Safeguard Break Attestation For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

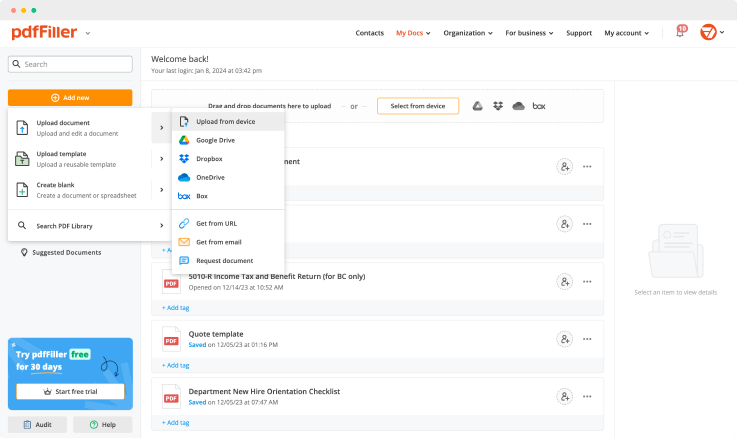
Upload a document

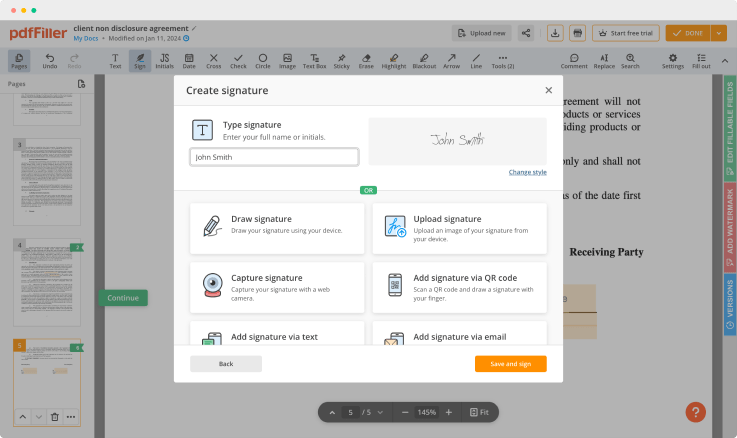
Generate your customized signature

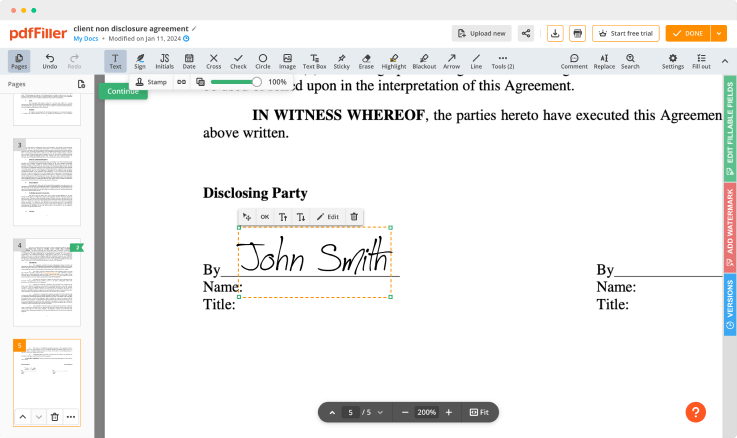
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Safeguard Break Attestation Feature
The Safeguard Break Attestation feature offers a robust solution for ensuring the transparency and accountability of your break times. By using this tool, you can effectively manage and document breaks in your work environment, leading to enhanced trust and compliance.
Key Features
Real-time tracking of employee breaks
User-friendly interface for easy access
Automatic notifications for break schedules
Flexible reporting options for management
Integration with existing company systems
Potential Use Cases and Benefits
Ensure compliance with labor regulations
Boost employee satisfaction with clear break policies
Reduce conflicts between management and staff regarding break times
Provide data insights for optimizing work schedules
Enhance overall productivity by minimizing interruptions
By implementing the Safeguard Break Attestation feature, you can address common challenges related to break management. This solution helps you establish clear guidelines that empower your staff while also meeting compliance requirements. Experience increased transparency, and ultimately, foster a more productive work environment.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
What is remote attestation?
Remote attestation is a method by which a host (client) authenticates its hardware and software configuration to a remote host (server). The goal of remote attestation is to enable a remote system (challenger) to determine the level of trust in the integrity of platform of another system (at testator).
What is attestation in security?
Begin Learning Cybersecurity for FREE Now! Attestation is the formal process of witnessing the signing of a document, then the witness adds his signature to verify the document was properly signed by those bound obligated to its contents.
What is device attestation?
Key attestation aims to provide a way to strongly determine if an asymmetric key pair is hardware-backed, what the properties of the key are, and what constraints are applied to its usage. ID attestation allows the device to provide proof of its hardware identifiers, such as serial number or IMEI.
How does remote attestation work?
Remote attestation is a method by which a host (client) authenticates its hardware and software configuration to a remote host (server). The goal of remote attestation is to enable a remote system (challenger) to determine the level of trust in the integrity of platform of another system (at testator).
What is Attestation Identity Key?
An Attestation Identity Key is a special purpose TPM-resident RSA key that is used to provide platform authentication based on the attestation capability of the TPM.
What is Endorsement Key?
The endorsement key is an encryption key that is permanently embedded in the Trusted Platform Module (TPM) security hardware, generally at the time of manufacture. TPM operations that involve signing pieces of data can make use of the endorsement key to allow other components to verify that the data can be trusted.
What is TPM attestation?
TPM key attestation is the ability of the entity requesting a certificate to cryptographically prove to a CA that the RSA key in the certificate request is protected by either “a” or “the” TPM that the CA trusts. The TPM trust model is discussed more in the Deployment overview section later in this topic.
What is sealed storage?
Sealed Storage is a cryptographic data protection facility that is conventionally implemented using a pair of operations called Seal (used to protect data) and Unseal (used to protect data).
Ready to try pdfFiller's? Safeguard Break Attestation
Upload a document and create your digital autograph now.