Doc Application - Transport Layer Securty Online For Free
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.
0
Forms filled
0
Forms signed
0
Forms sent
Discover the simplicity of processing PDFs online
Upload your document in seconds

Fill out, edit, or eSign your PDF hassle-free

Download, export, or share your edited file instantly
Top-rated PDF software recognized for its ease of use, powerful features, and impeccable support






Every PDF tool you need to get documents done paper-free
Create & edit PDFs
Generate new PDFs from scratch or transform existing documents into reusable templates. Type anywhere on a PDF, rewrite original PDF content, insert images or graphics, redact sensitive details, and highlight important information using an intuitive online editor.
Fill out & sign PDF forms
Say goodbye to error-prone manual hassles. Complete any PDF document electronically – even while on the go. Pre-fill multiple PDFs simultaneously or extract responses from completed forms with ease.
Organize & convert PDFs
Add, remove, or rearrange pages inside your PDFs in seconds. Create new documents by merging or splitting PDFs. Instantly convert edited files to various formats when you download or export them.
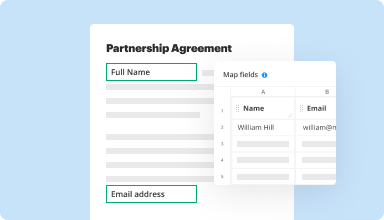
Collect data and approvals
Transform static documents into interactive fillable forms by dragging and dropping various types of fillable fields on your PDFs. Publish these forms on websites or share them via a direct link to capture data, collect signatures, and request payments.
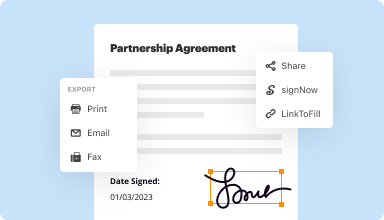
Export documents with ease
Share, email, print, fax, or download edited documents in just a few clicks. Quickly export and import documents from popular cloud storage services like Google Drive, Box, and Dropbox.
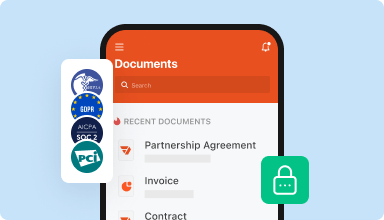
Store documents safely
Store an unlimited number of documents and templates securely in the cloud and access them from any location or device. Add an extra level of protection to documents by locking them with a password, placing them in encrypted folders, or requesting user authentication.
Customer trust by the numbers
64M+
users worldwide
4.6/5
average user rating
4M
PDFs edited per month
9 min
average to create and edit a PDF
Join 64+ million people using paperless workflows to drive productivity and cut costs
Why choose our PDF solution?
Cloud-native PDF editor
Access powerful PDF tools, as well as your documents and templates, from anywhere. No installation needed.
Top-rated for ease of use
Create, edit, and fill out PDF documents faster with an intuitive UI that only takes minutes to master.
Industry-leading customer service
Enjoy peace of mind with an award-winning customer support team always within reach.
What our customers say about pdfFiller
See for yourself by reading reviews on the most popular resources:
It was easy to use, my one complaint would be exporting one document at a time was time consuming. Wish I could have selected all documents to export one time.
2017-05-05
I was very pleased with the user friendly nature of PDFfiller. I had a situation where a documented needed to be sent ASAP, and everything went precisely as planned without minimal effort.
2018-12-20
I have had a great experience with PDF Filler. Being a computer novice however, some things were not quite as easy to find as I needed. I asked for assistance though and received it immediately. Great team !
2019-01-31
Good for quick edits and Esigs
PDF filler has helped me edit pdf's for clients, some clients want quick edits, and this program makes it very easy to do so.
I like that it is quick, simple, and functional. When you draft up a pdf to be E-signed and edited you can't ask for much more.
There's honestly not too much to dislike, they could use a UI overhaul as it feels outdated, I wish that it was free to use.
2020-02-27
Makes your work Easy, Professional and Reliable!
Efficient and compatible with many universal docs. I look forward to completing all my documents with professional results.
Monthly expenses/costs can become a concern for small business budget. It will be greatly appreciated if these costs were waived for organizations providing resources to support consumers. We work with a United Stated Private Attorney General supporting consumer claims.
2017-11-14
pdffiller.com has been phenomenal
