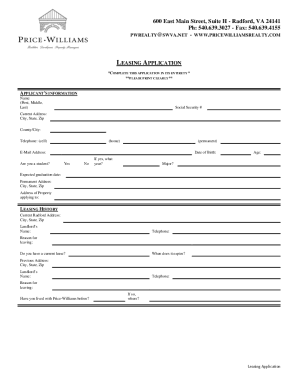
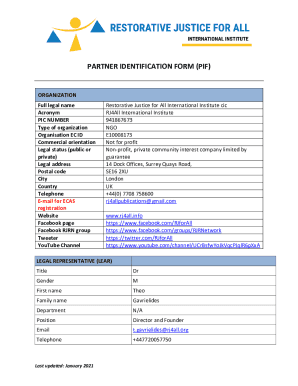
Get the free Risk Management Bulletin - Volume 8, Issue 6 - nd
Show details
This bulletin provides updates and information on risk management initiatives, training programs, and recommendations for state entities in North Dakota.
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign risk management bulletin

Edit your risk management bulletin form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your risk management bulletin form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing risk management bulletin online
To use our professional PDF editor, follow these steps:
1
Check your account. In case you're new, it's time to start your free trial.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit risk management bulletin. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Save your file. Select it in the list of your records. Then, move the cursor to the right toolbar and choose one of the available exporting methods: save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud.
With pdfFiller, it's always easy to work with documents. Try it!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out risk management bulletin

How to fill out Risk Management Bulletin - Volume 8, Issue 6
01
Begin by gathering the necessary background information related to the risks being addressed.
02
Access Volume 8, Issue 6 of the Risk Management Bulletin from the designated website or database.
03
Review the guidelines provided at the beginning of the bulletin for understanding its structure.
04
Identify the key sections of the bulletin that need to be filled out, such as introduction, risk assessments, and mitigation strategies.
05
Prepare concise and accurate descriptions for each identified risk, following the prescribed format.
06
Include relevant data and statistics to support your assessments and recommendations.
07
Ensure that all entries are clear and concise, avoiding unnecessary jargon or technical language.
08
Review and revise the filled-out sections for clarity and coherence, checking for any missing information.
09
Submit the completed Risk Management Bulletin as instructed, ensuring a copy is saved for your records.
Who needs Risk Management Bulletin - Volume 8, Issue 6?
01
Risk managers looking to identify, assess, and mitigate risks within their organizations.
02
Compliance officers needing to ensure adherence to industry regulations and standards.
03
Executives and decision-makers who require insights on risk management to inform strategic planning.
04
Stakeholders and investors interested in understanding the risk landscape of the organization.
05
Employees involved in operational roles who are tasked with implementing risk management practices.
Fill
form
: Try Risk Free






People Also Ask about
What are the main types of risk management?
It involves the process of identifying, assessing, and prioritizing risks, as well as developing and implementing strategies to mitigate or minimize those risks. There are three main types of risk management: financial risk management, operational risk management, and strategic risk management.
What are the 5 W's in risk management?
Understanding the “five W's” is crucial in risk management. The five W's in risk management are: Who, What, Where, When, and Why. These questions help in identifying potential risks and preparing a plan to mitigate them.
What are the 5 Rs of risk management?
The 5 Rs of risk management—Recognise, Rank, Respond, Report, Review—form a comprehensive strategy to handle risks effectively. Understanding and implementing these principles can save your organisation from potential setbacks and improve overall operational efficiency.
What are the 5 R's of risk management?
The 5 Rs of risk management—readiness, response, reduction, recovery, and review—are essential for effective risk mitigation.
What are the 8 recommended types of risk management?
8 Types of risk and risk management investment Technical Risk. For example are not confident that a particular requirement is achievable given the constraint of existing technology. Supply Chain. Manufacturability risks. Unit cost. Product fit/Market. Resource Risks. Program-management. Interpersonal.
What are the 8 principles under ISO 31000 risk management?
The International Organization for Standardization (ISO) outlines eight risk management principles to create a robust risk management program: Integration. Structured and comprehensive. Customized. Inclusive. Dynamic. Uses best available information. Considers human and culture factors. Practices continual improvement.
What is risk management level 6?
The SRMC® Level 6 course provides in-depth knowledge on critical security risk management topics, equipping professionals with the skills necessary to deliver strategic leadership and establish credibility in the field of security risk management.
What are the 8 key risk types?
These risks are: Credit, Interest Rate, Liquidity, Price, Foreign Exchange, Transaction, Compliance, Strategic and Reputation.
What are the 5 principles of risk management?
The 5 basic principles of risk management are to: Avoid risk - Identify appropriate strategies that can be used to avoid the risk whenever possible, if a risk cannot be eliminated then it must be managed Identify risk - Assess the risk, identify the nature of the risk and who is involved Analyse risk - By examining how
What are the 8 steps to the risk management process?
Eight steps to establishing a risk management program are: Implement a Risk Management Framework based on the Risk Policy. Establish the Context. Identify Risks. Analyze and Evaluate Risks. Treat and Manage Risks. Communicate and Consult. Monitor and Review. Record.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is Risk Management Bulletin - Volume 8, Issue 6?
Risk Management Bulletin - Volume 8, Issue 6 is a publication that provides updates and guidance on risk management practices, trends, and regulations relevant to various industries.
Who is required to file Risk Management Bulletin - Volume 8, Issue 6?
Entities involved in activities that expose them to significant risks, such as financial institutions, insurance companies, and corporations dealing with hazardous materials, are typically required to file this bulletin.
How to fill out Risk Management Bulletin - Volume 8, Issue 6?
To fill out the Risk Management Bulletin, individuals must follow the provided guidelines, accurately complete the required sections regarding risk assessments, management strategies, and submit relevant documentation.
What is the purpose of Risk Management Bulletin - Volume 8, Issue 6?
The purpose of the bulletin is to enhance awareness and compliance regarding risk management practices, thereby minimizing potential risks and promoting safety within organizations.
What information must be reported on Risk Management Bulletin - Volume 8, Issue 6?
The bulletin generally requires information related to risk assessments, mitigation strategies, incident reporting, and compliance with regulatory requirements.
Fill out your risk management bulletin online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Risk Management Bulletin is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.