
Get the free cryptography theory and practice 4th edition pdf
Fill out, sign, and share forms from a single PDF platform
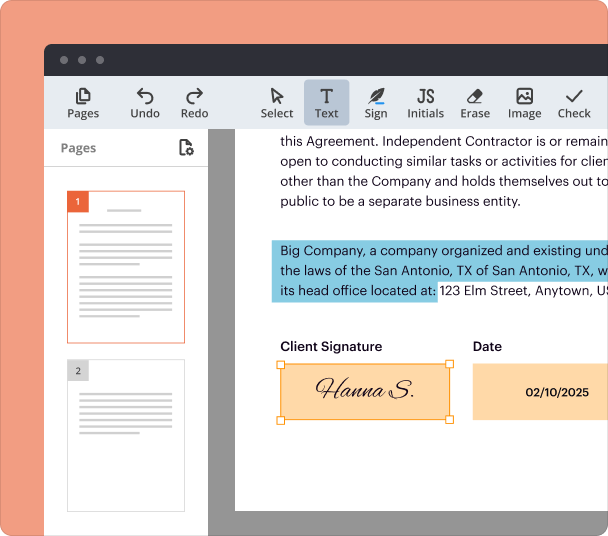
Edit and sign in one place
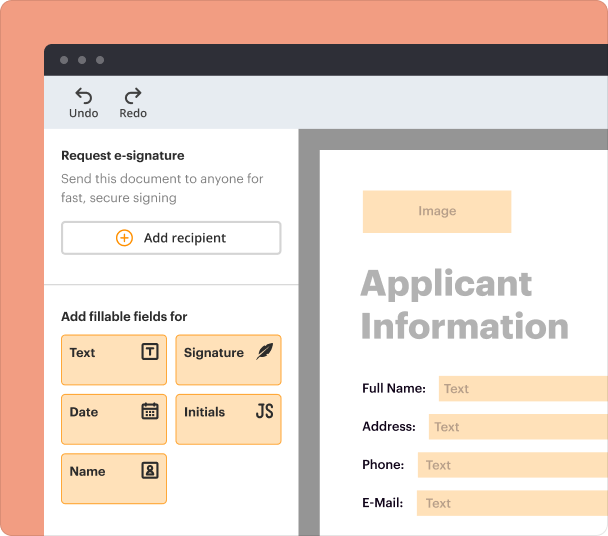
Create professional forms
Simplify data collection
Manage forms centrally
Why pdfFiller is the best tool for your documents and forms
End-to-end document management
Accessible from anywhere
Secure and compliant
How to fill out a cryptography formory and practice form form
Understanding cryptography: theory and practice
Cryptography plays a crucial role in protecting information in today's digital world. It encompasses techniques for securing communication and ensuring data integrity. Key concepts include encryption, decryption, and cryptographic algorithms, which are the backbone of modern cybersecurity protocols. For example, symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption relies on a pair of keys.
-
In the digital age, ensuring information security is paramount. Cryptography protects sensitive data from unauthorized access and cyber threats.
-
Understanding encryption and decryption is essential for anyone working with data security. Cryptographic algorithms enable these processes.
-
Symmetric and asymmetric encryption serve different purposes, making it important to choose the right method based on the application's needs.
-
Industries such as finance and healthcare utilize cryptography to safeguard transactions and confidential patient information.
Exploring key components of cryptographic methods
A thorough understanding of cryptographic keys and algorithms is vital for anyone involved in data protection. Passwords and digital signatures often utilize symmetric keys for encryption, while protocols like RSA employ asymmetric keys for secure communication. Learning about popular algorithms such as AES, which is widely used for encrypting sensitive data, is essential.
-
Keys are the foundation of all cryptographic functions. They must be kept secure to ensure the protection of sensitive information.
-
Algorithms like AES and RSA are widely recognized for their effectiveness in safeguarding data.
-
Understanding how protocols function can help in identifying potential vulnerabilities.
-
Maintaining confidentiality and integrity of cryptographic keys is critical for ensuring security.
Filling out cryptographic forms: step-by-step guidance
Filling out cryptography-related forms can sometimes be daunting, but with the right tools, the process can be streamlined. pdfFiller offers a user-friendly interface for managing all your document needs, making it easier to complete forms accurately. Begin with accessing pdfFiller to create and manage your forms effectively, followed by utilizing their tools to edit and sign them.
-
Start by visiting pdfFiller's website, where you can create an account to access various document management features.
-
Follow guided prompts to fill out specific fields. Take your time to review each section thoroughly.
-
Enhance your forms by adding signatures or making necessary edits with the available tools.
-
Utilize pdfFiller's interactive features to facilitate easier document management.
Editing and managing cryptographic documents on pdfFiller
Editing and reviewing cryptographic documents is essential for ensuring compliance and accuracy. pdfFiller provides users with various options for editing PDF documents by allowing text, images, and annotations to be seamlessly added. Collaborative features enable sharing documents with colleagues for review and signatures, fostering teamwork and efficiency.
-
Users can add necessary elements such as text, images, or comments depending on their needs.
-
Share documents with teammates for feedback, reviews, and signing.
-
Leverage cloud storage to access documents from anywhere, a significant advantage in today’s remote work environment.
-
Combine pdfFiller with other applications to optimize functionality for document management.
Understanding compliance in cryptography practices
Compliance with legal standards is non-negotiable in cryptography. Various regulations, such as GDPR and HIPAA, mandate robust data protection frameworks, and failure to comply can lead to severe consequences. Understanding the legal landscape will better prepare users to navigate regulations relevant to their work.
-
Learn about regulations that govern data protection and the impact of failing to adopt best practices.
-
Complying with rules like PCI DSS ensures that organizations meet required safeguarding standards.
-
Establish protocols to maintain compliance while managing cryptographic documents effectively.
-
Non-compliance can result in legal penalties as well as damage to reputation.
Harnessing the power of cryptographic solutions
Evaluating cryptographic methods can significantly impact an organization's security posture. By examining case studies on successful implementations, users can gain insights into the most effective techniques. With advancements on the horizon, understanding future trends is crucial for preparedness.
-
Assess various methods to identify which is most effective for your security needs.
-
Learn from organizations that have successfully implemented cryptography to enhance their security.
-
Stay informed about emerging technologies and practices that may influence cryptographic approaches.
-
pdfFiller is evolving to support users in navigating the changing landscape of cryptography.
Frequently Asked Questions about cryptography theory and practice form
What is cryptography?
Cryptography is the practice of securing information through techniques like encryption and decryption. It ensures that sensitive data remains confidential and protected from unauthorized access.
How do I fill out a cryptography-related form?
To fill out a cryptography-related form, access a platform like pdfFiller, follow step-by-step instructions, and utilize their tools for editing and signing your documents.
What are the types of cryptographic algorithms?
Cryptographic algorithms can be classified mainly into symmetric and asymmetric types. Symmetric algorithms use the same key for encryption and decryption, while asymmetric algorithms use a key pair for secure communications.
Why is compliance important in cryptography?
Compliance is crucial in cryptography to meet legal standards and protect user data. Regulations like GDPR and HIPAA help ensure that sensitive information is managed securely.
pdfFiller scores top ratings on review platforms

















