Secure Requisite Field Application For Free
Create a legally-binding electronic signature and add it to contracts, agreements, PDF forms, and other documents – regardless of your location. Collect and track signatures with ease using any device.
Drop document here to upload
Up to 100 MB for PDF and up to 25 MB for DOC, DOCX, RTF, PPT, PPTX, JPEG, PNG, JFIF, XLS, XLSX or TXT
Note: Integration described on this webpage may temporarily not be available.

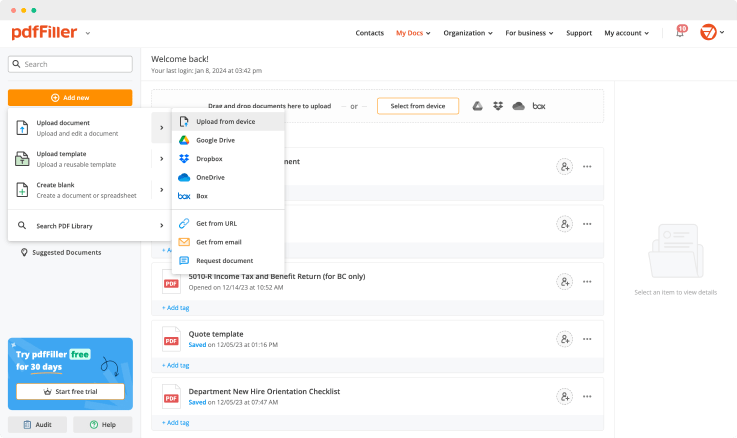
Upload a document

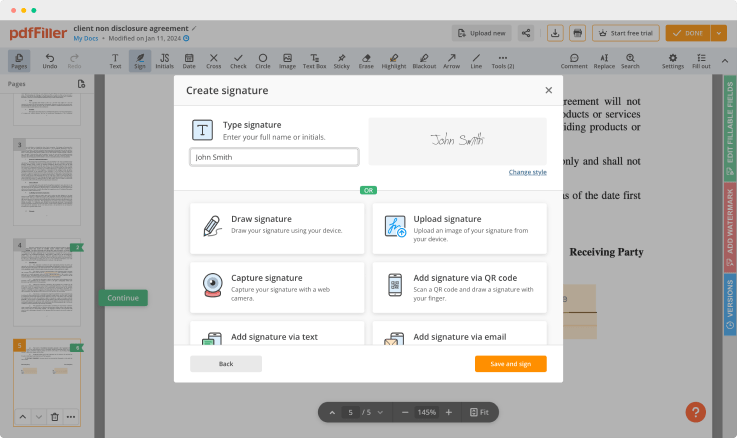
Generate your customized signature

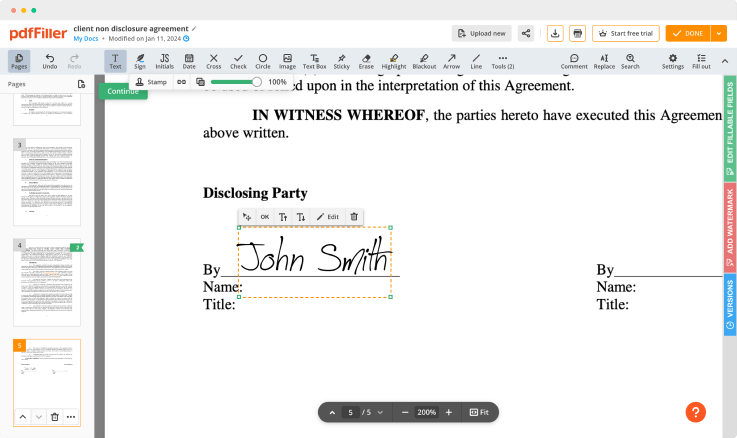
Adjust the size and placement of your signature

Download, share, print, or fax your signed document
Join the world’s largest companies
Employees at these companies use our products.
How to Add a Signature to PDF (and Send it Out for Signature)
Watch the video guide to learn more about pdfFiller's online Signature feature

pdfFiller scores top ratings in multiple categories on G2
4.6/5
— from 710 reviews








Why choose pdfFiller for eSignature and PDF editing?

Cross-platform solution
Upload your document to pdfFiller and open it in the editor.

