Get the free cyber security incident report examples
Show details
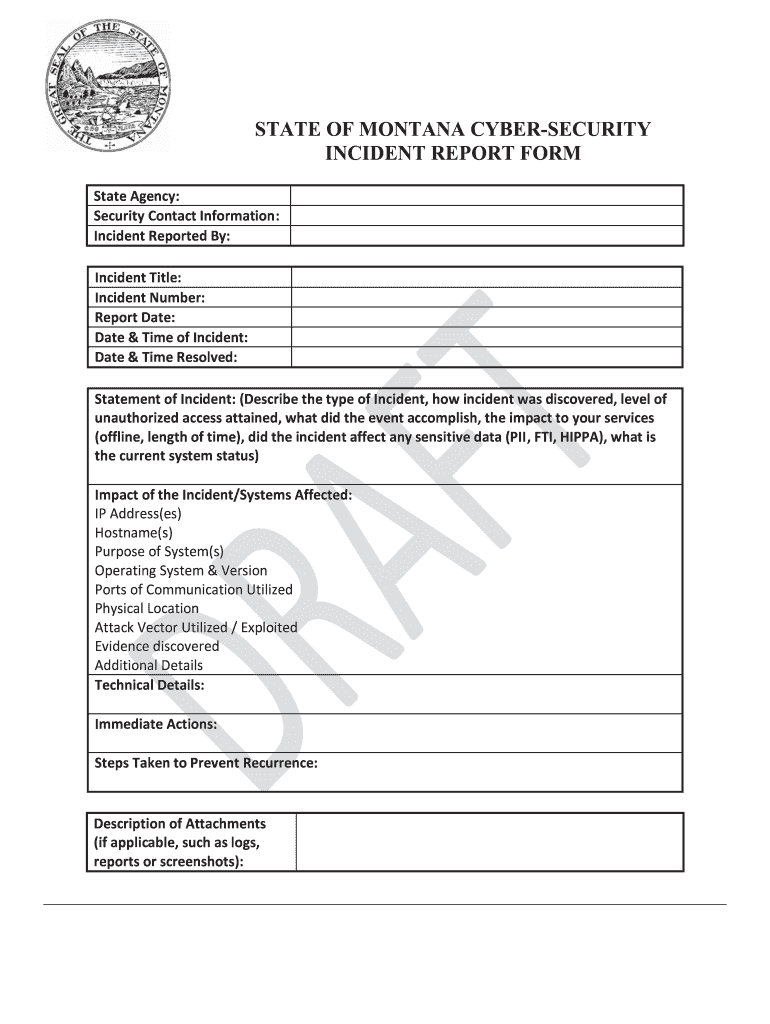
STATE OF MONTANA CYBERSECURITY INCIDENT REPORT FORM State Agency: Security Contact Information: Incident Reported By: Incident Title: Incident Number:
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cyber security incident report template form

Edit your cyber incident report template form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cybersecurity incident report template form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing cyber incident report example online
Follow the steps down below to use a professional PDF editor:
1
Set up an account. If you are a new user, click Start Free Trial and establish a profile.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit cyber security incident report template word form. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Create an account to find out for yourself how it works!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cyber incident response report template form

How to fill out cyber security incident reporting:
01
Gather all relevant information about the incident, including the date and time it occurred, the systems or networks affected, and any potential vulnerabilities that were exploited.
02
Document the impact of the incident, such as the extent of data loss or unauthorized access. Include details on the potential risks and consequences associated with the incident.
03
Provide a detailed description of the incident, including any suspicious activities or behaviors observed. Include information on any malware or hacking techniques used, if known.
04
Identify any individuals or entities involved in the incident, if possible. This may include internal employees, external hackers, or other relevant parties.
05
Determine the root cause of the incident and any contributing factors. This may involve conducting a thorough investigation or engaging with relevant technical experts.
06
Outline any immediate actions taken to mitigate the incident and prevent further damage. Describe any security measures implemented or systems patched to address vulnerabilities.
07
Assess the overall impact and severity of the incident. This may involve conducting a risk assessment or engaging with relevant stakeholders to determine the potential consequences.
08
Finally, submit the completed incident report to the appropriate authorities or internal teams, following any specific reporting procedures or guidelines outlined by your organization.
Who needs cyber security incident reporting:
01
Organizations of all sizes and industries can benefit from cyber security incident reporting. It is essential for both private and public sector entities.
02
Government agencies and regulatory bodies often require organizations to report cyber security incidents as part of compliance or legal obligations.
03
Cyber security incident reporting is necessary to ensure transparency and accountability, as well as to facilitate effective incident response and recovery.
04
Stakeholders within an organization, including executives, IT departments, and legal teams, rely on incident reporting to understand the overall cyber security posture and detect any patterns or trends.
05
External parties such as customers, partners, and shareholders may also require incident reporting to evaluate the organization's commitment to safeguarding sensitive information.
06
Ultimately, anyone who wants to protect their data and prevent future incidents should prioritize cyber security incident reporting.
Fill
information security incident report template
: Try Risk Free






