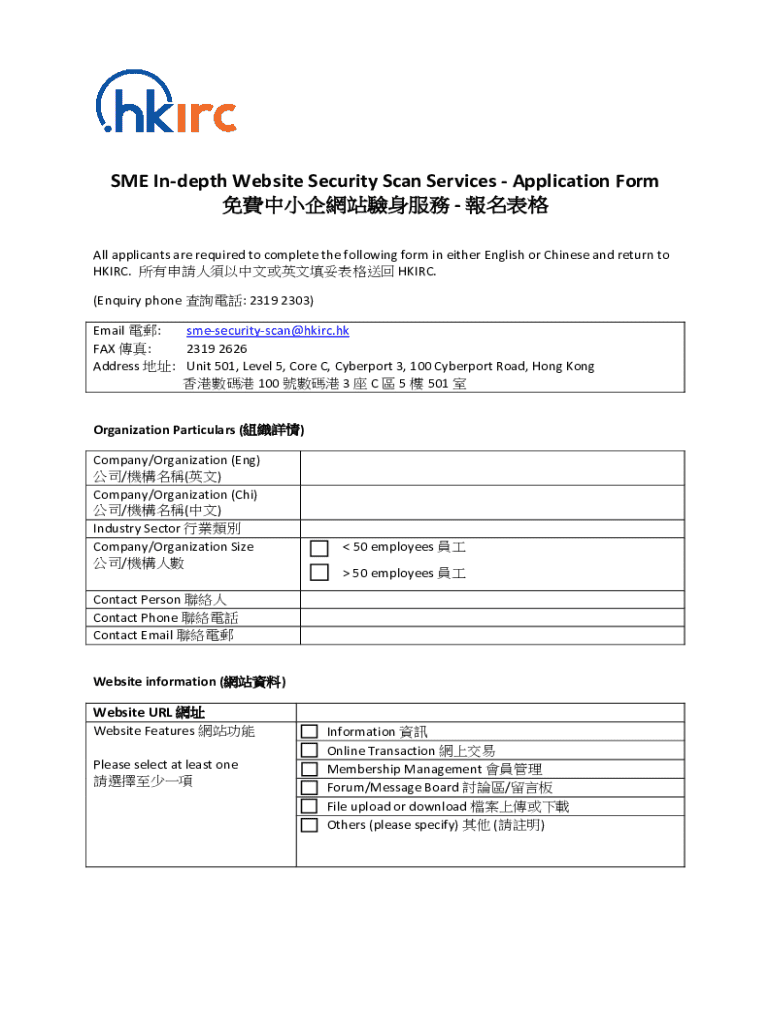
Get the Free In-depth Website Security Scan Services
Get, Create, Make and Sign in-depth website security scan



How to edit in-depth website security scan online
Uncompromising security for your PDF editing and eSignature needs
How to fill out in-depth website security scan

