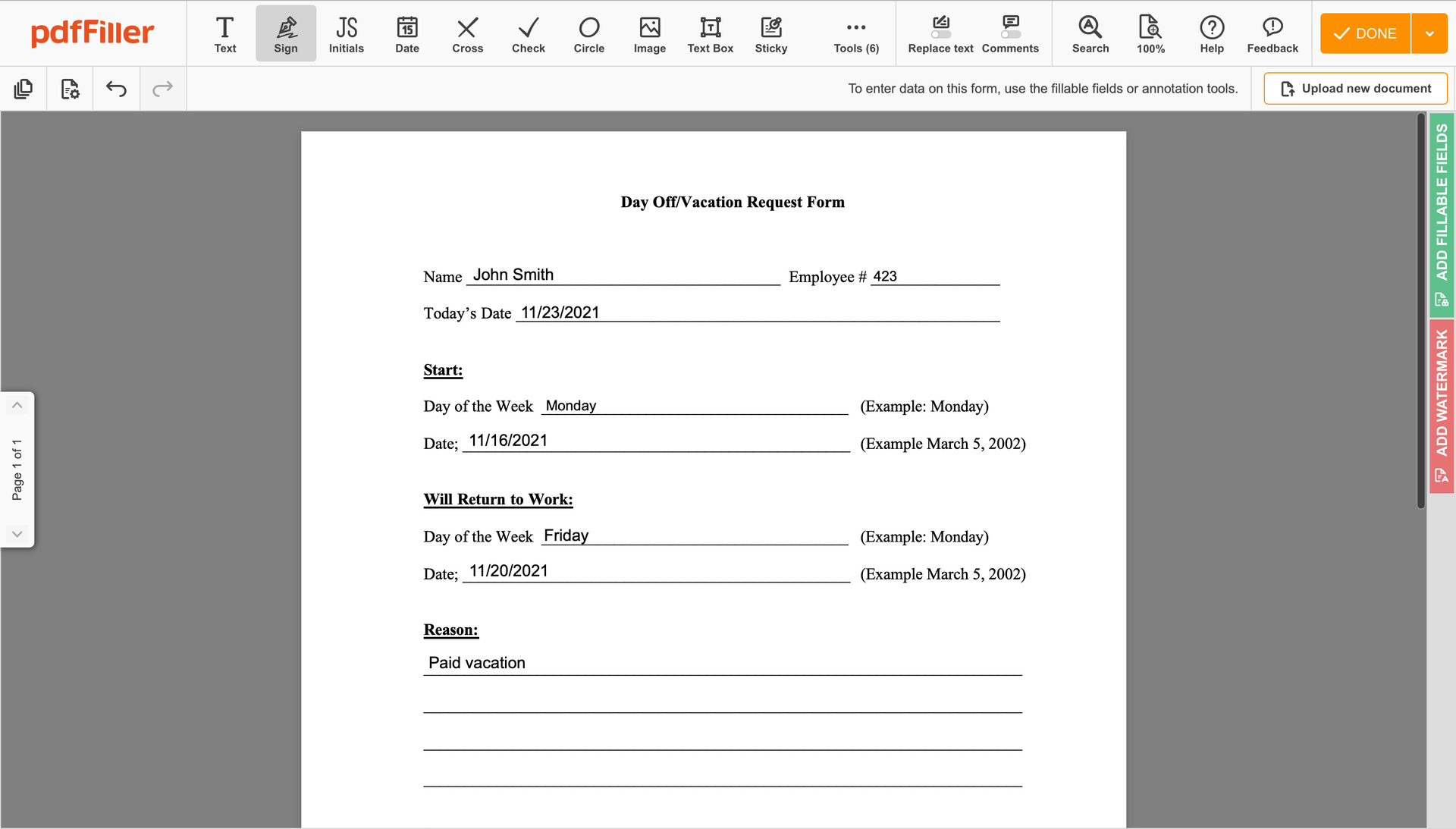
You can mouse-draw your signature, type it or upload an image of it - our solution will digitize it in a blink of an eye. Once your signature is set up, click Save and sign.
