Protected Compulsory Field Paper For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
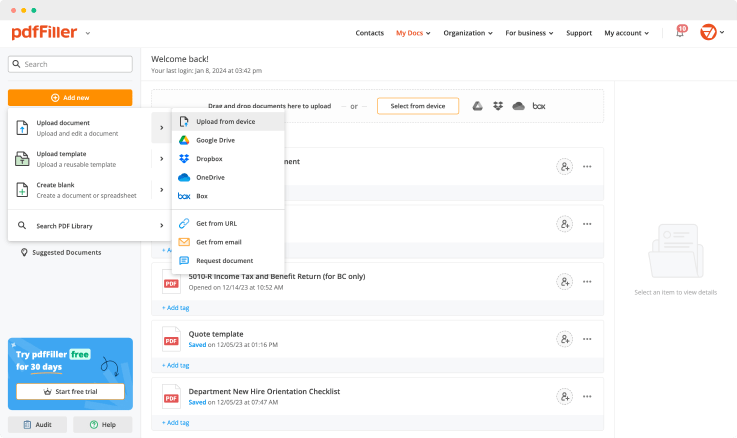
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

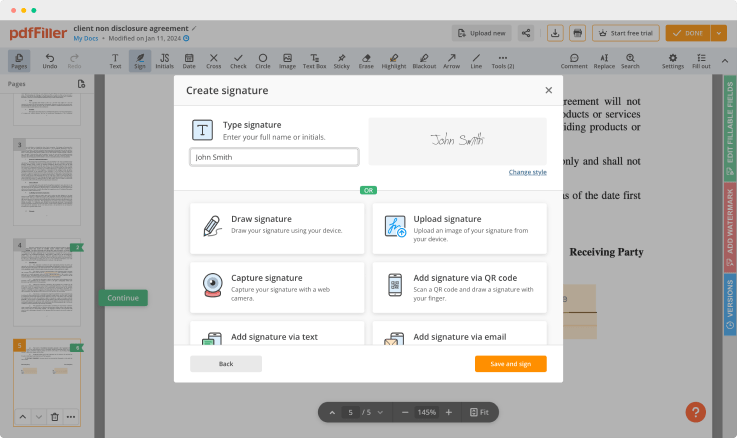
Generate your customized signature

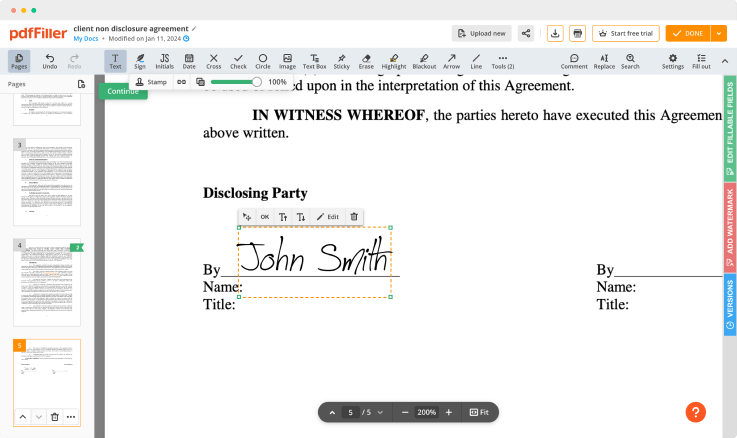
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Protected Compulsory Field Paper Feature
The Protected Compulsory Field Paper feature offers a reliable way to secure your important data while ensuring compliance with necessary requirements. This tool provides a seamless experience for users seeking to protect sensitive information.
Key Features
Data encryption for enhanced security
Customizable fields to meet your specific needs
User-friendly interface for easy navigation
Automatic backups to prevent data loss
Compliance with industry regulations
Potential Use Cases and Benefits
Secure storage of personal information for businesses
Protection of sensitive documents in healthcare
Safeguarding client data in legal firms
Enhanced data management for educational institutions
Streamlined compliance tracking for finance departments
By using the Protected Compulsory Field Paper feature, you can address your data security concerns effectively. This function enables you to store and manage sensitive information safely while adhering to legal obligations. With its customizable options, you can tailor the feature to fit your organization's specific requirements, making it a valuable asset for any industry.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What is the correct order of steps that must be taken if there is a breach of HIPAA information or data?
Stop the breach. Terminate improper access to PHI. Retrieve any PHI that was improperly disclosed. And obtain assurances from recipients that they have not used or disclosed the PHI, and/or will not, further use or disclose PHI that was improperly accessed. Document your actions and the recipient's response.
What is the correct order of steps that must be taken if there is a breach of HIPAA information or data?
Stop the breach. Terminate improper access to PHI. Retrieve any PHI that was improperly disclosed. And obtain assurances from recipients that they have not used or disclosed the PHI, and/or will not, further use or disclose PHI that was improperly accessed. Document your actions and the recipient's response.
How soon must a HIPAA breach be reported?
Data Breaches Experienced by HIPAA Business Associates Any breach of unsecured protected health information must be reported to the covered entity within 60 days of the discovery of a breach. While this is the absolute deadline, business associates must not delay notification unnecessarily.
What is the procedure if a breach of patient information occurs?
If a breach affects 500 or more individuals, covered entities must notify the Secretary without unreasonable delay and in no case later than 60 days following a breach. If, however, a breach affects fewer than 500 individuals, the covered entity may notify the Secretary of such breaches on an annual basis.
How do you handle a HIPAA violation?
Step 1: Timely Response to Patient Complaints. Step 2: Conduct an Adequate Investigation. Step 3: Correct and Mitigate Harmful Effects. Step 4: Determine if there is a Reportable Breach. Step 5: Involve HR to Determine Disciplinary Measures. Step 6: Get your Documents in Order. Step 7: Follow up with the Patient.
What steps need to be taken to notify a patient of a HIPAA violation?
Step 1: Timely Response to Patient Complaints. Step 2: Conduct an Adequate Investigation. Step 3: Correct and Mitigate Harmful Effects. Step 4: Determine if there is a Reportable Breach. Step 5: Involve HR to Determine Disciplinary Measures. Step 6: Get your Documents in Order. Step 7: Follow up with the Patient.
What do you do in case of HIPAA breach?
Covered entities will notify the Secretary by visiting the HHS website and filling out and electronically submitting a breach report form. If a breach affects 500 or more individuals, covered entities must notify the Secretary without unreasonable delay and in no case later than 60 days following a breach.
What counts as a HIPAA violation?
There are hundreds of ways that HIPAA Rules can be violated, although the most common HIPAA violations are: Impermissible disclosures of protected health information (PHI) Unauthorized accessing of PHI. Failure to manage risks to the confidentiality, integrity, and availability of PHI.
Ready to try pdfFiller's? Protected Compulsory Field Paper
Upload a document and create your digital autograph now.