Reliable Highlight Log For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

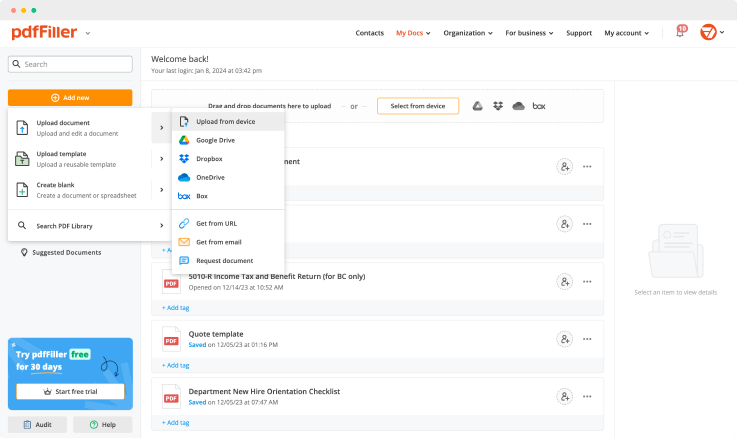
Upload a document

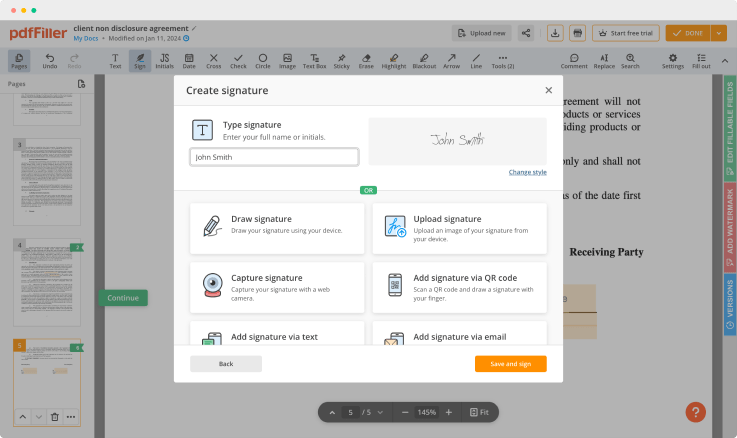
Generate your customized signature

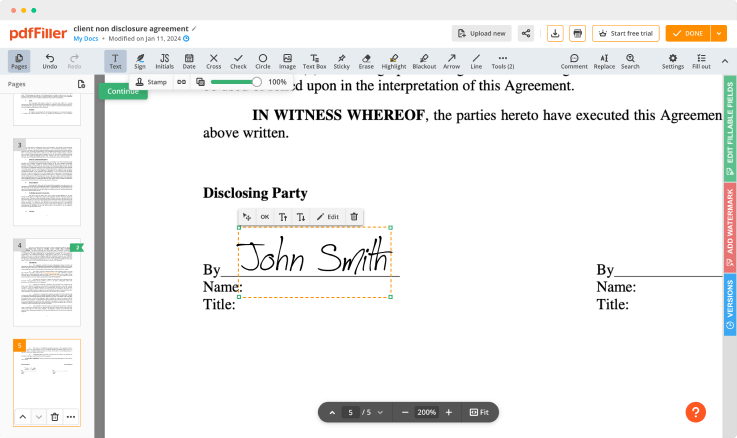
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Reliable Highlight Log Feature
The Reliable Highlight Log feature simplifies the way you track important information. It ensures that you capture key moments and details in an organized manner, making your workflow smoother and more efficient.
Key Features
Easy tagging for quick reference
User-friendly interface for seamless navigation
Automatic synchronization across devices
Customizable log entries to fit your needs
Search functionality to quickly locate highlights
Use Cases and Benefits
Perfect for students to summarize lecture notes
Ideal for professionals managing projects and tasks
Helpful for researchers tracking important findings
Great for writers organizing inspiration and ideas
Convenient for anyone needing to remember crucial information
The Reliable Highlight Log feature addresses your need for clarity. It organizes your thoughts and important details, keeping them easily accessible. Now, you can focus on what matters most, without worrying about losing vital information. By integrating this feature into your routine, you enhance productivity and ensure that you never miss a key point again.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How do you manage logs?
Set a Strategy. Don't log blindly. Structure Your Log Data. In addition, developing a logging strategy, it's important to consider the format of your logs. Separate and Centralize your Log Data. Practice End-to-End Logging. Correlate Data Sources. Use Unique Identifiers. Add Context. Perform Real-Time Monitoring.
What is log storage and management?
Log management is the collective processes and policies used to administer and facilitate the generation, transmission, analysis, storage, archiving and ultimate disposal of the large volumes of log data created within an information system. Virtually all software applications and systems produce log files.
What are the key benefits of Log Management & Monitoring?
Resource Management Monitoring across systems to detect particular log events and patterns in log data. Monitoring in real-time for anomalies or inactivity to gauge system health. Identifying performance or configuration issues. Drilling down on data to gain insight and perform root cause analysis when failures occur.
Why are system logs important?
It's important to review your logs constantly because they will show you any suspicious activity happening in your system. Logs are important for security purposes because they are the first indicators that something is wrong. When you review them regularly, you give yourself the opportunity to nip attacks in the bud.
How often should logs be reviewed?
To be precise under the PCI DSS Requirement 10, which is dedicated to logging and log management, logs for all system components must be reviewed at least daily.
What is a control log?
Log management is a security control which addresses all system and network logs. Here's a high-level overview of how logs work: each event in a network generates data, and that information then makes its way into the logs, records which are produced by operating systems, applications and other devices.
What is a change control log?
A change log, change management log, change order log or change control log template whatever you call ITIS a document that allows you to capture change as it happens and track it throughout the project until the issue raised has been put to bed.
Why are logs important in network security?
From a security point of view, the purpose of a log is to act as a red flag when something bad is happening. Reviewing logs regularly could help identify malicious attacks on your system. Given the large of amount of log data generated by systems, it is impractical to review all of these logs manually each day.
Ready to try pdfFiller's? Reliable Highlight Log
Upload a document and create your digital autograph now.