Secure Hour Article For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

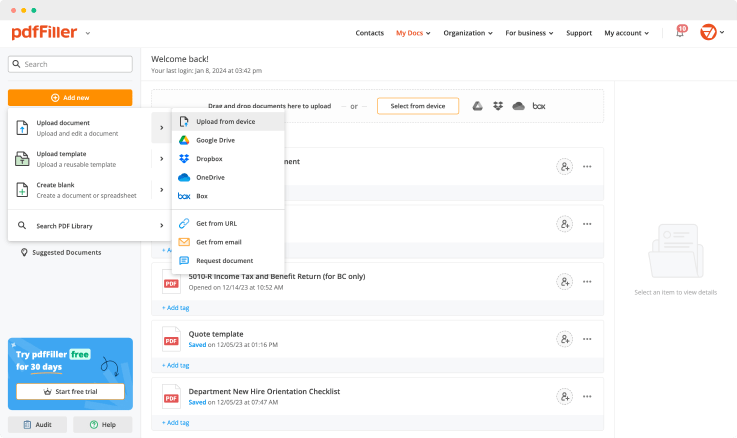
Upload a document

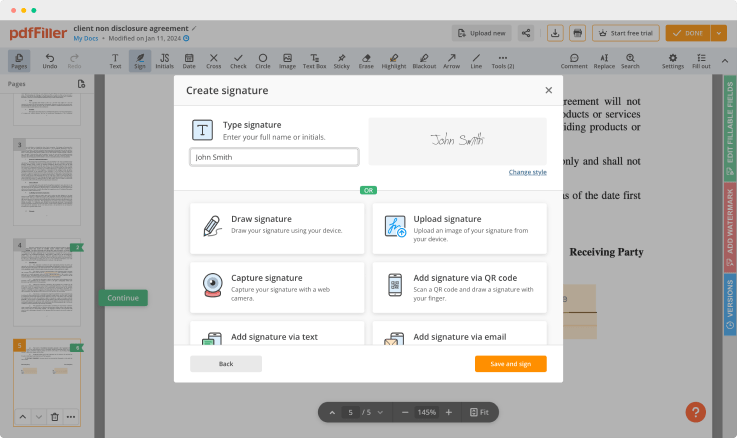
Generate your customized signature

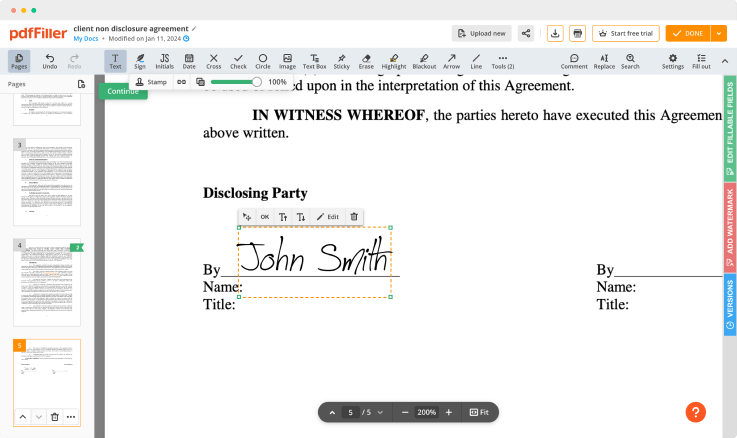
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Secure Hour Article Feature
The Secure Hour Article feature offers a reliable solution for protecting your valuable content. With this feature, you can ensure that your articles are accessible only to authorized users, enhancing your content's security.
Key Features
User authentication to restrict access
Customizable permissions for different user roles
Track user activity for security purposes
Simple integration with existing platforms
Mobile-friendly access for on-the-go users
Potential Use Cases and Benefits
Publish sensitive information without fear of unauthorized access
Share articles with a select audience, such as team members or clients
Protect intellectual property and proprietary content
Ensure compliance with data privacy regulations
Enhance user trust by displaying commitment to content security
By implementing the Secure Hour Article feature, you can address your concerns about content safety. This tool safeguards your articles, allowing you to focus on creating without worrying about exposure. You can build and maintain a trusted environment for your readers while maximizing your content's potential.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How can I secure my personal data?
Be Alert to Impersonators. Safely Dispose of Personal Information. Encrypt Your Data. Keep Passwords Private. Don't Overshare on Social Networking Sites. Use Security Software. Avoid Phishing Emails. Be Wise About Wi-Fi.
How can I protect my Internet privacy?
Limit the personal information you share on social media. Browse in incognito or private mode. Use a different search engine. Use a virtual private network. Be careful where you click. Secure your mobile devices, too. Use quality antivirus software.
How can you protect your data on Internet?
Review and secure your social media accounts. Change your passwords on all other accounts. Use an Encrypted Operating System. Get smart about smart device security. Cut back on data sharing. Don't use public computers. Don't use free Wi-Fi. Use a VPN whenever you're online.
What can I do to protect my data?
Apply Software Updates. Protect Passwords. Disable Lock-Screen Notifications. Lock Your Apps. Keep Your Browsing to Yourself. Encrypt Your Data. Back It Up. 10 Outdated Cybersecurity Workplace Practices.
How do I protect my Internet?
Open your router settings page. Create a unique password on your router. Change your Network's SSID name. Enable Network Encryption. Filter MAC addresses. Reduce the Range of the Wireless Signal. Upgrade your Router's firmware.
How do I protect my data on Google?
Know your privacy rights: Use the Google Privacy Center. Protect your content on the services you use. Turn off the suggestion feature in the Chrome browser. Turn off Web History. Opt out of interest-based ad serving. Add SSL to Gmail.
How can you protect yourself from big data?
Create a unique password for every account. You might think that a data breach of an account you rarely use is no big deal. Turn on two-factor authentication. Take action early if there's a data breach.
How can we protect big data?
Think about security before you start your big data project. Consider what data may get stored. Centralize accountability. Encrypt data both at rest and in motion. Separate your keys and your encrypted data. Use the Kerberos network authentication protocol. Use secure automation.
Ready to try pdfFiller's? Secure Hour Article
Upload a document and create your digital autograph now.