Protected Company Notification For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

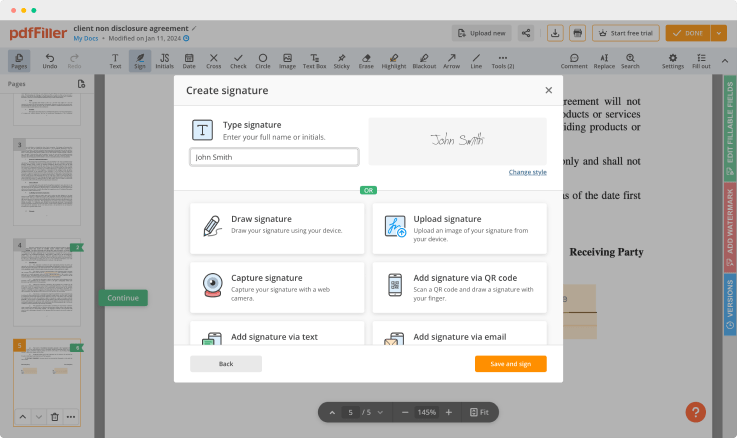
Generate your customized signature

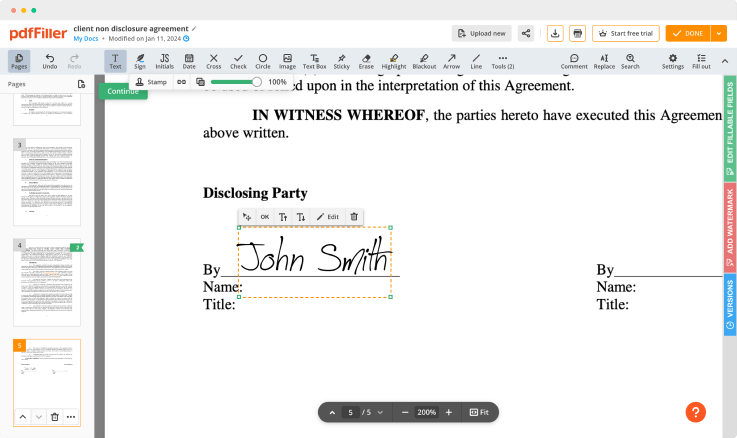
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Protected Company Notification Feature
The Protected Company Notification feature ensures that your organization stays informed about important updates and changes. This tool is designed to streamline communication and keep all team members aligned with the latest information.
Key Features
Real-time notifications for critical updates
Customizable alerts based on user preferences
Secure communication channels to protect sensitive information
Integration with various platforms for seamless use
User-friendly interface for easy access and management
Potential Use Cases and Benefits
Keep teams informed about policy changes or new procedures
Notify employees of security incidents or alerts promptly
Enhance collaboration by sharing updates across departments
Reduce the risk of miscommunication in fast-paced environments
Improve employee engagement with regular updates
By implementing the Protected Company Notification feature, your organization can solve the challenge of fragmentation in information sharing. This solution ensures that everyone remains up to date with the latest information, which fosters a cohesive working environment and enhances operational efficiency.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What should you do if you suspect a data breach?
Address the Breach and Contact your IT Support if you suspect that there is a data breach, the most important thing to do is address it. Uncover the Cause of the Breach once IT support is on hand to check the situation, they will be able to uncover the cause of the breach.
What should you do if you suspect a data breach has occurred?
Typical Data Breach Scenarios. How Often Breaches Occur. Determine What Data Is at Risk. Consult with an Appropriate IT Expert. Consider Notifying Insurance Company. Identify Applicable Breach Notification Obligations. Consult with Legal Counsel for Guidance as Needed. Bottom Line.
What data breaches need to be reported?
Data breaches only need to be reported if they pose a risk to the rights and freedoms of natural living persons. This generally refers to the possibility of affected individuals facing economic or social damage (such as discrimination), reputational damage or financial losses.
How does a data breach affect me?
Recent Data Breaches Sure, gaining access to information like names, email addresses, and passwords might not seem as harmful as someone having your Social Security number. But any data breach can leave you at risk of identity theft if the hackers want to use that information against you.
What happens when your data is breached?
A data breach occurs when a cybercriminal successfully infiltrates a data source and extracts sensitive information. This can be done physically by accessing a computer or network to steal local files or by bypassing network security remotely. The latter is often the method used to target companies.
What happens if there is a data breach?
A personal data breach occurs when there's a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data processed. If this happens, the organization holding the personal data must notify the supervisory authority without undue delay.
What is the most common cause of a data breach?
Hacking attacks may well be the most common cause of a data breach, but it is often a weak or lost password that is the vulnerability that is being exploited by the opportunist hacker ms 2016. Stats show that 4 in 5 breaches classified as a hack in 2012 were in-part caused by weak or lost (stolen) passwords!
How do you handle a data breach?
Stop the breach. Assess the damage. Notify those affected. Security audit. Update your recovery plan to prepare for future attacks. Train your employees. Protect the data. Enforce strong passwords.
Ready to try pdfFiller's? Protected Company Notification
Upload a document and create your digital autograph now.