Reliable Recommended Field Log For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

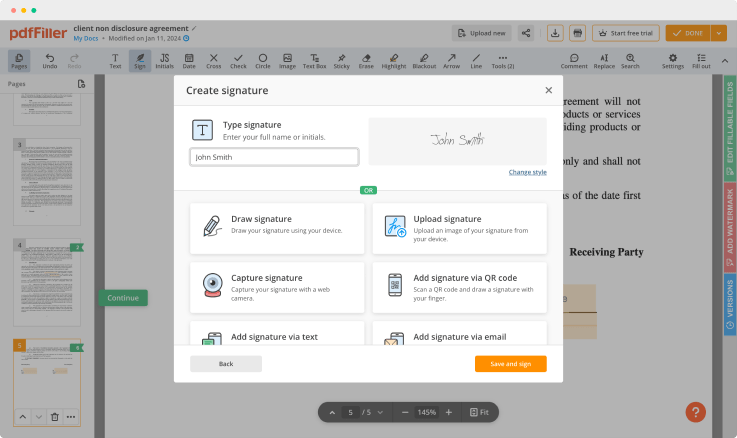
Generate your customized signature

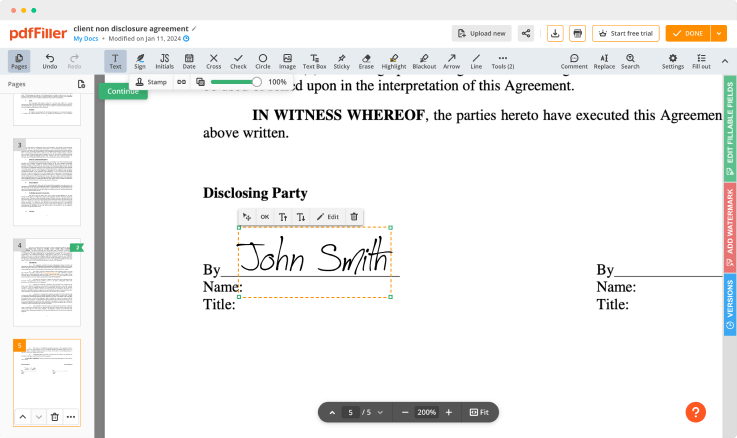
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Reliable Recommended Field Log Feature
The Reliable Recommended Field Log is designed for professionals who need an efficient way to record data in the field. This feature streamlines your workflow and ensures accuracy, making it easier for you to focus on your tasks.
Key Features
User-friendly interface for quick data entry
Customizable fields to suit your specific needs
Offline access for remote locations
Automatic data syncing when connected to the internet
Enhanced security to protect your information
Potential Use Cases and Benefits
Fieldwork in agriculture to track crop conditions
Construction sites for monitoring progress and materials
Environmental studies to record data distances from urban areas
Surveys for real estate assessments and planning
Maintenance logs for equipment tracking and servicing
This feature solves your problem by minimizing errors and improving data integrity. With its customizable options, you can adapt the log to your specific tasks. Whether you are in a rural area or a bustling job site, you maintain access to your essential information. Make your fieldwork more organized and efficient with the Reliable Recommended Field Log.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How do you make a good log?
Use a standard and easily configurable logging framework. Use a logging framework with flexible output options. Use a standard structured format like JSON. Create a standard schema for your fields. Don't let logging block your application. Avoid vendor lock-in.
How do you write a good log?
Don't Write Logs by Yourself (AKA Don't Reinvent the Wheel) Log at the Proper Level. Employ the Proper Log Category. Write Meaningful Log Messages. Write Log Messages in English. Add Context to Your Log Messages. Log in Machine Parseable Format. But Make the Logs Human-Readable as Well.
What should a log file contain?
Log files created by software installers typically contain a list of files that were added or copied to the hard drive during the installation process. They may also include the date and time the files were installed, as well as the directory where each file was placed.
What should be logged in a web application?
Some application events should be logged: For major components of an application we may log lifecycle events like start, stop and restart. Some security-related events may be logged such as unauthorized URL access attempts, user logins etc. Some resource thresholds may be exceeded and should also be logged.
How do I log in to Microservices?
Correlate Requests With a Unique ID. Include a Unique ID in the Response. Send Logs to a Centralized Location. Structure Your Log Data. Add Context to Every Request. Write Logs to Local Storage. Add Traces Where It Matters.
What is audit logging in Microservices?
There are two main areas of concern in APIs and Microservices that need a set of audit and logging capabilities. These allow the user to get both a horizontal end to end audit of a request and a vertical audit of event handling within a set of containers servicing a specific API or microservice in the ecosystem.
What is correlation ID in Microservices?
A correlation ID uniquely identifies each 'customer order', or the equivalent in your system. Similarly, web-based applications have 'user requests', for each user interaction. Once you have a correlation ID, you include it in every log message and network request, such as HTTP requests to microservices.
What are the ways with which Microservices can communicate with each other?
The most common type is single-receiver communication with a synchronous protocol like HTTP/HTTPS when invoking a regular Web API HTTP service. Microservices also typically use messaging protocols for asynchronous communication between microservices.
Ready to try pdfFiller's? Reliable Recommended Field Log
Upload a document and create your digital autograph now.