Get the free Responsible Computer Network and Internet Use for Schools template
Show details
A Responsible Computer, Network and Internet Use guide that can be used by schools.
We are not affiliated with any brand or entity on this form
Why choose pdfFiller for your legal forms?
All-in-one solution
pdfFiller offers a PDF editor, eSignatures, file sharing, collaboration tools, and secure storage—all in one place.
Easy to use
pdfFiller is simple, cloud-based, has a mobile app, and requires no downloads or a steep learning curve.
Secure and compliant
With encryption, user authentication, and certifications like HIPAA, SOC 2 Type II, and PCI DSS, pdfFiller keeps sensitive legal forms secure.

What is responsible computer network and
A responsible computer network is a system of interconnected devices designed to ensure safe, ethical, and efficient use of data and resources.
pdfFiller scores top ratings on review platforms




I enjoy updating documents without creating a entirely new document. I wish there was shading an area after you erase to match the background of the document.
Easy to use and great way to organize my fillable docs
I HAVE A HARD TIME FILLING OUT FORMS BECAUSE MY HANDS TRIMBLE.THIS MAKES IT MORE LEDGABLE
UN F'n Believable...this should be locked down and held a secret with me being your last member..It has given me wings to unlimited potential...thanks
works great. love the copy, rename, erase, all of it. Just what I needed.
Works great. It's too expensive though. Very simple program that I don't use much. Would gladly pay $20/yr.
Who needs responsible computer network and?
Explore how professionals across industries use pdfFiller.
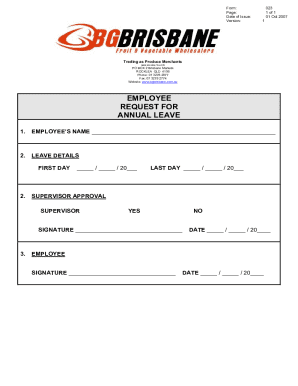
Responsible Computer Network and Internet Use Guide
What does it mean to understand computer network and system administration?
Computer network administration involves managing and maintaining the networks that facilitate communication and data exchange. It requires knowledge of both hardware and software components and is critical in ensuring that the infrastructure runs smoothly and securely.
-
Computer network administration entails the setup, management, and troubleshooting of computer networks to ensure connectivity and performance.
-
Proper management of a network is essential for safeguarding sensitive data and ensuring that systems remain functional.
-
Network administrators must uphold ethical standards, ensuring trust and privacy while managing user data.
Why is accessing technology resources considered a privilege?
Accessing technology resources is a privilege because it allows individuals to leverage tools that can enhance productivity and knowledge. However, with this privilege comes responsibility.
-
ICT encompasses all technologies used to handle telecommunications, broadcast media, intelligent building management systems, and audio-visual processing and transmission systems.
-
Privileged access refers to the enhanced level of control over resources, while rights are what users are entitled to within the system.
-
Misusing technology resources can lead to security breaches and loss of trust, damaging both personal reputations and institutional integrity.
What is a policy framework for responsible use of technology?
A policy framework for responsible use outlines the guidelines and protocols for acceptable usage of technology within an organization.
-
These policies define what constitutes acceptable behavior when accessing technology resources, helping to protect both users and the organization.
-
Implementing training sessions and workshops can foster a culture of responsible technology use among users.
-
Compliance with the Children’s Internet Protection Act (CIPA) ensures that schools and libraries provide a safe online environment for minors.
How does digital citizenship play a role in technology use?
Digital citizenship refers to the responsible use of technology and the internet. It emphasizes the need for ethical behavior online and fosters respect among all users.
-
Digital citizenship involves understanding how to engage safely and ethically in the digital realm.
-
Ethical use of IT is crucial for maintaining trust and integrity in online interactions.
-
Both students and educators must uphold standards of behavior that promote a positive digital environment.
What educational initiatives can support responsible technology use?
Educational initiatives should focus on instilling values of digital ethics and responsible behavior in users at all levels.
-
Training programs can educate users on the implications of their digital footprint and the importance of ethical online behavior.
-
Promoting a balanced approach to technology use can help mitigate negative impacts associated with excessive screen time.
-
Utilizing varied teaching methods can accommodate different learning preferences, facilitating better understanding and retention of responsible practices.
What tools can assist in implementing network responsibility?
Various tools are available to help organizations and individuals monitor and manage their network usage effectively.
-
Monitoring tools allow administrators to track activity on the network, aiding in the identification of potential misuse.
-
pdfFiller streamlines the management of acceptable use policies, making them more accessible to users.
-
Using collaborative tools can enhance teamwork among stakeholders when developing and updating internet policies.
What are the future challenges and opportunities in network administration?
As technology evolves, network administrators must be prepared to face new challenges while also seizing opportunities for improvement.
-
Trends such as increased cloud integration and remote work are reshaping network management practices.
-
AI is increasingly being utilized to enhance security protocols and automate network monitoring processes.
-
Staying informed about regulatory changes will help organizations adapt their policies and practices accordingly.
How to fill out the responsible computer network and
-
1.Open the PDF filler application and log in to your account.
-
2.Locate the template for 'Responsible Computer Network and' in the document library.
-
3.Once you have opened the template, read the instructions carefully to understand the required fields.
-
4.Start filling in the general information section with your organization’s name, address, and contact details.
-
5.Proceed to the next section where you define your network usage policies, including acceptable behavior and security protocols.
-
6.In the data management section, include guidelines on data access, sharing, and storage responsibilities.
-
7.Clarify roles and responsibilities for network administrators, users, and any other stakeholders involved.
-
8.Review all sections to ensure accuracy and completeness of the information provided.
-
9.Once you have filled in all required fields, save the document.
-
10.Finally, download or share the completed document as needed.
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.