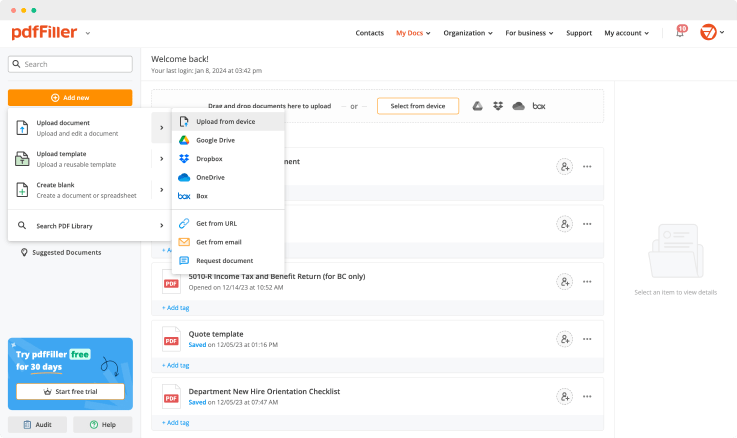
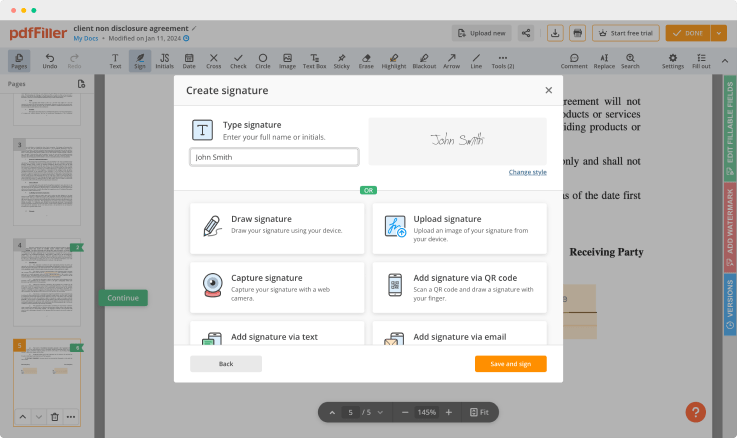
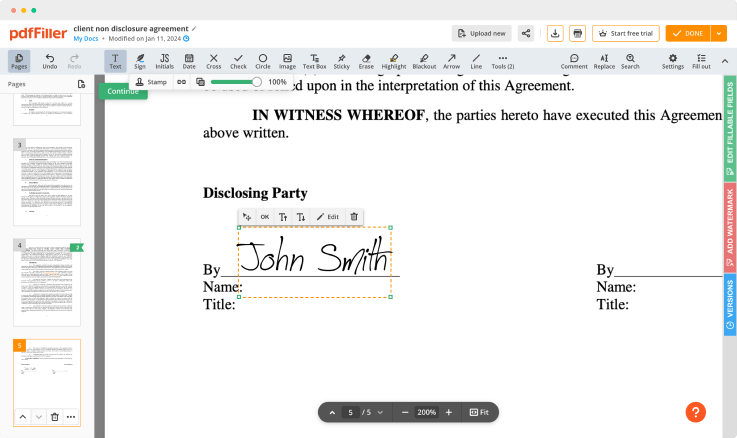
Lock Table Log For Free




Join the world’s largest companies









Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution

Unlimited document storage

Widely recognized ease of use

Reusable templates & forms library
The benefits of electronic signatures

Efficiency

Accessibility

Cost savings

Security

Legality

Sustainability
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance

SOC 2 Type II Certified

PCI DSS certification

HIPAA compliance

CCPA compliance
Lock Table Log Feature
The Lock Table Log feature provides essential support in managing concurrent access to your database. It ensures data integrity and prevents conflicts, allowing your applications to operate smoothly. With this feature, you can confidently control how your data is accessed and modified.
Key Features
Potential Use Cases and Benefits
In today’s fast-paced digital world, reliable data management is crucial. The Lock Table Log feature addresses your need for a secure and efficient system. By preventing conflicts and ensuring that only one process accesses the data at a time, it substantially reduces the risk of errors. This allows you to focus on delivering quality applications, while we handle the complexities of data management.
Instructions and Help about Lock Table Log For Free
Lock Table Log: easy document editing
The PDF is a popular document format for a variety of reasons. PDFs are accessible from any device to share them between devices with different display resolution and settings. It will keep the same layout no matter you open it on Mac computer or an Android device.
Data safety is the key reason users choose PDF files to share and store data. That’s why it’s essential to get a secure editing tool, especially when working online. PDF files are not only password-protected, but analytics provided by an editing service allows document owners to identify those who’ve read their documents and track potential breaches in security.
pdfFiller is an online editor that lets you create, modify, sign, and send your PDFs using one browser tab. Thanks to the numerous integrations with the most popular solutions for businesses, you can upload an information from any system and continue where you left off. Work with the completed document yourself or share it with others by any convenient way — you'll get notified when someone opens and fills out it.
Use editing features to type in text, annotate and highlight. Change a template’s page order. Once a document is completed, download it to your device or save it to the third-party integration cloud. Collaborate with other users to complete the document and request an attachment. Add and edit visual content. Add fillable fields and send for signing.
Get your documents completed in four simple steps:
For pdfFiller’s FAQs
Ready to try pdfFiller's? Lock Table Log