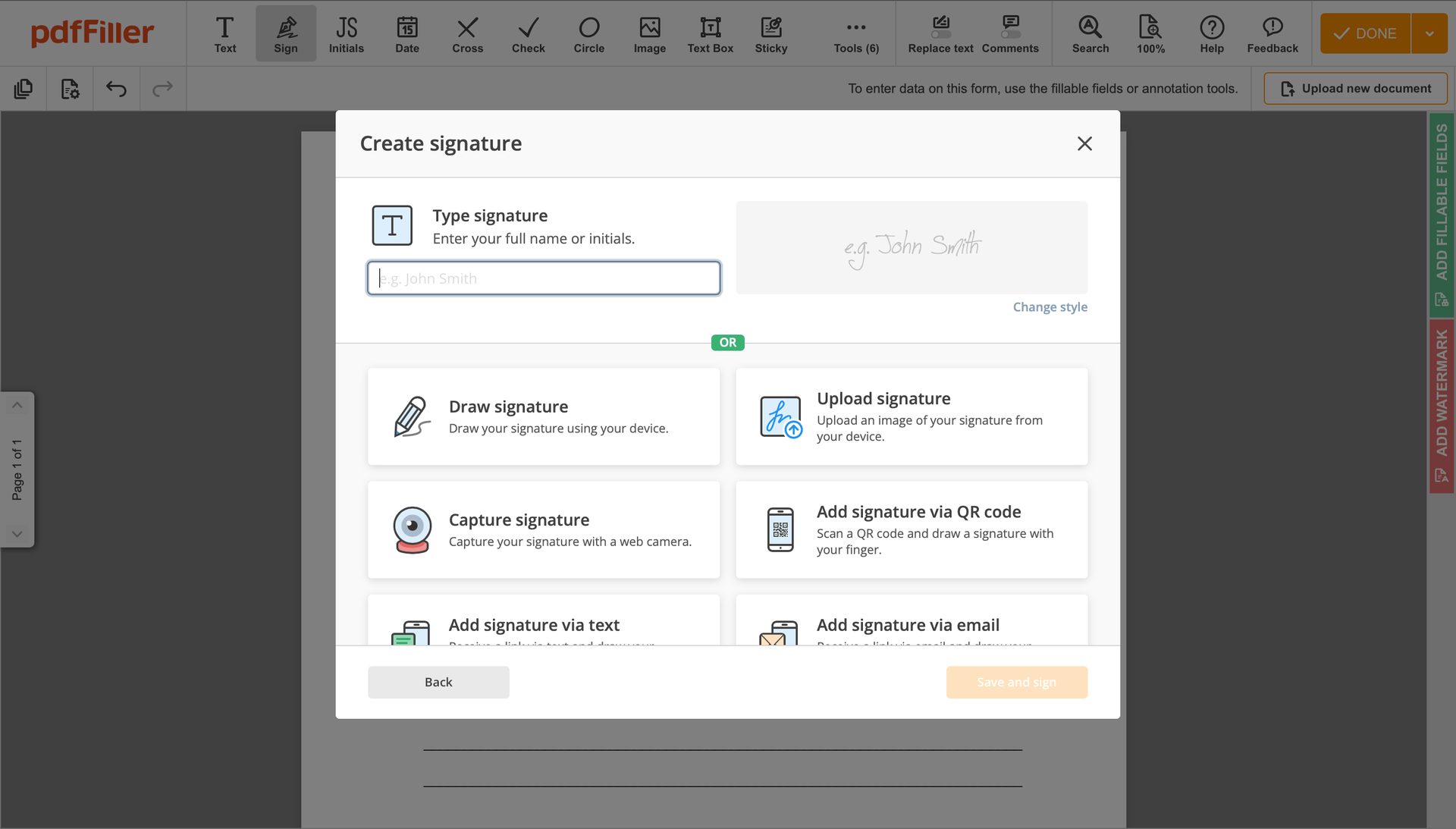
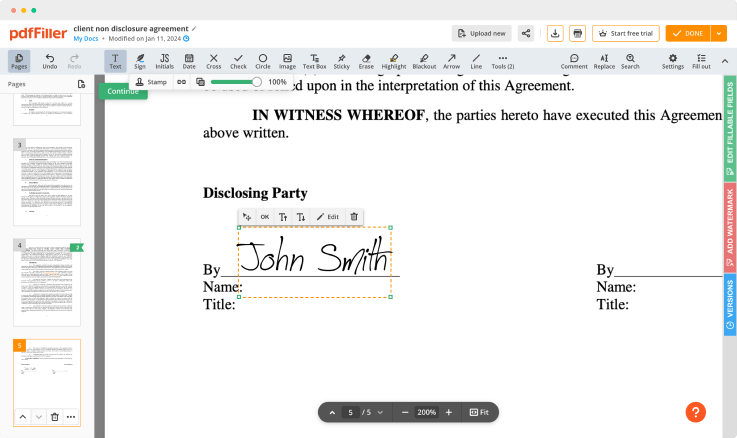
Click on the document place where you want to add an Cloud Security Trust Sign. You can move the newly created signature anywhere on the page you want or change its configurations. Click OK to save the adjustments.
