
Get the free Assertions and Protocols for the OASIS - docs oasis-open
Show details
4 Assertions and Protocols for the OASIS Security Assertion Markup Language (SAML) V2.0 5 OASIS Standard, 15 March 2005 6 7 Document identifier: samlcore2.0os 8 9 Location: http://docs.oasisopen.org/security/saml/v2.0/
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign assertions and protocols for
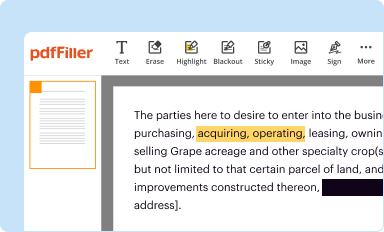
Edit your assertions and protocols for form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
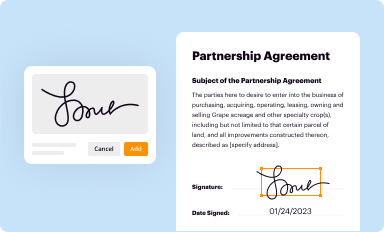
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your assertions and protocols for form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing assertions and protocols for online
In order to make advantage of the professional PDF editor, follow these steps:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit assertions and protocols for. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
With pdfFiller, it's always easy to deal with documents. Try it right now
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out assertions and protocols for
How to fill out assertions and protocols:
01
Start by understanding the purpose of the assertions and protocols. Assertions are statements that define the expected behavior of a system or a specific component. Protocols, on the other hand, outline a set of rules or guidelines that need to be followed for communication between different components or systems.
02
Identify the specific assertions and protocols that need to be filled out. This will depend on the project or system you are working on. It could include assertions related to data validation, error handling, security, performance, or any other aspect that needs to be tested or ensured.
03
Familiarize yourself with the format and structure of assertions and protocols. Typically, assertions are written using a specific syntax or framework, depending on the programming language or testing tool being used. Protocols may be documented using standard formats such as XML or JSON.
04
Consult any existing documentation or guidelines that may already be in place for the project or system. This can provide useful insights and examples to follow when filling out assertions and protocols.
05
Analyze the requirements and specifications of the system or component. This will help determine the necessary assertions to be included. Assertions should cover both positive scenarios where the system is expected to work as intended, as well as negative scenarios where potential errors or failures need to be accounted for.
06
Define the expected behavior and outcomes for each assertion. Clearly state what the system or component is expected to do or not do based on the given input or conditions.
07
Review and validate the assertions to ensure they are accurate, comprehensive, and cover all relevant scenarios. It may be helpful to conduct peer reviews or seek feedback from other team members to ensure the quality and correctness of the assertions.
08
Similarly, for protocols, outline the necessary rules and guidelines that need to be followed for effective communication. Specify the actions, message formats, data flows, and any other relevant details required for successful communication between components or systems.
09
After completing the assertions and protocols, document them in a clear and organized manner. This can include creating separate sections or files for each assertion or protocol, providing appropriate headings, and using consistent formatting throughout the documentation.
Who needs assertions and protocols for?
01
Software developers: Assertions and protocols are essential tools for software developers to ensure the reliability, correctness, and interoperability of their code. By using assertions, developers can verify that their code meets the expected requirements and functions correctly under different scenarios. Protocols help establish communication guidelines between different components or systems, making it easier for developers to integrate and interact with other parts of the software.
02
Quality assurance (QA) teams: QA teams heavily rely on assertions and protocols to test and validate the functionality, performance, and security of software products. By properly filling out assertions, QA teams can create test cases and scenarios that cover a wide range of possible inputs and conditions, ensuring thorough testing. Protocols play a crucial role in testing communication between different components or systems, helping QA teams identify and rectify any issues or inconsistencies.
03
System administrators: System administrators use assertions and protocols to maintain and monitor the performance, security, and compliance of their systems. By properly filling out assertions, administrators can define the expected behavior of their systems and detect any deviations or errors. Protocols aid administrators in configuring and managing the communication between various components or systems, ensuring smooth operation and troubleshooting any communication-related issues.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send assertions and protocols for to be eSigned by others?
When you're ready to share your assertions and protocols for, you can send it to other people and get the eSigned document back just as quickly. Share your PDF by email, fax, text message, or USPS mail. You can also notarize your PDF on the web. You don't have to leave your account to do this.
How do I make edits in assertions and protocols for without leaving Chrome?
assertions and protocols for can be edited, filled out, and signed with the pdfFiller Google Chrome Extension. You can open the editor right from a Google search page with just one click. Fillable documents can be done on any web-connected device without leaving Chrome.
Can I edit assertions and protocols for on an iOS device?
Use the pdfFiller app for iOS to make, edit, and share assertions and protocols for from your phone. Apple's store will have it up and running in no time. It's possible to get a free trial and choose a subscription plan that fits your needs.
What is assertions and protocols for?
Assertions and protocols are used to provide evidence and documentation to support a claim or argument.
Who is required to file assertions and protocols for?
Any individual or organization involved in a legal or regulatory process may be required to file assertions and protocols.
How to fill out assertions and protocols for?
Assertions and protocols are typically filled out by providing detailed information, supporting evidence, and documentation related to the claim or argument.
What is the purpose of assertions and protocols for?
The purpose of assertions and protocols is to provide a clear and organized presentation of evidence and documentation to support a claim or argument.
What information must be reported on assertions and protocols for?
Information reported on assertions and protocols may include facts, data, witness statements, expert opinions, and other supporting evidence.
Fill out your assertions and protocols for online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Assertions And Protocols For is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















