Protected Us Phone Title For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
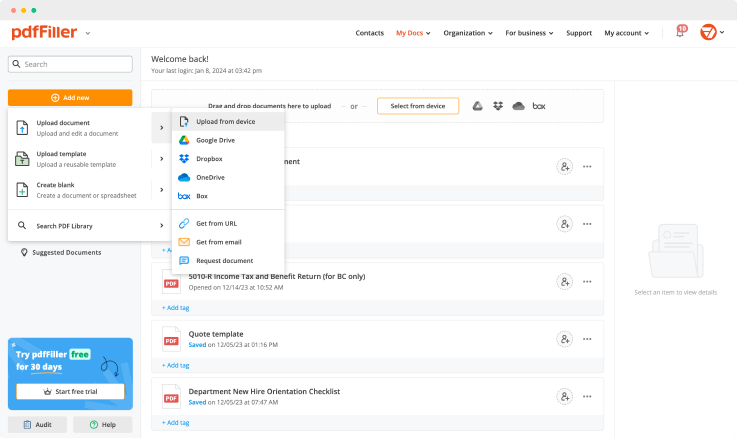
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

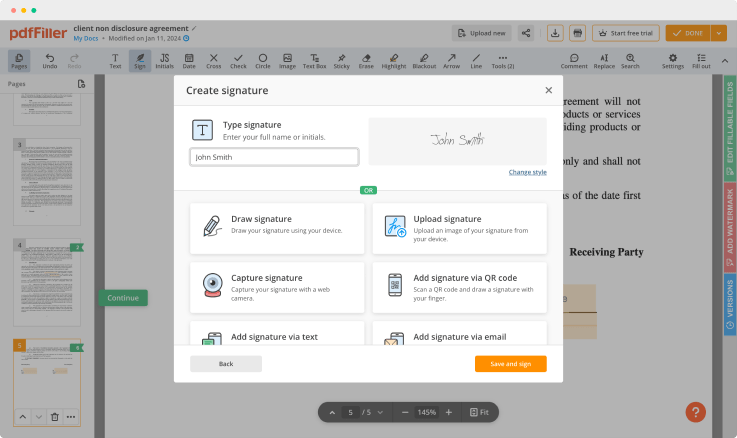
Generate your customized signature

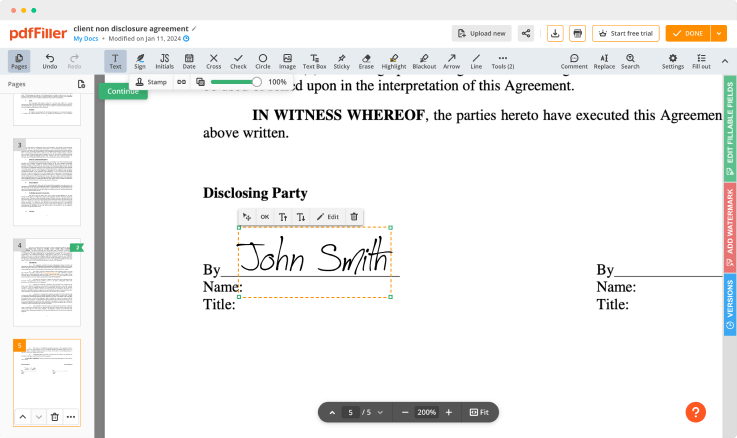
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Protected Us Phone Title Feature
Introducing the Protected Us Phone Title feature, designed to enhance your phone security and provide peace of mind. This innovative feature safeguards your personal information and keeps your device safe from unauthorized access. Let's explore what this feature has to offer.
Key Features
Provides enhanced security for your phone data
Offers quick access to emergency contacts
Enables location tracking for lost or stolen devices
Includes customizable protection settings
Seamlessly integrates with your existing phone features
Potential Use Cases and Benefits
Ideal for individuals who frequently travel or are in public places
Useful for parents wanting to keep their children's devices secure
Great for professionals who handle sensitive information
Helpful for anyone wishing to locate a lost phone quickly
Perfect for users wanting peace of mind regarding their phone's security
The Protected Us Phone Title feature addresses your need for security and convenience. By implementing this feature, you can protect your data, ensuring that only authorized individuals access it. Moreover, it helps you stay connected with emergency contacts and secure your device's location, making it a reliable companion in any situation.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What is considered a protected computer?
The definition of “protected computer” includes government computers, financial institution computers, and any computer “which is used in interstate or foreign commerce or communications.” It also specifically includes those computers used in “foreign” communications.
What is a protected computer under the CAA?
A protected computer under the CAA is any computer that is connected to a government network, or is used for interstate or foreign commerce or communication. So if the computer is connected to the Internet, it is protected.
What is the main federal law used to prosecute cybercrime?
The federal Computer Fraud and Abuse Act (CAA), 18 U.S.C. § 1030, is the primary statutory mechanism for prosecuting cybercrime, and provides for both criminal and civil penalties.
What are the 4 major categories of computer crimes?
For a new breed of criminals, computers are rapidly becoming the “weapon of choice.” There are four major categories of computer crime: internal computer crimes--trojan horses, logic bombs, trap doors, worms, and viruses. Telecommunications crimes--phreaking and hacking. Computer manipulation crimes that result in
What is unlawful use of a computer?
--A person commits the offense of unlawful use of a computer if he: (1) accesses or exceeds authorization to access, alters, damages or destroys any computer, computer system, computer network, computer software, computer program, computer database, World Wide Web site or telecommunication device or any part thereof
What is considered a computer crime?
Computer crime is an act performed by a knowledgeable computer user, sometimes referred to as a hacker that illegally browses or steals a company's or individual's private information. In some cases, this person or group of individuals may be malicious and destroy or otherwise corrupt the computer or data files.
Which federal law is most commonly used to prosecute hackers?
The Computer Fraud and Abuse Act of 1986, enacted into law today as United States Code Title 18 Section 1030, is the primary federal law governing cybercrime in the United States today. It has been used in such famous cases as the Morris Worm and in the prosecution of notorious TAX hacker Albert Gonzalez.
What are examples of works not protected by copyright?
For example: choreographic works that have not been notated or recorded, or improvisational speeches or performances that have not been written or recorded are both ineligible for copyright protection. For many years, unrecorded music concerts were also unprotected by copyright law because they were not fixed.
Ready to try pdfFiller's? Protected Us Phone Title
Upload a document and create your digital autograph now.