pdffiller.com has been phenomenal. I am able to pretty much upload anything I need to fill-in and sign. This site does what other sites/apps couldn't do. Thank you!
2024-11-26
pdfFiller
I have been really satisfied with this program
I like that I can recreate forms and make them to where they can just be filled in through the computer
It was a little bit hard to figure out exactly how to get started with it but once I did it was easy
2021-12-02
Its a excellent tool which fulfill all the requirement. And tool is designed so well that easily work with. I'm really happy and glad I found this tool which made my life easy. Definitely I will recommend to my friends. Thanks
2021-06-10
had a few problems with text
had a few problems with text, once I got hang of it, it was OK, tried to add "auto-fill" for signature of doc, having troubles.
2020-05-01
Doc Application - Transport Layer Security Feature
The Transport Layer Security (TLS) feature in Doc Application ensures that your data remains safe and private during transmission. This essential tool protects your sensitive information from unauthorized access, making it a critical component for any user who values security in their digital communications.
Key Features
Encrypts data to prevent interception
Authenticates user identity for secure connections
Maintains data integrity during transfer
Supports multiple protocols for flexibility
Provides real-time monitoring of data exchanges
Use Cases and Benefits
Secure communications for financial transactions
Protection of confidential client information
Safeguarding intellectual property during sharing
Ensuring compliance with data protection regulations
Enhancing trust with customers and partners
By integrating TLS into your Doc Application, you address the common concern of data breaches during transmission. This feature not only mitigates the risk of unauthorized access but also builds confidence among users, knowing their information is secure. Embrace the reliability of TLS and strengthen your digital security with Doc Application.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What layer does the TLS protocol work?
TLS operates between the Transport layer and the Application Layer (kind of). Really it just wraps Application Layer traffic in encryption during transport. The TLS Key Exchange happens in the in between layers.
At which TCP IP layer does the TLS protocol work?
The TLS (and SSL) protocols are located between the application protocol layer and the TCP/IP layer, where they can secure and send application data to the transport layer.
At which TCP IP layer does the HTTPS protocol work?
HTTP operates at the highest layer of the TCP/IP model, the Application layer; as does the TLS security protocol (operating as a lower sublayer of the same layer), which encrypts an HTTP message prior to transmission and decrypts a message upon arrival.
Is TLS over TCP?
TLS does not require TCP, it only requires reliable transport. There is even a standard for TLS over SMTP which is another reliable transport protocol. But, if you take today's internet then you usually only have UDP and TCP as transport protocols on top of IP and from these two TCP is the only reliable one.
What is TCP TLS?
When the SSL protocol was standardized by the IETF, it was renamed to Transport Layer Security (TLS). TLS was designed to operate on top of a reliable transport protocol such as TCP. However, it has also been adapted to run over data gram protocols such as UDP.
How does TLS protocol work?
TLS uses a combination of symmetric and asymmetric cryptography, as this provides a good compromise between performance and security when transmitting data securely. The session key is then used for encrypting the data transmitted by one party, and for decrypting the data received at the other end.
Why do we need SSL TLS protocol and how it works?
It's a protocol used to encrypt and authenticate the data sent between an application (like your browser) and a web server. This leads to a more secure web for both you and the visitors to your website. SSL is closely tied to another acronym TLS. But due to security flaws, it was never released to the public.
Does TLS use AES?
TLS uses many encryption algorithms, including AES in various modes, and several hash algorithms, including those in the SHA family. TLS may also use encryption algorithms not based on a block cipher, such as RC4.
#1 usability according to G2
Try the PDF solution that respects your time.