Unlimited document storage
Generate and save your electronic signature using the method you find most convenient.

Widely recognized ease of use
Resize your signature and adjust its placement on a document.

Reusable templates & forms library
Save a signed, printable document on your device in the format you need or share it via email, a link, or SMS. You can also instantly export the document to the cloud.
The benefits of electronic signatures
Bid farewell to pens, printers, and paper forms.

Efficiency
Enjoy quick document signing and sending and reclaim hours spent on paperwork.

Accessibility
Sign documents from anywhere in the world. Speed up business transactions and close deals even while on the go.

Cost savings
Eliminate the need for paper, printing, scanning, and postage to significantly cut your operational costs.

Security
Protect your transactions with advanced encryption and audit trails. Electronic signatures ensure a higher level of security than traditional signatures.

Legality
Electronic signatures are legally recognized in most countries around the world, providing the same legal standing as a handwritten signature.

Sustainability
By eliminating the need for paper, electronic signatures contribute to environmental sustainability.
Enjoy straightforward eSignature workflows without compromising data security

GDPR compliance
Regulates the use and holding of personal data belonging to EU residents.

SOC 2 Type II Certified
Guarantees the security of your data & the privacy of your clients.

PCI DSS certification
Safeguards credit/debit card data for every monetary transaction a customer makes.

HIPAA compliance
Protects the private health information of your patients.

CCPA compliance
Enhances the protection of personal data and the privacy of California residents.
Secure Requisite Field Application Feature
The Secure Requisite Field Application feature streamlines your data management tasks with safety and efficiency. This tool ensures that your field applications are both protected and compliant, enabling you to focus on what truly matters: your work.
Key Features
Robust data encryption for secure storage
User-friendly interface for easy operation
Real-time data synchronization across devices
Customizable templates to suit your needs
Comprehensive reporting tools for insights
Potential Use Cases and Benefits
Field data collection for construction projects
Health-related data capture in remote areas
Inventory management for retail businesses
Maintenance tracking for transportation fleets
Compliance checks for regulatory purposes
By integrating the Secure Requisite Field Application into your workflow, you solve common problems like data loss, security breaches, and inefficient data entry. This solution gives you peace of mind, allowing you to work confidently and make informed decisions based on accurate data.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What if I have more questions?
Contact Support
How do you secure a Web application?
Step 1: Query parameterization. Step 2: Secure password storage. Step 3: Contextual output encoding XSS defense. Step 4: Content security policy. Step 5: Cross site request forgery.
How do I become an information security analyst?
Information security analysts usually need at least a bachelor's degree in computer science, information assurance, programming, or a related field. Some employers prefer applicants who have a Master of Business Administration (MBA) in information systems.
What education do you need to be an information security analyst?
Information Security Analysts Information security analysts usually need at least a bachelor's degree in computer science, information assurance, programming, or a related field. Some employers prefer applicants who have a Master of Business Administration (MBA) in information systems.
What degree do you need for information security analyst?
Information security analysts usually need at least a bachelor's degree in computer science, information assurance, programming, or a related field. Some employers prefer applicants who have a Master of Business Administration (MBA) in information systems.
How long does it take to become an information security analyst?
How Long Does It Take to Become an Information Security Analyst? It takes approximately four years to earn an information security bachelor's degree and begin looking for a job. Some employers require related work experience or an MBA.
How do I become a cybersecurity analyst without a degree?
1:18 5:59 Suggested clip How To Get A Job In Cybersecurity (No Degree or Experience 2018 YouTubeStart of suggested client of suggested clip How To Get A Job In Cybersecurity (No Degree or Experience 2018
How do I become a security analyst?
Step 1: Earn a Bachelor's Degree. If you are currently enrolled in college and working toward your bachelor's degree, you are already on your way to a financial analyst career. Step 2: Complete an Internship. Step 3: Find a job. Step 4: Get certified and/or an advanced degree.
What does an IT security analyst do?
Information security analysts install software, such as firewalls, to protect computer networks. Information security analysts plan and carry out security measures to protect an organization's computer networks and systems. Their responsibilities are continually expanding as the number of cyberattacks increases.
Ready to try pdfFiller's? Secure Requisite Field Application
Upload a document and create your digital autograph now.