
Get the free Security Access Request - xray tamu
Show details
This document is a request form for security access to teaching, research, and office areas in the Chemistry Building at Texas A&M University, requiring personal and supervisor information, and detailing
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign security access request
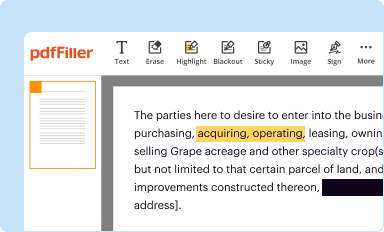
Edit your security access request form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
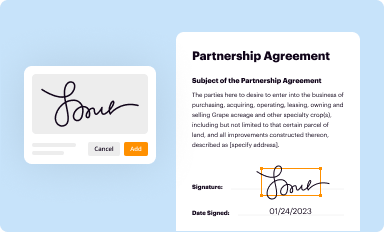
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your security access request form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing security access request online
Follow the guidelines below to benefit from a competent PDF editor:
1
Log in. Click Start Free Trial and create a profile if necessary.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit security access request. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Get your file. Select the name of your file in the docs list and choose your preferred exporting method. You can download it as a PDF, save it in another format, send it by email, or transfer it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Try it for yourself by creating an account!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security access request
How to fill out Security Access Request
01
Begin by accessing the Security Access Request form from the designated website or internal portal.
02
Fill out your personal information, including name, department, and contact details.
03
Specify the type of access you are requesting, selecting from the options provided.
04
Provide a justification for the access request, explaining why it is necessary for your role.
05
Indicate the duration for which access is required, specifying dates if applicable.
06
Review the form for accuracy and completeness before submission.
07
Submit the request to the appropriate supervisor or security officer for approval.
Who needs Security Access Request?
01
Employees who require access to restricted areas or sensitive information.
02
Contractors or external partners needing temporary access for specific projects.
03
New hires who need security access as part of their onboarding process.
04
Existing staff who require additional access to perform their jobs effectively.
Fill
form
: Try Risk Free






People Also Ask about
What is a DSAR in English?
A Data Subject Access Request (DSAR) is directed to the organization granting individuals the right to access information about personal data the organization is processing.
How to word a SAR request?
Your SAR should include: A clear label for your request (use 'subject access request' as your email subject line or a heading for your letter) The date of your request. Your name. Any other information used by the organisation to help prove to them that you are who you say you are. Your current contact details.
What does SAR stand for in GDPR?
What is a subject access request (SAR)? A SAR is a request made by or on behalf of an individual for the information which they are entitled to ask for under Article 15 of the UK GDPR.
What is included in a SAR request?
We suggest you include the following information in a SAR: a subject line or header that says "subject access request"; the date you're making the request; your name (and any other names where relevant, eg your name before you were married); your email address, home address and phone number;
What is an example of a subject access request?
For example, a parent could approach a teacher at the end of a school day and say, “I want all the information the school hold on my child.” This would be a valid subject access request. All staff should be able to recognise the SAR and know the next steps to take.
What does an SAR stand for?
Suspicious Activity Reports (SAR)
What does SAR in GDPR stand for?
What is a subject access request (SAR)? A SAR is a request made by or on behalf of an individual for the information which they are entitled to ask for under Article 15 of the UK GDPR.
What does SAR stand for in data?
A subject access request (SAR) is a request made to a data controller by an individual for a copy of their personal data (as opposed to original documents) which that data controller holds on that individual.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is Security Access Request?
A Security Access Request is a formal document or process used to request access to secure systems or sensitive information within an organization.
Who is required to file Security Access Request?
Employees, contractors, or any individuals who need access to secure systems or data within the organization are typically required to file a Security Access Request.
How to fill out Security Access Request?
To fill out a Security Access Request, individuals must provide their personal information, specify the type of access needed, justify the request, and obtain necessary approvals from their supervisor or relevant authority.
What is the purpose of Security Access Request?
The purpose of the Security Access Request is to ensure that access to sensitive information and systems is granted only to authorized personnel, maintaining the organization's security and compliance.
What information must be reported on Security Access Request?
The information that must be reported on a Security Access Request typically includes the requestor's name, employee ID, department, type of access requested, purpose of access, and approvals from supervisors.
Fill out your security access request online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security Access Request is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















