Get the free Employee Policy for Ination Security template
Show details
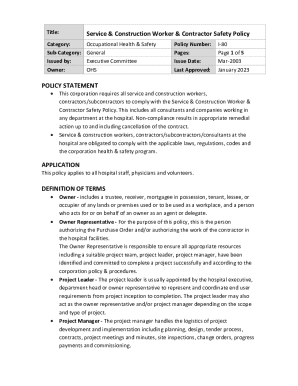
This document is an important policy for a company that relies on its information assets and computer resources to conduct and support its business operations with its customers, employees and suppliers.
We are not affiliated with any brand or entity on this form
Why choose pdfFiller for your legal forms?
All-in-one solution
pdfFiller offers a PDF editor, eSignatures, file sharing, collaboration tools, and secure storage—all in one place.
Easy to use
pdfFiller is simple, cloud-based, has a mobile app, and requires no downloads or a steep learning curve.
Secure and compliant
With encryption, user authentication, and certifications like HIPAA, SOC 2 Type II, and PCI DSS, pdfFiller keeps sensitive legal forms secure.

What is employee policy for information
An employee policy for information outlines guidelines and expectations regarding the handling and protection of company and employee data.
pdfFiller scores top ratings on review platforms




Very helpful
excellent platform
New and anxious to learn.
I really like your product. I am not very computer savvy so I would greatly appreciate a webinar to help with navigating your website. That being said I have used your chat feature several times and your agents have all been awesome...very helpful!!
it is an easy programme to use
Great tool to use for editing forms
Who needs employee policy for ination?
Explore how professionals across industries use pdfFiller.
Comprehensive Guide to Employee Policy for Information Form
In this guide, we will explore how to fill out an employee policy for information form effectively, ensuring all necessary information is accurately provided.
What is the necessity of an employee policy for information security?
Information security is foundational to maintaining trust and efficiency within company operations. Without it, sensitive corporate and employee data may be vulnerable to breaches or unauthorized access. A clear employee policy outlines the necessity of protecting these information assets and highlights the benefits of having a structured approach to information management.
-
A well-defined policy establishes clear roles and responsibilities regarding information security.
-
Relevant policies help safeguard valuable company and personal information from threats.
-
With proper guidelines, employees can confidently handle information, fostering an environment of trust and accountability.
Who does the employee policy apply to?
The scope of the employee policy for information security extends to all employees, contractors, and third-party vendors interacting with sensitive data. It's crucial to outline who the policy applies to make sure everyone understands their obligations when handling company information. This universal adherence is essential for creating a secure workplace.
-
Direct employees are the primary users of the information and must follow security protocols.
-
Contractors often have access to sensitive information and are expected to comply with the same standards as employees.
-
Third-party vendors should also be informed about the security measures to protect shared data.
What are the core elements of the employee policy?
Key components of an effective employee policy include three main principles: confidentiality, integrity, and availability (often referred to as the CIA triad). Employee training is a critical aspect, ensuring that team members can execute their responsibilities competently.
-
Ensures sensitive information is accessible only to those authorized to have access.
-
Maintains the accuracy and completeness of information, preventing unauthorized alterations.
-
Ensures that data is readily accessible to authorized users when needed.
-
Regular policy training helps employees understand their roles and the importance of information security.
-
Clearly detailed responsibilities create accountability among employees for information management.
How is the employee policy a living document?
An employee policy for information security is not static; it must evolve in response to organizational changes or emerging threats. Regular reviews and an established process for feedback are crucial for maintaining its relevance and effectiveness.
-
Adaptation to changes in company structure or external regulations is necessary to stay compliant.
-
Employees should be encouraged to seek permission for exceptions, ensuring they understand the policy's intentions.
-
Encouraging input can lead to valuable insights for improving the policy.
What types of information need protection?
Sensitive business development, operational, and employee data must be effectively safeguarded to prevent data breaches and ensure employee privacy. Understanding the types of protected information and their implications is vital.
-
Includes critical strategic documents and plans that can impact competitive advantage.
-
Covers daily operational processes, access to which is vital for maintaining efficiency.
-
Represents personal and sensitive information that must remain confidential.
How does compliance fit into the employee policy?
Ensuring compliance with relevant laws and regulations is a key aspect of any employee policy for information security. Employees have legal responsibilities regarding the handling of sensitive information, and failure to comply can result in serious consequences.
-
Understanding local laws governing data protection is essential for creating compliant policies.
-
Employees must be aware of their obligations and the legal implications of breached information.
-
Potential repercussions can include disciplinary action or legal penalties, underscoring the importance of adherence.
How can pdfFiller tools integrate with the employee policy?
Utilizing pdfFiller allows companies to fill out and edit the employee policy for information security forms seamlessly. The e-signature capability fosters quicker acceptance and compliance, making it easier for teams to engage with the document management processes.
-
Employees can easily fill out complex forms digitally, reducing paperwork burdens.
-
Electronic signatures simplify the approval process, enhancing workflow efficiency.
-
Using a cloud platform ensures that documents are accessible anytime, anywhere, promoting flexibility and security.
Why are policy review and update procedures important?
Regular policy reviews help ensure that the employee policy for information security remains effective and relevant. Assigning responsibility for updates and communicating changes to staff members are critical for ongoing adherence.
-
Establishing a schedule for periodic review of the policy maintains its relevance.
-
Assigning staff responsibility for updates ensures accountability and thoroughness.
-
Clear communication of updates or modifications ensures all employees remain informed and compliant.
How to fill out the employee policy for ination
-
1.Access the employee policy form on pdfFiller.
-
2.Make sure you're logged in to your pdfFiller account; if you don't have one, create an account.
-
3.Open the document and review the sections that require input.
-
4.Fill in your company name in the designated field at the top of the document.
-
5.Provide the current date to signify when the policy is effective.
-
6.Next, complete the sections describing employee responsibilities regarding information security.
-
7.Be specific about how employees should handle confidential data and the consequences of policy violations.
-
8.If there are sections requiring a signature, navigate to the signature field and apply your electronic signature.
-
9.Once you have reviewed all sections and filled in the necessary information, double-check for any errors or omissions.
-
10.Finally, save your completed policy and share it with relevant stakeholders or print it for distribution.
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.