Secure Needed Field Paper For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
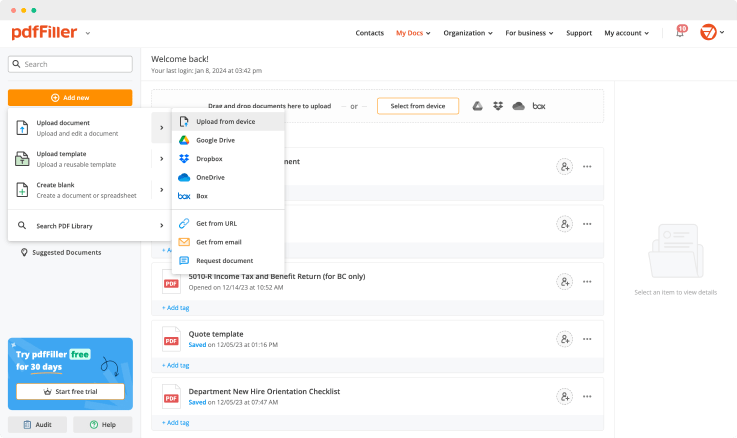
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

Upload a document

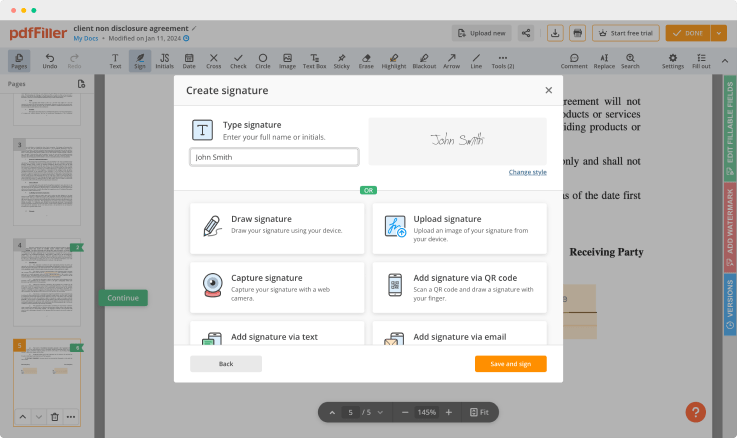
Generate your customized signature

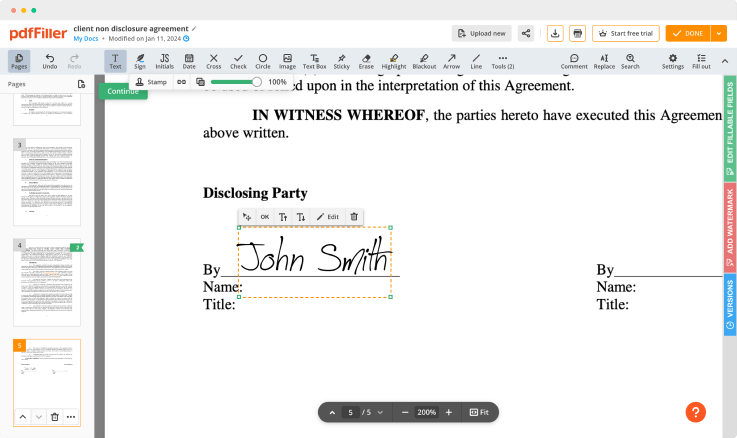
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Secure Needed Field Paper Feature
Introducing the Secure Needed Field Paper feature, designed to simplify how you manage essential documents while ensuring their safety. This feature allows you to create and handle records that require high levels of security and accuracy. Whether you are in a business setting or managing personal information, this tool meets your needs reliably.
Key Features
User-friendly interface that simplifies document creation
Customizable fields for tailored information capture
Automatic backup to prevent data loss
Robust encryption for enhanced security
Easy sharing options with controlled access
Potential Use Cases and Benefits
Ideal for businesses needing secure client information storage
Great for medical professionals managing sensitive patient data
Useful for educators tracking student records securely
Perfect for personal use, such as organizing financial documents safely
With the Secure Needed Field Paper feature, you can protect your important information while ensuring that it is easily accessible when needed. This solution addresses your concerns about data security and organization, giving you peace of mind and increasing your productivity.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How do you secure information systems?
Protect with passwords. Design safe systems. Related: How Small-Business Owners Can Award Against Online Security Threats. Conduct screening and background checks. Provide basic training. Avoid unknown email attachments. Hang up and call back. Think before clicking.
What are the 3 principles of information security?
Three Tenets of Information Security. The CIA triad of confidentiality, integrity, and availability is at the heart of information security. They are fundamental principles of information security.
What are the basic principles of information security?
Information security principles The basic components of information security are most often summed up by the so-called CIA triad: confidentiality, integrity, and availability. Confidentiality is perhaps the element of the triad that most immediately comes to mind when you think of information security.
What are the three elements of information security?
Different Elements in Computer Security In order to fulfil these requirements, we come to the three main elements which are confidentiality, integrity, and availability and the recently added authenticity and utility.
What are the 3 domains of information security?
The Security Domains Triad: Cyber, Physical, People. We recently discussed the tried-and-true CIA information security triad: Confidentiality (keeping secrets secret), Integrity (ensuring information is not modified) and Availability (keeping electronic doors open and IT shops humming).
What are the 5 physical security controls required for information security?
Physical control examples include types of building materials, perimeter security including fencing and locks and guards. Deterrence, denial, detection then delay are the controls used for securing the environment.
What are the physical security controls?
Physical security has three important components: access control, surveillance and testing. Such hardening measures include fencing, locks, access control cards, biometric access control systems and fire suppression systems.
What are the physical security controls used at the airport?
Such hardening measures include fencing, locks, access control cards, biometric access control systems and fire suppression systems. Second, physical locations should be monitored using surveillance cameras and notification systems, such as intrusion detection sensors, heat sensors and smoke detectors.
Ready to try pdfFiller's? Secure Needed Field Paper
Upload a document and create your digital autograph now.