Get the free Lost or Stolen Device Report Form
Show details
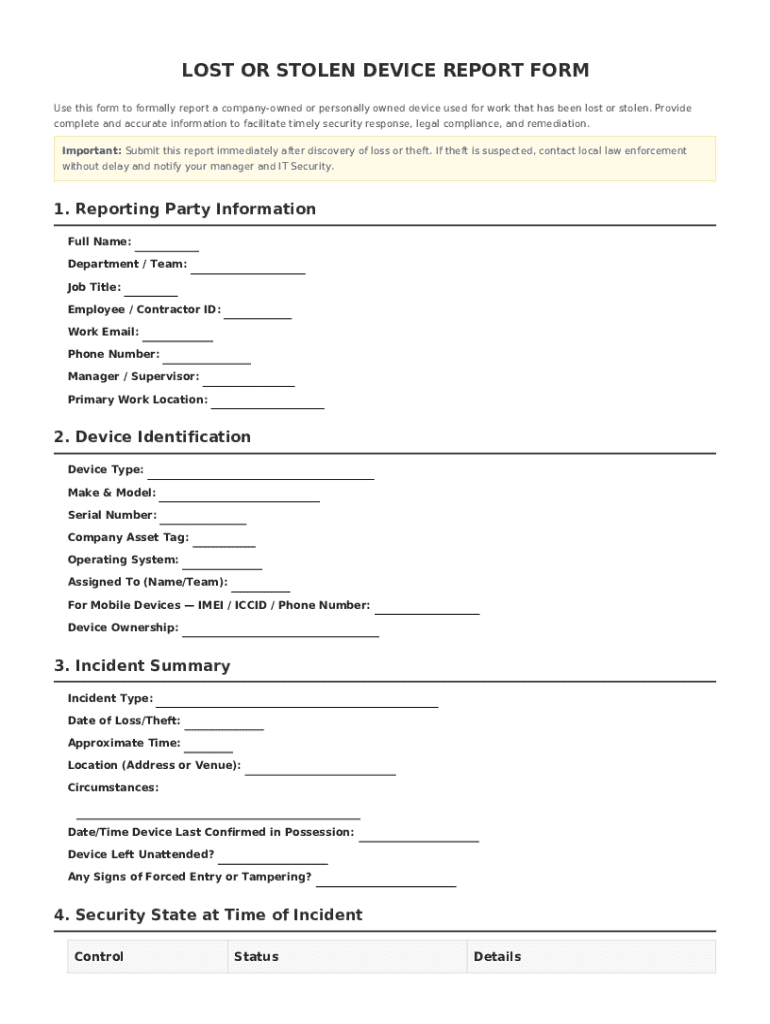
A critical internal form used to formally report a missing company-owned or authorized personal device (BYOD) that contains company data, initiating security protocols such as remote wiping and access
We are not affiliated with any brand or entity on this form
Why pdfFiller is the best tool for managing contracts
End-to-end document management
From editing and signing to collaborating and tracking, pdfFiller has all the PDF tools you need for your contract workflow.
Mobile ready
pdfFiller is cloud-based, letting you edit, sign, and share contracts from your computer, smartphone, or tablet.
Legally binding & secure
pdfFiller lets you securely manage contracts with eSignatures that comply with global laws like ESIGN and GDPR. It's also HIPAA and SOC 2 compliant.

What is lost or stolen device
A 'lost or stolen device' document is a formal declaration to report an electronic device that has been misplaced or taken without permission.
pdfFiller scores top ratings on review platforms




Who needs lost or stolen device?
Explore how professionals across industries use pdfFiller.
Guidelines for Filling Out the Lost or Stolen Device Report Form
To successfully navigate the process of reporting a lost or stolen device, it’s critical to understand the requirements and steps involved in completing the lost or stolen device form. This guide will provide you with the necessary instructions, allowing for timely and effective reporting.