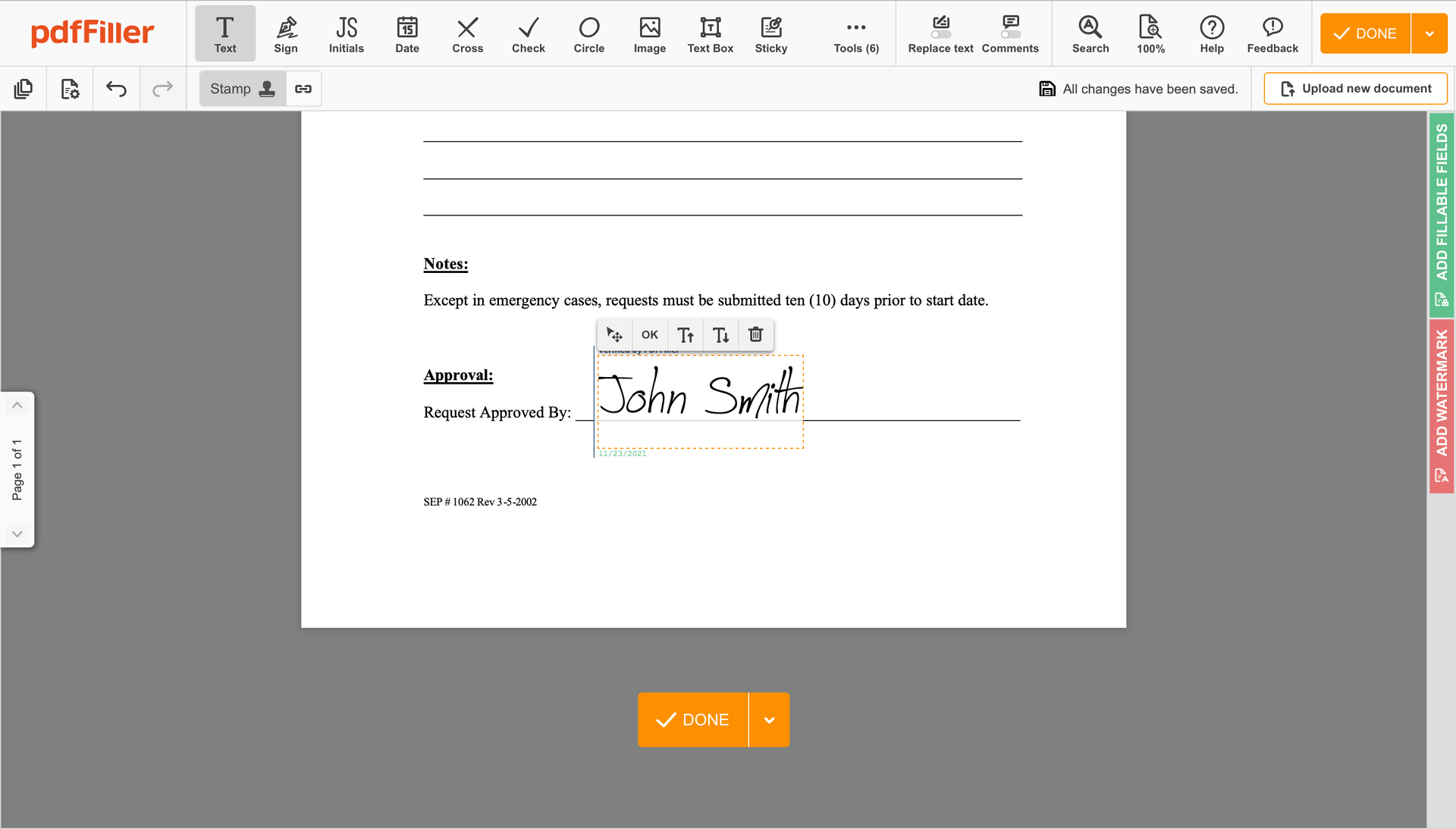
Once your form is ready to go, hit the DONE button in the top right area.
