Docx Application - Cloud Security Trust Online For Free
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.
0
Forms filled
0
Forms signed
0
Forms sent
Discover the simplicity of processing PDFs online
Upload your document in seconds

Fill out, edit, or eSign your PDF hassle-free

Download, export, or share your edited file instantly
Top-rated PDF software recognized for its ease of use, powerful features, and impeccable support






Every PDF tool you need to get documents done paper-free
Create & edit PDFs
Generate new PDFs from scratch or transform existing documents into reusable templates. Type anywhere on a PDF, rewrite original PDF content, insert images or graphics, redact sensitive details, and highlight important information using an intuitive online editor.
Fill out & sign PDF forms
Say goodbye to error-prone manual hassles. Complete any PDF document electronically – even while on the go. Pre-fill multiple PDFs simultaneously or extract responses from completed forms with ease.
Organize & convert PDFs
Add, remove, or rearrange pages inside your PDFs in seconds. Create new documents by merging or splitting PDFs. Instantly convert edited files to various formats when you download or export them.
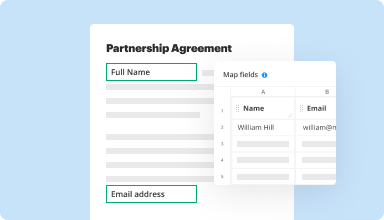
Collect data and approvals
Transform static documents into interactive fillable forms by dragging and dropping various types of fillable fields on your PDFs. Publish these forms on websites or share them via a direct link to capture data, collect signatures, and request payments.
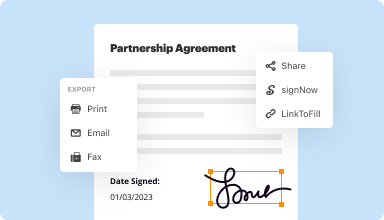
Export documents with ease
Share, email, print, fax, or download edited documents in just a few clicks. Quickly export and import documents from popular cloud storage services like Google Drive, Box, and Dropbox.
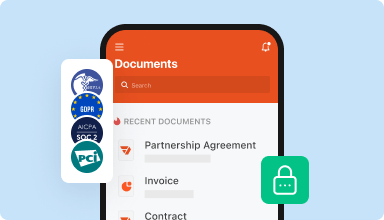
Store documents safely
Store an unlimited number of documents and templates securely in the cloud and access them from any location or device. Add an extra level of protection to documents by locking them with a password, placing them in encrypted folders, or requesting user authentication.
Customer trust by the numbers
64M+
users worldwide
4.6/5
average user rating
4M
PDFs edited per month
9 min
average to create and edit a PDF
Join 64+ million people using paperless workflows to drive productivity and cut costs
Why choose our PDF solution?
Cloud-native PDF editor
Access powerful PDF tools, as well as your documents and templates, from anywhere. No installation needed.
Top-rated for ease of use
Create, edit, and fill out PDF documents faster with an intuitive UI that only takes minutes to master.
Industry-leading customer service
Enjoy peace of mind with an award-winning customer support team always within reach.
What our customers say about pdfFiller
See for yourself by reading reviews on the most popular resources:
I completed a passport application. The document was easy to fill & very professional in quality which made it very easy to be understood during processing.
2015-11-25
I received some paperwork that needed to be signed and sent back to sender in a timely manner. PDFfiller was the only way I could do this. I had no access to a printer or fax machine. I'm trying to learn all of the use of the PDFfiller. I am currently trying to learn how to download some of my saved papers and sign them, then send them out. I forgot how I did it yesterday.
2017-11-08
Directions for completing fillable forms were very clear, easy to follow, and concise. This is a great product for someone who is in need of fillable forms on a regular basis. Highly recommended.
2019-05-05
Awesome experience with Alice
Awesome experience with Alice. She guided me through step by step. Made it simple for me. Very knowledgeable, experienced, and courteous. 10+ out of 10 rating.
2019-02-28
Excellent Tool for Document Management
I had a great experience using pdfFiller. The platform is intuitive and user-friendly, making it easy to manage, edit, and share documents. The range of features offered is impressive, from converting files to creating templates. I highly recommend pdfFiller for anyone looking for a comprehensive document management solution. Keep up the great work!
2024-08-03
My experience with PdfFiller was great
My experience with PdfFiller was great. I use PdfFiller as a cloud storage for backup files, in addition I can multitask by retrieving signed documents and save them in my signed doc. file for later.
2024-03-07
pdfFiller is a useful PDF editor and e-signing tool
pdfFiller is a very easy tool to use if you find yourself needing to sign or edit PDF documents, but don't want to spend a lot of money on more expensive software.
