Get the free Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Chil...
Show details
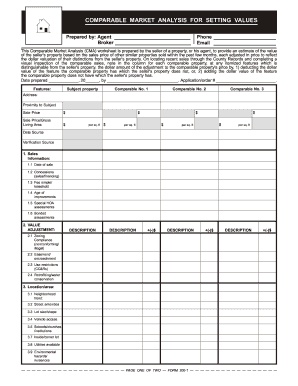
This document outlines the provisions of a federal law intended to develop a national strategy for the prevention of child exploitation, enhance law enforcement capabilities, and address Internet
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign providing resources officers and

Edit your providing resources officers and form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your providing resources officers and form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit providing resources officers and online
To use the services of a skilled PDF editor, follow these steps below:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit providing resources officers and. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
The use of pdfFiller makes dealing with documents straightforward. Try it now!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out providing resources officers and

How to fill out Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008
01
Read the act to understand its purpose and requirements.
02
Identify the specific resources needed for implementation.
03
Gather data on officers' roles in addressing cyber threats.
04
Assess the technology required to support initiatives outlined in the act.
05
Establish a timeline for resource allocation and officer training.
06
Compile a budget that outlines funding necessary for the resources and technology.
07
Coordinate with local law enforcement and educational institutions.
08
Implement monitoring systems to track the effectiveness of the measures.
09
Review and adjust strategies as needed based on feedback and results.
Who needs Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008?
01
Parents and guardians concerned about online safety for their children.
02
Schools and educational institutions that require protocols for cyber safety.
03
Law enforcement agencies tasked with combating cyber threats.
04
Policy makers looking to implement protective measures for children online.
05
Community organizations focused on child welfare and safety.
Fill
form
: Try Risk Free






People Also Ask about
What is the Protect Our children Act of 2008?
Imposes civil penalties on service providers who fail to report suspected child exploitation or . Prohibits law enforcement agencies that receive reports from service providers from disclosing information in such reports except for law enforcement and criminal defense purposes.
What is the Protect Our children Act 2008?
Keeping the Internet Devoid of Sexual Predators Act of 2008 or the KIDS Act of 2008 - Directs the Attorney General to: (1) require sex offenders to provide to the National Sex Offender Registry all Internet identifiers (i.e., email addresses and other designations used for self-identification or routing in Internet
What is the child Act of 2008?
The Child Soldiers Prevention Act (CSPA) is a United States federal statute signed into law by President George W. Bush on December 23, 2008, as part of the William Wilberforce Trafficking Victims Protection Reauthorization Act of 2008. The law criminalizes leading a military force which recruits child soldiers.
What is the Protect Our Kids Act?
Promoting Responsible Oversight To Eliminate Communist Teachings for Our Kids Act or the PROTECT Our Kids Act. This bill prohibits federal education funding for any elementary or secondary school that directly or indirectly receives support from the Chinese government.
What purpose does the child protection act serve?
THEREFORE it is the intent of the Legislature to maintain the long established Constitutional rights of parents to raise, protect, and nurture their children, and to protect children, families, and those who work with them from the harms of wrongful determinations of abuse, by enacting the “Defining Abuse Child
What is the Kids Act of 2008?
The Internet Crimes Against Children Task Force Program (ICAC) helps state and local law enforcement agencies develop an effective response to technology-facilitated child sexual exploitation and Internet crimes against children.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008?
The Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008 is a legislative act aimed at enhancing measures to protect children from cyber threats. It focuses on providing law enforcement with the necessary resources, personnel, and technology to combat online dangers that may target minors.
Who is required to file Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008?
Entities such as law enforcement agencies, local governments, and educational institutions that receive funding under this act are typically required to file and comply with its provisions.
How to fill out Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008?
To fill out the provisions related to the act, entities must gather required data on resource allocation, detailing the usage of funds, staffing levels, and technology deployment efforts aimed at preventing cyber threats to children. An official form or application process may be provided by the relevant authority.
What is the purpose of Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008?
The purpose of the act is to strengthen the framework for protecting children from cyber threats by ensuring that law enforcement and community organizations have the necessary tools, personnel, and support to effectively address online dangers that target minors.
What information must be reported on Providing Resources, Officers, and Technology To Eradicate Cyber Threats to Our Children Act of 2008?
The information required to be reported typically includes details on the financial expenditures related to the act, the number of officers deployed for child protection efforts, statistics on cyber incidents involving children, and the effectiveness of the technologies employed.
Fill out your providing resources officers and online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Providing Resources Officers And is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.