Form Software - SOC-2 Online For Free
Discover the simplicity of processing PDFs online








Every PDF tool you need to get documents done paper-free
Create & edit PDFs
Fill out & sign PDF forms
Organize & convert PDFs
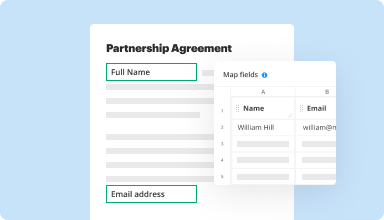
Collect data and approvals
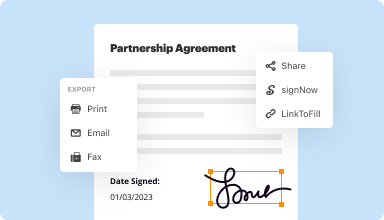
Export documents with ease
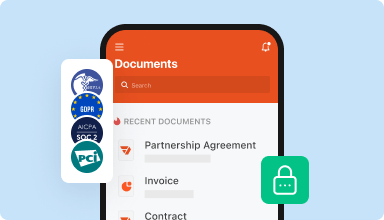
Store documents safely
Customer trust by the numbers
Why choose our PDF solution?
Cloud-native PDF editor
Top-rated for ease of use
Industry-leading customer service
What our customers say about pdfFiller
Form Software - SOC-2 Feature
Manage your security and compliance with expertise using the SOC-2 feature of Form Software. This tool helps you build trust with your clients by showcasing your commitment to data protection and compliance standards.
Key Features
Potential Use Cases and Benefits
With the SOC-2 feature, you can address compliance challenges directly. It allows you to focus on your core business while ensuring that security practices meet the expectations of your clients. You will find that this tool not only safeguards your data but also opens doors to new opportunities.
How to Use the Form Software - SOC-2 Feature
The Form Software - SOC-2 feature is a powerful tool that allows you to securely fill out and manage forms with ease. Follow these step-by-step instructions to make the most of this feature:
By following these simple steps, you can efficiently utilize the Form Software - SOC-2 feature and streamline your form-filling process.
For pdfFiller’s FAQs
#1 usability according to G2