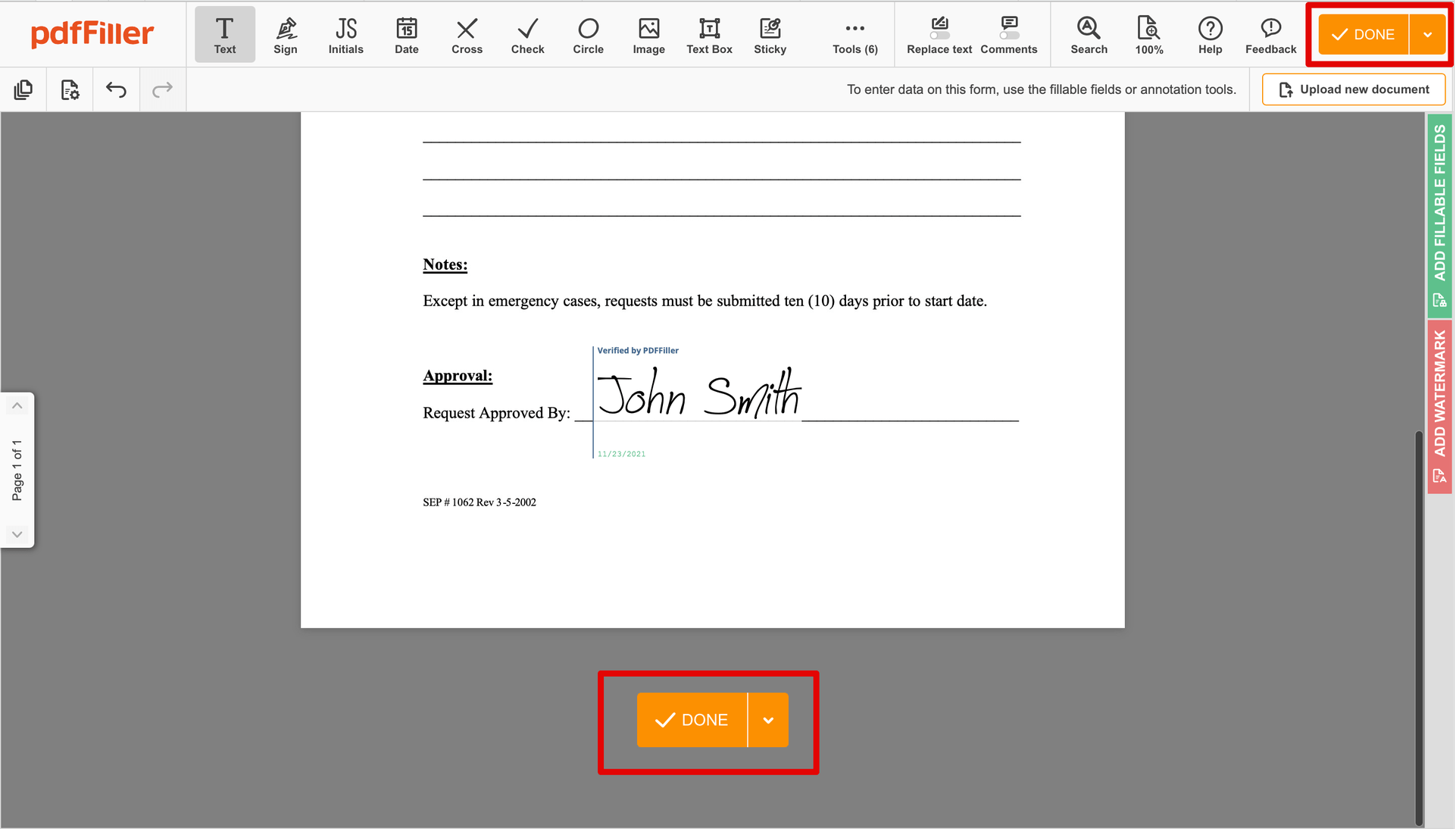
As soon as you're done with signing, you will be redirected to the Dashboard.
Use the Dashboard settings to download the executed form, send it for further review, or print it out.
Still using different programs to manage and edit your documents? We have an all-in-one solution for you. Document management is notably easier, faster and much smoother using our tool. Create fillable forms, contracts, make templates, integrate cloud services and other useful features within your browser. You can use Cloud Security Trust Sign right away, all features, like signing orders, alerts, requests , are available instantly. Have the value of full featured program, for the cost of a lightweight basic app.
How to edit a PDF document using the pdfFiller editor:
For pdfFiller’s FAQs
Ready to try pdfFiller's? Cloud Security Trust Sign