How to fill out in-depth website security scan
Who needs in-depth website security scan?
In-Depth Website Security Scan Form: A Comprehensive Guide
Understanding the in-depth website security scan form
An in-depth website security scan form serves as a vital tool for both individuals and businesses seeking to enhance their online security posture. By collecting necessary information, this form facilitates a thorough evaluation of a website's vulnerabilities. The purpose is to identify weaknesses that malicious actors may exploit, making it essential for maintaining a secure digital presence.
Website security scans are crucial for protecting sensitive data, preventing unauthorized access, and ensuring compliance with regulations such as GDPR. Scans can uncover a range of common vulnerabilities, including outdated software, weak passwords, and misconfigured security settings. Understanding these vulnerabilities is the first step in mitigating risks and fortifying a website against potential threats.
Key components of an effective security scan
A comprehensive security scan must consist of several key components to effectively identify vulnerabilities. This includes deciding between automated and manual scans, as each method has its own advantages and limitations. Automated scans are generally faster and can cover more ground, but manual scans allow for a more nuanced examination.
Another component is penetration testing, where an ethical hacker simulates attacks to find weaknesses before malicious actors do. Essential tools for performing security scans include software like Nessus, OpenVAS, and Burp Suite, which systematically test for common vulnerabilities. When selecting a security scan solution, look for features such as comprehensive reporting, update frequency, and support for different programming languages.
Step-by-step guide to completing the in-depth website security scan form
Completing the in-depth website security scan form starts with gathering the necessary information. Required credentials typically include the website URL and access to administrative accounts to ensure thorough testing. Additionally, providing contact information is essential for follow-up communication regarding the scan outcomes.
Next, it's crucial to identify the scope and objectives of the scan. This involves specifying particular areas of the website to focus on, such as databases or payment gateways, and setting realistic expectations for the scan outcomes. Choosing the appropriate type of scan is equally important, where users can select from common vulnerabilities, such as SQL injection and Cross-Site Scripting (XSS), aligning the scan with their unique risk profile.
The scanning and analysis process
The scanning process primarily involves crawling the website to identify accessible assets, such as databases, API endpoints, and sensitive files. Automated tools gather data while testing for known vulnerabilities. This stage may also include tracking server responses to simulate attack scenarios and uncover risks.
Once the scan is completed, analyzing the results requires understanding the findings' severity and potential impact. Each vulnerability typically comes with an impact rating, guiding organizations on prioritization. It's also vital to distinguish between true vulnerabilities and false positives to avoid unnecessary panic and resource allocation. Validation techniques, such as retests, can provide further assurance.
Post-scan protocols: remediation and retesting
After completing the scan, the next logical step involves effective remediation of identified vulnerabilities. Addressing these issues promptly is crucial, particularly for high-severity vulnerabilities that can pose immediate risks. It's important to prioritize vulnerabilities based on their potential impact and exploitability, developing strategies for mitigating these risks.
Equally important is the process of retesting to ensure comprehensive security. Scheduling follow-up scans allows organizations to confirm that vulnerabilities have been appropriately addressed and that no new threats have emerged. Using the initial report as a baseline for comparison can streamline remediation efforts and track improvements over time.
Best practices for ongoing website security maintenance
Ongoing maintenance is vital for ensuring long-term website security. Implementing regular security scans is an essential practice to stay abreast of new vulnerabilities and threats. Establishing a cadence for scanning, such as weekly or monthly assessments, can help organizations proactively manage their security posture.
Moreover, training team members on security best practices enhances overall security awareness across the organization. Integrating security scans into development workflows ensures that security considerations are baked into the development lifecycle, reducing the likelihood of vulnerabilities being introduced.
Scaling your security efforts
As organizations grow, scaling security efforts becomes critical. Utilizing API integrations for automated scanning simplifies the process, allowing teams to seamlessly incorporate security assessments into their existing workflows. These integrations enable real-time updates and alerts, ensuring that any newly discovered vulnerabilities are quickly addressed.
Enhancing team collaboration is also beneficial, as sharing insights and findings across departments fosters a comprehensive approach to security. Additionally, advanced tools equipped with machine learning classifiers can help predict and respond to emerging threats more effectively, thus bolstering an organization’s security framework.
Real-world applications of the in-depth website security scan form
The application of the in-depth website security scan form transcends the theoretical realm, with real-world use cases highlighting its effectiveness. For instance, a small e-commerce business was able to identify critical SQL injection vulnerabilities through thorough scanning, leading to immediate remediation measures that safeguarded customer data and trust.
Testimonials from users often reflect the value of employing comprehensive scans, emphasizing improvements in web security posture and awareness. Moreover, numerous examples exist of major vulnerabilities discovered during routine scans, allowing organizations to proactively address these issues before they could be exploited by malicious entities.
Preparing for the future of website security
In the ever-evolving landscape of cyber threats, organizations must remain vigilant and adapt to emerging risks. Trends in website security, such as the rise of artificial intelligence and machine learning in security protocols, signify where the future is headed. With tools from pdfFiller, businesses can maintain a forward-focused security strategy that supports ongoing assessments and adaptability.
Fostering a culture of security awareness within organizations translates into greater resilience against threats. Training programs and continuous evaluations help employees recognize and address vulnerabilities, forming a critical line of defense in the security strategy. Building a proactive rather than reactive security framework ensures that ongoing challenges are met with preparedness.
Frequently asked questions about the in-depth website security scan form
One of the common challenges faced by users when completing the in-depth website security scan form is understanding the technical terminology involved. Non-technical users may find it daunting to navigate terms like ‘SQL injection’ or ‘XSS’. Therefore, providing clear explanations and examples within the form can alleviate confusion and enhance user experience.
Moreover, teams with varied technical expertise may struggle with hands-on scanning practices. Offering comprehensive guidelines, along with the examples of potential vulnerabilities, can ensure that everyone—from non-tech staff to IT specialists—can contribute to the security assessment process effectively.
Additional features and enhancements
As technology evolves, innovations in security scanning continue to emerge. Regular updates to the in-depth website security scan form from pdfFiller will introduce enhanced functionalities that facilitate even more effective vulnerability assessments. Future updates may include deeper integrations with security tools, real-time scanning capabilities, and advanced reporting analytics.
Feedback mechanisms will also play a crucial role in these enhancements. By gathering user input, pdfFiller can continuously improve its offerings, ensuring that the in-depth website security scan form meets the dynamic needs of its users, ultimately fortifying defenses against emerging security threats.






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Where do I find in-depth website security scan?
Can I create an electronic signature for the in-depth website security scan in Chrome?
How do I complete in-depth website security scan on an Android device?
What is in-depth website security scan?
Who is required to file in-depth website security scan?
How to fill out in-depth website security scan?
What is the purpose of in-depth website security scan?
What information must be reported on in-depth website security scan?
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.















