Secure Number Object For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

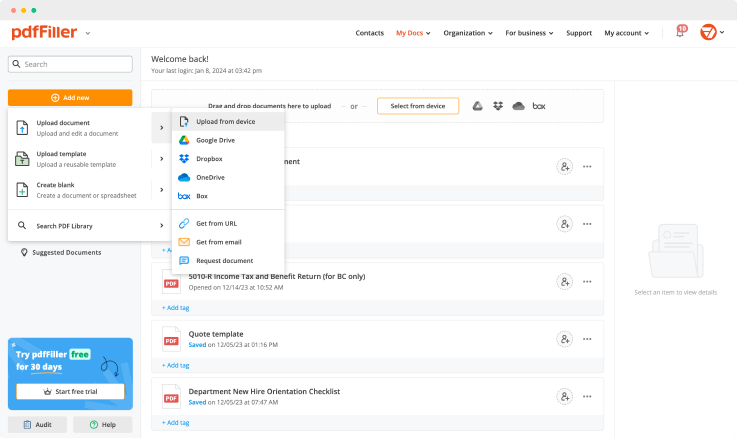
Upload a document

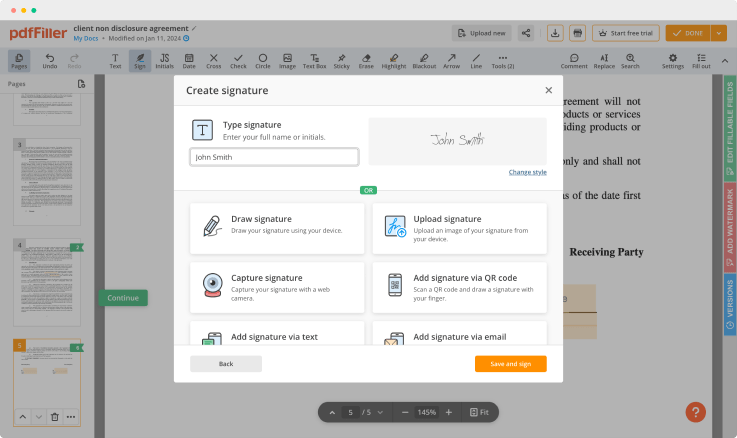
Generate your customized signature

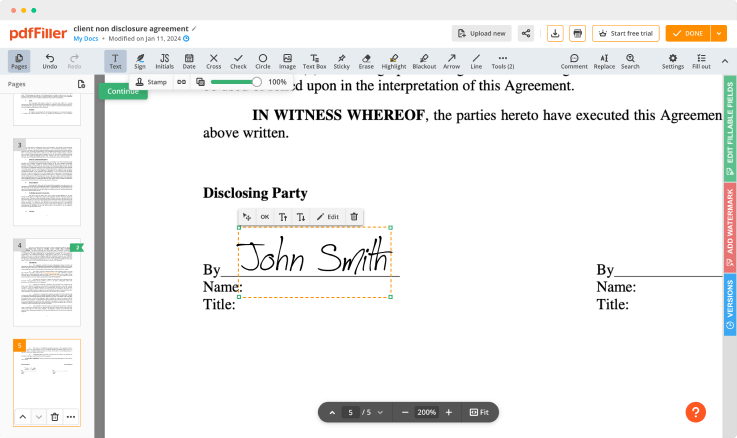
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Secure Number Object Feature
The Secure Number Object feature offers a reliable way to manage sensitive numeric data. It ensures that numbers remain protected while allowing you to perform necessary operations without compromise.
Key Features
Easy integration into existing systems
Robust encryption for secure storage
Flexible data manipulation options
User-friendly interface for quick access
Compatibility with various programming languages
Potential Use Cases and Benefits
Storing credit card numbers securely for online transactions
Managing confidential employee identification numbers
Safeguarding sensitive financial data in applications
Ensuring that personal information remains private in health systems
Facilitating secure data exchanges in collaborative projects
The Secure Number Object feature addresses the need for safety in handling sensitive information. It empowers you to store and process numbers securely, reducing the risk of data breaches. By choosing this feature, you protect your valuable information while maintaining the flexibility to use it effectively.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How do you secure data in a database?
Separate the Database and Web Servers. Keep the database server separate from the web server. Encrypt Stored Files. Encrypt stored files. Encrypt Your Backups Too. Encrypt backup files. Use a WAS. Keep Patches Current. Minimize Use of 3rd Party Apps. Don't Use a Shared Server. Enable Security Controls.
How do you protect data in a database?
Separate the Database and Web Servers. Keep the database server separate from the web server. Encrypt Stored Files. Encrypt stored files. Encrypt Your Backups Too. Encrypt backup files. Use a WAS. Keep Patches Current. Minimize Use of 3rd Party Apps. Don't Use a Shared Server. Enable Security Controls.
What does protecting and maintaining a database mean?
Database security refers to the collective measures used to protect and secure a database or database management software from illegitimate use and malicious threats and attacks. It is a broad term that includes a multitude of processes, tools and methodologies that ensure security within a database environment.
How do you protect data in Access table?
Open the web app in Access and select the table you want to lock from the Table Selector in the left pane. Click Settings/Actions > Lock. The Lock icon appears next to the name of the table. Tip: To unlock a table, follow the same steps and click Unlock.
How do you harden a database?
Locking down access to resources that can be misused. Disabling functions that are not required. Principle of the least authority or least privileges.
How does a DBMS provide data security?
A DBMS provides data security by protecting data against unauthorized uses. Users are assigned to databases. This prevents harmful attacks against the data.
What do you mean by database security?
Database security refers to the collective measures used to protect and secure a database or database management software from illegitimate use and malicious threats and attacks. It is a broad term that includes a multitude of processes, tools and methodologies that ensure security within a database environment.
What is security consideration in DBMS?
Data Security Consideration. It refers to the right of individuals or organizations to deny or restrict the collection and use of information about unauthorized access. Data security requires system managers to reduce unauthorized access to the systems by building physical arrangements and software checks.
Ready to try pdfFiller's? Secure Number Object
Upload a document and create your digital autograph now.