-
Recognize the legal and procedural obligations you have in reporting incidents involving lost or stolen devices.
-
Collect all necessary details beforehand to expedite the completion of the form.
What is the purpose and importance of the lost or stolen device form?
Understanding the significance of timely reporting is vital. When devices are lost or stolen, quick action can prevent unauthorized access to sensitive information, ensuring compliance with corporate and legal standards.
-
It is crucial to comply with organizational and legal requirements when reporting such incidents, protecting both the employee and the organization.
-
Complete submissions enhance the organization's ability to respond to security incidents effectively, improving the chances of device recovery.
What information is required from the reporting party?
Each reporting individual must provide specific information, helping to establish accountability. Required details include full name, department, job title, and contact methods.
-
Include your full name, department, and job title to identify the primary point of contact.
-
Provide an employee or contractor ID number and work email along with your phone number and manager's information for follow-up actions.
How do you identify the lost or stolen device?
Correctly identifying the device is essential for tracking and recovery. Include details on the type of device, such as whether it’s a laptop, phone, or tablet.
-
Clearly state the make, model, serial number, and asset tag of your device to facilitate identification.
-
Providing accurate identification is crucial, increasing the chance of a successful tracking efforts.
What should be included in the incident summary for reporting?
A detailed incident summary helps in evaluating the nature of the occurrence. Clearly categorize the event as lost, suspected theft, or confirmed theft, and provide documentation to support your claims.
-
Identify the nature of the incident accurately to guide follow-up actions.
-
Include details regarding the date, time, and location of the loss along with a thorough narrative description of the events surrounding the incident.
What security state should be assessed at the time of the incident?
In assessing the security state at the time of the incident, report any implemented security controls. This information is critical for evaluating potential vulnerabilities or lapses in security.
-
Mention whether security features such as screen locks and full-disk encryption were active at the time of the device loss.
-
Evaluate the impact of device management platforms, such as Mobile Device Management (MDM), on your device's security at the time of the incident.
-
Detail if multifactor authentication was employed, as this affects the overall security level of the device.
What compliance and reporting actions must be taken?
Taking the right actions after an incident is crucial. If you suspect theft, contact law enforcement immediately, and notify your management and IT security teams.
-
If theft is suspected, it is essential to report the incident to law enforcement immediately.
-
Alert your management and IT security, ensuring they can initiate appropriate protocols for the situation.
-
Understand and execute follow-up actions required post-form submission, ensuring compliance with company policy.
How can pdfFiller facilitate seamless reporting?
pdfFiller simplifies the process of filling out the lost or stolen device form, allowing users to fill out, edit, and sign documents securely. With features like accessibility from anywhere, users can manage submissions efficiently.
-
Users can fill out forms, edit them as needed, and securely sign documents on any device.
-
Team members can collaborate and manage form submissions from any location, streamlining the reporting process.
-
pdfFiller's collaboration features facilitate shared input and feedback, improving the quality of the submissions.
What are the final steps after submission?
After filling out the lost or stolen device form, understanding the final steps aids in tracking and follow-through. Utilize pdfFiller's platform to monitor the status and engage with IT for updates.
-
Follow the outlined steps after submitting the form to ensure all protocols are adequately addressed.
-
Utilize pdfFiller's tools to monitor the status of your submission for timely updates.
-
Engage with IT for follow-up processes and updates on your reported incident.
How to fill out the lost or stolen device
-
1.Open the PDF document for the 'lost or stolen device' form.
-
2.Begin by filling in your personal information at the top, including your name, address, and contact details.
-
3.Indicate the make and model of the device that has been lost or stolen.
-
4.Provide the serial number or any identification number associated with the device.
-
5.Specify the date and location where the device was lost or stolen.
-
6.Detail any circumstances surrounding the loss or theft in the designated section.
-
7.If applicable, include the police report number or mention if it was filed with law enforcement.
-
8.Review all the information you entered for accuracy before submitting.
-
9.Sign and date the document as required at the end.
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.