I appreciate how easy pdfFiller makes it to electronically sign documents or edit and convert PDF files. The instructions are easy to follow and within minutes you can merge, split or sign documents without to much effort.
All in all I can't complain about the software. There were a few instances where I would download my signed document for it to turn out completely blank (in the free version), but then I'd just download it again and that usually solves the issue.
2022-11-03
It is an excellent experience with…
It is an excellent experience with pdFiller. I was attended to by an experienced customer advisor. The service I received is beyond my expectation. Please I will recommend pdFiller for your needs
2021-07-27
Became a notary and I love it! Very easy to use! Has all the tools necessary to get the job done. Not just for notary, even can be used for personal use as well. Amazing!
2021-02-09
Docx Application - Cloud Security Trust Feature
The Cloud Security Trust feature in the Docx Application ensures your documents remain safe and confidential. With increasing cybersecurity threats, trust in your cloud solutions is essential. This feature provides you with robust security tools to protect your valuable information.
Key Features
End-to-end encryption for secure document storage
User authentication protocols to control access
Automatic backups to prevent data loss
Real-time activity monitoring to detect suspicious actions
Regular security updates to combat new threats
Potential Use Cases and Benefits
Businesses can secure sensitive client data with confidence
Educational institutions can protect academic records and research papers
Freelancers can safeguard project files shared with clients
Healthcare providers can maintain patient confidentiality and comply with regulations
Non-profits can ensure donor information stays private and secure
With the Cloud Security Trust feature, you can address concerns about data breaches and unauthorized access. This feature allows you to focus on your work, knowing your documents are protected. Trust in your cloud solution to keep your information safe, and feel secure in your digital communications.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What is cloud application security?
Cloud application security is the security of only the application layer of IaaS, PaaS, and SaaS: This type of security consists in properly programming cloud applications to avoid vulnerabilities such as SQL injection, cross-site scripting, weak authentication and session management, cross site request forgery, etc.
How do I secure my cloud application?
Integrate cloud-based identity management solutions with enterprise security from the outset.
Focus on the design and architecture of your security solution first; select the technology second.
Build security testing into your DevOps automation.
Consider performance in your design.
Can my cloud be hacked?
As hackers demonstrated through the celebrity iCloud breach, poor password security can give cybercriminals an all-access pass to your private data. However, the biggest cause of concern for Cloud storage isn't hacked data, it's lost data.
How secure is WD My Cloud home?
To stay safe, WD says My Cloud owners should disable the Dashboard Cloud access and disable any port-forwarding functions. The company says a future update will address device exploitation by a hacker with access to the owner's local network, or if the user has enabled certain My Cloud settings.
Is my cloud encrypted?
One's connection to the MyCloud.com web portal is also encrypted (HTTPS). Using a direct link to individual files (and possibly folders) is also encrypted (HTTPS). SSH access to the Cloud can be enabled for both local and remote access.
Is it safe to store sensitive documents in the cloud?
Yes, your data is relatively safe in the cloud likely much more so than on your own hard drive. In addition, files are easy to access and maintain. But if you have sensitive data you'd like to keep from prying eyes probably best to store in a hard drive that remains disconnected from your home computer.
How do you manage cloud security?
View all cloud services in use and assess their risk.
Audit and adjust native security settings.
Use Data Loss Prevention to prevent theft.
Encrypt data with your own keys.
Block sharing with unknown devices or unauthorized users.
What is security management in cloud computing?
Cloud security management for software-as-a-service (SaaS) The most common way to manage data security and user access in cloud computing is through the use of a Cloud Access Security Broker (CASE). This technology allows you to see all your cloud applications in use and to apply security policy across them.
#1 usability according to G2
Try the PDF solution that respects your time.






