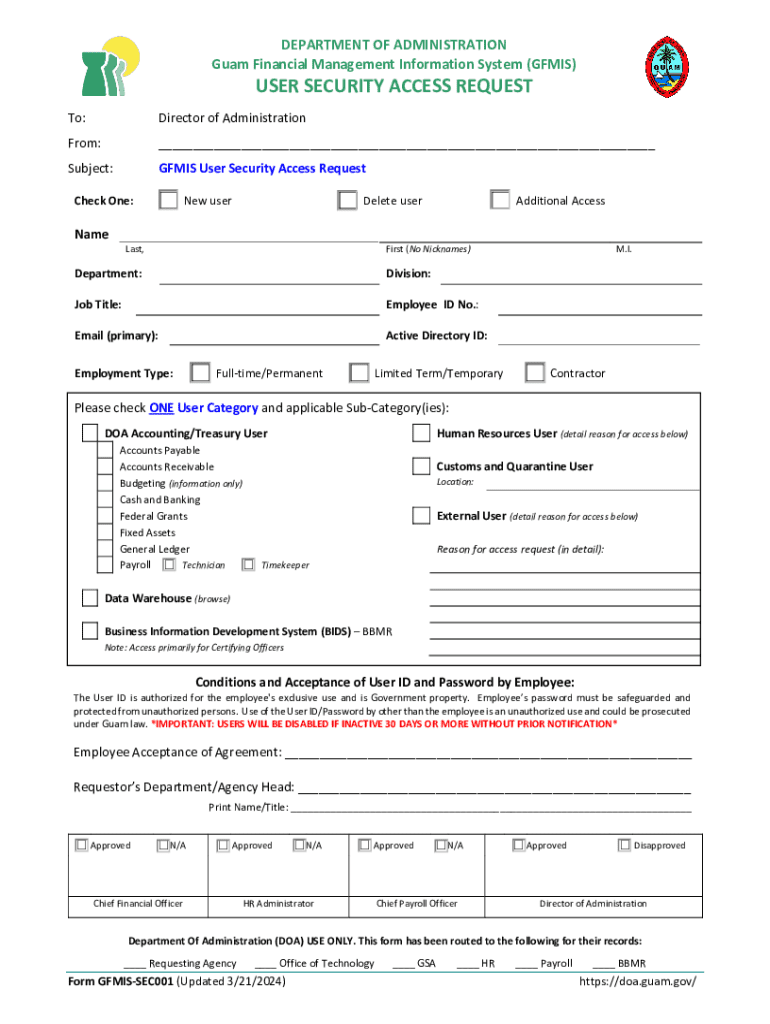
Get the free user security access requestdoa - doa guam
Get, Create, Make and Sign user security access requestdoa



How to edit user security access requestdoa online
Uncompromising security for your PDF editing and eSignature needs
How to fill out user security access requestdoa

How to fill out user security access requestdoa
Who needs user security access requestdoa?
Comprehensive Guide to the User Security Access Request DOA Form
Overview of user security access request DOA form
The User Security Access Request DOA Form is a crucial document designed for individuals seeking access to sensitive data and systems within an organization. This form serves as the first step in a structured process to ensure that only authorized personnel can access specific data sets. By enforcing stringent security measures, organizations can protect both their internal data and the privacy of individuals involved.
In the digital age, managing security access becomes indispensable to safeguard sensitive information. The access request process allows organizations to verify the legitimacy of requests while minimizing the risk of data breaches. Utilizing tools like pdfFiller for managing access requests offers efficient features that streamline submission and approvals.
Understanding user security access requests
User security access requests refer to formal applications for permission to access designate information stored in databases or systems. The primary goal of these requests is to manage and protect sensitive or confidential information effectively. Organizations implement this process to ascertain who accesses what data and why, creating a controlled environment for information handling.
Typically, individuals across various roles are required to submit a security access request. This includes both single users and teams, such as researchers, administrative personnel, or project leaders, who may need to access information relevant to their functions. Roles commonly requiring such access range from educators and administrators to IT staff and data analysts.
Step-by-step guide to filling out the access request form
Filling out the User Security Access Request DOA Form can be a straightforward process if each step is followed carefully. Below is a step-by-step guide to ensure that you provide all necessary information and improve the chances of your request being approved.
Approving a user security access request
The approval process for a User Security Access Request is crucial for maintaining the integrity of an organization's information security. After submission, designated individuals are responsible for reviewing the request and making a decision regarding approval.
Those responsible for approving requests typically include department heads, data stewards, or IT security personnel, depending on the organization's structure. They assess several factors during approval, including the need for access and the user's role within the organization.
Frequently asked questions
Understanding the dynamics of the access request process is essential for smooth operations. Below are commonly asked questions regarding the User Security Access Request DOA Form to help users navigate the process.
Tips for streamlining the access request process
To enhance the efficiency of your user security access request submission, consider the following best practices. These strategies help mitigate common issues and promote smoother transactions throughout the process.
Resources for users
For those looking to initiate a User Security Access Request, the process begins with the access request form found on pdfFiller. With a range of tools available for effective document management, these resources promote smooth navigation through the document lifecycle.
Important notes about security access requests
It's essential to acknowledge the privacy and security considerations that accompany security access requests. As these forms deal with sensitive data, organizations must comply with various regulatory requirements to maintain confidentiality.
Failure to manage access appropriately can lead to severe consequences, including data leaks or loss of trust from stakeholders. Therefore, it is vital for individuals completing access requests to understand their responsibilities and the potential implications of unauthorized access.
Additional access and forms
Organizations often require various forms for different access scenarios. pdfFiller provides a wide-range selection of related forms, facilitating a comprehensive approach to security access management. Exploring related forms can enhance efficiency and clarity in the request process.
Feedback and improvements
Feedback is vital in refining the access request process. Users are encouraged to share insights about their experiences, allowing organizations to continuously improve upon existing systems and frameworks.
Engaging in a dialogue not only fosters a collaborative environment but also enhances the effectiveness of the security protocols implemented within the organization.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send user security access requestdoa for eSignature?
Can I sign the user security access requestdoa electronically in Chrome?
How do I fill out user security access requestdoa using my mobile device?
What is user security access requestdoa?
Who is required to file user security access requestdoa?
How to fill out user security access requestdoa?
What is the purpose of user security access requestdoa?
What information must be reported on user security access requestdoa?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.















