Write Over Mandatory Field Certificate For Free
Discover the simplicity of processing PDFs online








Every PDF tool you need to get documents done paper-free
Create & edit PDFs
Fill out & sign PDF forms
Organize & convert PDFs
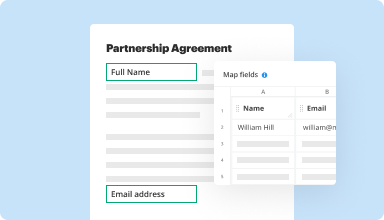
Collect data and approvals
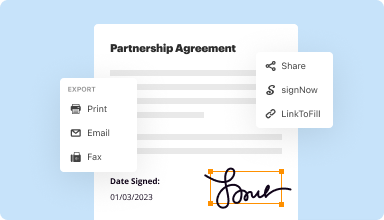
Export documents with ease
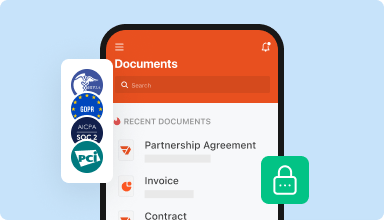
Store documents safely
Customer trust by the numbers
Why choose our PDF solution?
Cloud-native PDF editor
Top-rated for ease of use
Industry-leading customer service
What our customers say about pdfFiller
Write Over Mandatory Field Certificate Feature
The Write Over Mandatory Field Certificate feature transforms how businesses manage essential data fields. It allows you to override mandatory fields to ensure flexibility in your data collection processes. This solution is perfect for organizations looking to adapt quickly to changing needs without compromising data integrity.
Key Features
Potential Use Cases and Benefits
This feature directly addresses common challenges in data collection. It enables you to quickly modify data entry requirements based on real-world conditions. Instead of struggling with rigid forms that impede progress, you can focus on gathering the information you need while ensuring that essential standards are met. As a result, you can expect a smoother workflow, improved compliance, and ultimately, a better output for your business.
For pdfFiller’s FAQs
#1 usability according to G2