People Also Ask about cybersecurity incident report example
What should be included in a cyber incident report?
Helpful information could include who you are, who experienced the incident, what sort of incident occurred, how and when the incident was initially detected, what response actions have already been taken, and who has been notified.
What is an example of cybersecurity incident?
There are many types of cybersecurity incidents typically caused by insiders, such as sensitive data leaks and breaches, trade secrets and insider data theft, privilege misuse, and phishing attacks.
What is a security incident in cyber security?
A security incident can be anything from an active threat to an attempted intrusion to a successful compromise or data breach. Policy violations and unauthorized access to data such as health, financial, social security numbers, and personally identifiable records are all examples of security incidents.
What are the 4 types of incident reports?
Common Types of Incident Reports Workplace. Workplace incident reports detail physical events that happen at work and affect an employee's productivity. Accident or First Aid. Safety and Security. Exposure Incident Report.
How do you write an incident report for security?
How to write a security report Take notes. Details and observations make up the bulk of your security reports. Start with a summary. Detail the narrative. Follow the form. Proofread. Avoid emotional language. Avoid abbreviations and conjunctions. Be prompt.
Our user reviews speak for themselves
Read more or give pdfFiller a try to experience the benefits for yourself
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Can I create an eSignature for the cyber security incident report pdf in Gmail?
You may quickly make your eSignature using pdfFiller and then eSign your cybersecurity incident response report template right from your mailbox using pdfFiller's Gmail add-on. Please keep in mind that in order to preserve your signatures and signed papers, you must first create an account.
How do I edit it security incident report template on an iOS device?
You can. Using the pdfFiller iOS app, you can edit, distribute, and sign cybersecurity incident response report example. Install it in seconds at the Apple Store. The app is free, but you must register to buy a subscription or start a free trial.
How can I fill out cyber security incident template on an iOS device?
Install the pdfFiller app on your iOS device to fill out papers. If you have a subscription to the service, create an account or log in to an existing one. After completing the registration process, upload your cyber security incident report example. You may now use pdfFiller's advanced features, such as adding fillable fields and eSigning documents, and accessing them from any device, wherever you are.
What is cyber security incident reporting?
Cyber security incident reporting is the process of documenting and communicating information regarding a security breach, cyber attack, or any other event that may compromise the confidentiality, integrity, or availability of information systems or data.
Who is required to file cyber security incident reporting?
Individuals and organizations that experience or observe a cyber security incident are generally required to file cyber security incident reports. This often includes companies in regulated industries, government agencies, and any entity handling sensitive data.
How to fill out cyber security incident reporting?
To fill out cyber security incident reporting, one should gather relevant details about the incident, including when and how it occurred, the systems affected, any detected vulnerabilities, and the response actions taken. This information should be organized according to the reporting guidelines provided by the relevant authority.
What is the purpose of cyber security incident reporting?
The purpose of cyber security incident reporting is to facilitate timely and effective responses to security incidents, improve information sharing between organizations, enhance overall security posture, and comply with legal and regulatory requirements.
What information must be reported on cyber security incident reporting?
The information that must be reported typically includes the date and time of the incident, a description of the incident, the type of data involved, the impact assessment, the entities affected, and any corrective actions taken or planned.
Fill out your cyber security incident report online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cyber Security Incident Report Template Excel is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















