Vulnerability Assessment Agreement Template free printable template
Show details
Este documento establece los trminos y condiciones para la realizacin de una evaluacin de vulnerabilidad de seguridad, crucial para la ciberseguridad y la proteccin de activos digitales.
We are not affiliated with any brand or entity on this form
Why pdfFiller is the best tool for managing contracts
End-to-end document management
From editing and signing to collaborating and tracking, pdfFiller has all the PDF tools you need for your contract workflow.
Mobile ready
pdfFiller is cloud-based, letting you edit, sign, and share contracts from your computer, smartphone, or tablet.
Legally binding & secure
pdfFiller lets you securely manage contracts with eSignatures that comply with global laws like ESIGN and GDPR. It's also HIPAA and SOC 2 compliant.

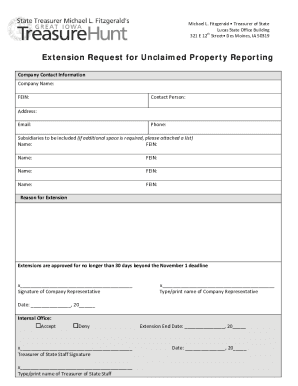
What is Vulnerability Assessment Agreement Template
A Vulnerability Assessment Agreement Template is a formal document outlining the terms and conditions for conducting a vulnerability assessment, which identifies weaknesses in a system or organization.
pdfFiller scores top ratings on review platforms




I can always find the right form on PDF Filler, thank you for all your assistance.Lue Robinson
Great for business documents, still could provide more simple directions but once you get the hang of things, it becomes easier.
great!! easy to work with the software ,many options ,fully recommended....
everything is clear , ease and very helpful
IT WAS GREAT. WAS ABLE TO DO A TASK I NEVER IMAGINED.
It makes legal documents cleaner and neate
Who needs Vulnerability Assessment Agreement Template?
Explore how professionals across industries use pdfFiller.
Creating a comprehensive vulnerability assessment agreement template: How to fill out a vulnerability assessment agreement form
Filling out a Vulnerability Assessment Agreement Template form requires understanding the key components that govern cybersecurity practices and responsibilities. This guide provides step-by-step instructions on creating, editing, signing, and eventually managing this critical document effectively.
What is a vulnerability assessment agreement?
A Vulnerability Assessment Agreement is a formal contract between a client and a service provider, outlining the terms under which a cybersecurity assessment will take place. Its significance lies in minimizing risks associated with potential security breaches while defining the roles and responsibilities of both parties in the assessment process.
-
It refers to an agreement that lays out all legal and operational protocols related to vulnerability assessments in cybersecurity environments.
-
It helps clarify expectations, obligations, and liabilities between the client and service provider.
-
Conducting thorough vulnerability assessments is crucial to identifying and mitigating cybersecurity risks.
Who are the parties involved in the agreement?
The Vulnerability Assessment Agreement specifies two main parties: the client requesting the assessment and the service provider conducting it. Identification of these entities is critical as it determines the contractual obligations each party must adhere to, ensuring clarity in legal accountability.
-
Typically the organization or individual seeking to assess their cybersecurity posture.
-
An external entity or consulting firm that specializes in vulnerability assessments.
-
Both parties must fulfill their respective duties as outlined in the agreement.
What is included in the scope of work?
The scope of work section delineates what the vulnerability assessment will cover, including systems, networks, and applications involved. It not only defines the service provider's tasks but also sets boundaries on the assessment to avoid misunderstandings about what is included and what is excluded.
-
Outlines the specific services to be delivered.
-
Defines the systems and applications subjected to the assessment.
-
Describes what will not be included in the assessment and the rationale behind these exclusions.
What are key definitions to know?
In any Vulnerability Assessment Agreement Template, clear definitions are paramount. Understanding who the client and service provider are, as well as the specific methods involved in vulnerability assessments, ensures that both parties are aligned on expectations and terminology.
-
A systematic examination of an information system to determine its security flaws.
-
Clearly defined roles help prevent confusion by identifying who is responsible for what.
What are the responsibilities of the service provider?
The service provider's responsibilities are crucial for an effective vulnerability assessment. This includes executing the assessment, reporting findings timely, and maintaining confidentiality throughout the process.
-
Carrying out the assessment as stipulated in the agreement.
-
Providing a thorough report on vulnerabilities detected and maintaining confidentiality regarding sensitive information.
-
Ensuring all deliverables are submitted within the agreed timeframe.
What responsibilities does the client hold?
Clients play a vital role in the success of the assessment. Their responsibilities often include providing necessary access and ensuring a single point of communication to facilitate collaboration between both entities.
-
Clients must provide the service provider with necessary systems and data for evaluation.
-
Ensuring that there is a designated individual to streamline communication.
-
Facilitating necessary procedures and approvals inside the organization for the assessment.
What findings and recommendations will be provided?
After completing the vulnerability assessment, the service provider documents all identified vulnerabilities. Understanding these findings is essential for remediation efforts, as this informs how organizations can bolster their cybersecurity measures effectively.
-
A comprehensive account of all identified issues requiring resolution.
-
Strategies for addressing vulnerabilities and improving security.
-
Importance of following up on findings to maintain or improve overall security health.
How to ensure legal compliance and best practices?
Legal compliance is critical in vulnerability assessments. Organizations must be aware of relevant laws and regulations that impact the assessment process, including best practices that should be followed to craft a robust agreement.
-
Understanding laws such as GDPR or HIPAA that could impact the assessment.
-
Industry-specific compliance requirements which need to be addressed in the agreement.
-
Incorporating established guidelines helps ensure the agreement's effectiveness.
How can pdfFiller help with the agreement?
Utilizing pdfFiller simplifies the creation and management of the Vulnerability Assessment Agreement Template. Through its platform, users can easily edit documents, incorporate eSignatures, and manage their paperwork collaboratively.
-
pdfFiller offers user-friendly tools for document creation and editing.
-
Users can efficiently sign and store contracts electronically.
-
Benefits of accessing documents from anywhere and collaborating in real time.
How to fill out the Vulnerability Assessment Agreement Template
-
1.Download the Vulnerability Assessment Agreement Template from pdfFiller.
-
2.Open the template using pdfFiller's online editor.
-
3.Begin by entering the date of the agreement at the top of the document.
-
4.Fill in the names and contact information of both parties involved in the assessment.
-
5.Specify the scope of the vulnerability assessment by detailing the systems or areas to be assessed.
-
6.Include any relevant deadlines for the completion of the assessment.
-
7.State the responsibilities of each party clearly to avoid any misunderstandings.
-
8.Add sections for confidentiality, data protection, and liability as necessary.
-
9.Review the entire document to ensure all information is correct and comprehensive.
-
10.Save the completed agreement and share it with the relevant parties for signature.
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.