
Get the free Security Breach Response Policy ( pdf )
Show details
Oregon Public Employees Retirement System Posted date November 24, 2009, Number 1.10.01.01.001.PRO Page 1 of 5 Signature Approval date November 13, 2009, Paul Clara Policy/Procedure: Security Breach
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign security breach response policy
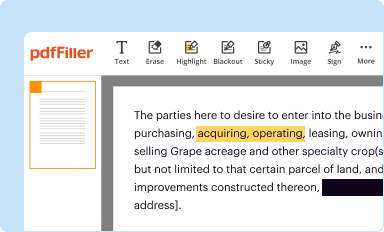
Edit your security breach response policy form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
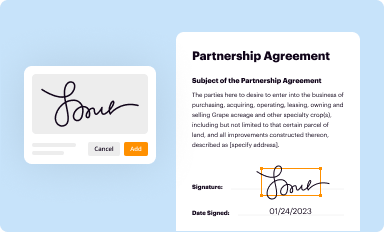
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your security breach response policy form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing security breach response policy online
To use our professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit security breach response policy. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
Dealing with documents is always simple with pdfFiller.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out security breach response policy
01
Start by conducting a thorough risk assessment to identify potential security breaches and their potential impact on your organization.
02
Define the scope and objectives of your security breach response policy to ensure it aligns with your organization's goals and regulatory requirements.
03
Identify a designated response team responsible for managing and executing the policy in the event of a security breach. This team should include members from IT, legal, human resources, and public relations.
04
Clearly outline the reporting and escalation procedures within your policy. Specify who should be notified in the event of a breach and establish clear channels of communication.
05
Develop a step-by-step incident response plan that outlines the actions to be taken when a breach occurs. This plan should include measures such as containing the breach, investigating the incident, notifying affected individuals, and restoring systems and data.
06
Ensure your policy addresses compliance with relevant laws and regulations, such as data breach notification requirements and data protection regulations.
07
Regularly review and update your security breach response policy to reflect emerging threats and changing regulatory requirements.
08
Train your employees on the policy, ensuring they are aware of their roles and responsibilities in responding to a security breach.
09
Conduct regular drills and simulations to test the effectiveness of your policy and enhance your organization's incident response capabilities.
Who needs security breach response policy?
01
Organizations of all sizes and industries should have a security breach response policy in place.
02
Companies that handle sensitive customer data, such as personal information, financial records, or medical records, are particularly susceptible to breaches and should prioritize having a comprehensive policy.
03
Compliance with data protection laws and regulations often requires organizations to have a formal security breach response policy.
04
Proactive implementation of a security breach response policy can help minimize the potential damage and financial losses associated with a breach, making it beneficial for any organization.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I get security breach response policy?
It's simple with pdfFiller, a full online document management tool. Access our huge online form collection (over 25M fillable forms are accessible) and find the security breach response policy in seconds. Open it immediately and begin modifying it with powerful editing options.
Can I create an electronic signature for signing my security breach response policy in Gmail?
Use pdfFiller's Gmail add-on to upload, type, or draw a signature. Your security breach response policy and other papers may be signed using pdfFiller. Register for a free account to preserve signed papers and signatures.
How do I fill out security breach response policy on an Android device?
Complete security breach response policy and other documents on your Android device with the pdfFiller app. The software allows you to modify information, eSign, annotate, and share files. You may view your papers from anywhere with an internet connection.
What is security breach response policy?
A security breach response policy is a set of guidelines and procedures that an organization follows in the event of a data breach or security incident.
Who is required to file security breach response policy?
The organization or entity that experiences a security breach is required to file a security breach response policy.
How to fill out security breach response policy?
To fill out a security breach response policy, the organization should include information about the steps to be taken in case of a breach, the team responsible for managing the response, and any notification or reporting requirements.
What is the purpose of security breach response policy?
The purpose of a security breach response policy is to ensure that an organization responds swiftly, effectively, and in accordance with applicable laws and regulations in the event of a data breach or security incident.
What information must be reported on security breach response policy?
The information that must be reported on a security breach response policy can vary depending on local laws and regulations, but typically includes details about the incident, the affected individuals, and any actions taken by the organization.
Fill out your security breach response policy online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Security Breach Response Policy is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















