Secure Initials Attestation For Free




Join the world’s largest companies









Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution

Unlimited document storage

Widely recognized ease of use

Reusable templates & forms library
The benefits of electronic signatures

Efficiency

Accessibility

Cost savings

Security

Legality

Sustainability
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance

SOC 2 Type II Certified

PCI DSS certification

HIPAA compliance

CCPA compliance
Secure Initials Attestation Feature
The Secure Initials Attestation feature provides a reliable way for you to confirm important documents and agreements securely. This feature enhances your ability to manage signatures while ensuring integrity and trust in your documentation process.
Key Features
Potential Use Cases and Benefits
Using the Secure Initials Attestation feature can solve your problems related to verification and security in document handling. By adopting this feature, you enhance your credibility. You gain peace of mind knowing that your documents are securely attested and easily verifiable. This not only protects you but also reassures your clients and partners about the authenticity of your agreements.
Instructions and Help about Secure Initials Attestation For Free
Secure Initials Attestation: simplify online document editing with pdfFiller
Instead of filing all the documents personally, try modern online solutions for all types of paperwork. Most of them will cover your needs for filling and signing documents, but demand that you use a desktop computer only. When a simple online PDF editing tool is not enough and a more flexible solution is required, you can save your time and work with the documents faster with pdfFiller.
pdfFiller is a web-based document management platform with an array of onboard editing features. Upload and modify documents in PDF, Word, PNG, TXT, and more common formats. Using pdfFiller, make your documents fillable and share them with others right away, edit PDF files, sign contracts and so on.
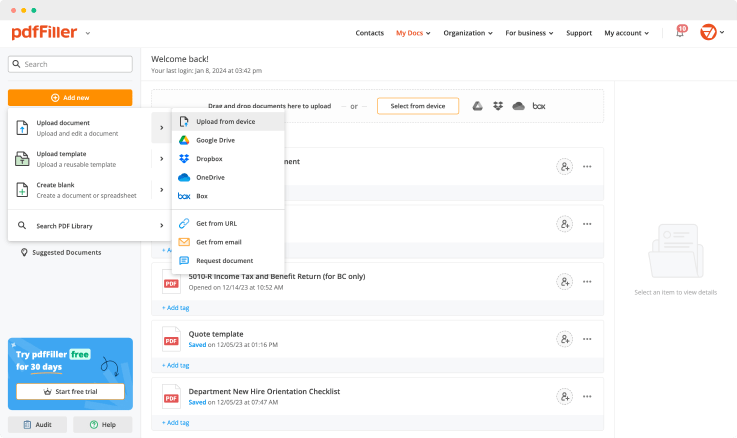
Got the pdfFiller website to work with your documents paperless. Search your device storage for required document to upload and change, or simply create a new one from scratch. All the document processing tools are accessible to you in just one click.
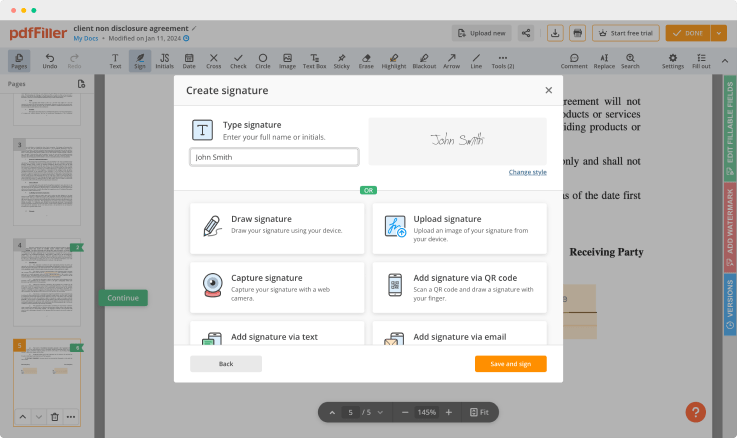
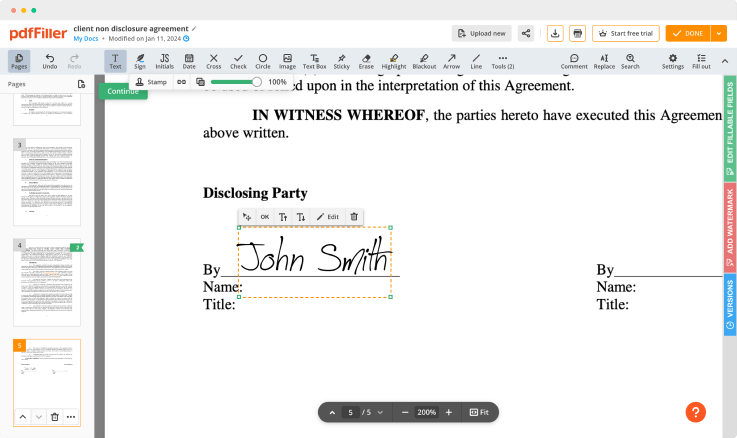
Use editing tools to type in text, annotate and highlight. Change a form’s page order. Once a document is completed, download it to your device or save it to cloud. Collaborate with people to fill out the fields and request an attachment. Add and edit visual content. Add fillable fields and send documents to sign.
To edit PDF form you need to:
pdfFiller makes document management effective and as easy as possible. Go paper-free effortlessly, complete forms and sign important contracts within one browser tab.
For pdfFiller’s FAQs
Ready to try pdfFiller's? Secure Initials Attestation