Get the free A CHECKLIST FOR PROTECTING YOUR HOME WHEN YOURE AWAY
Show details
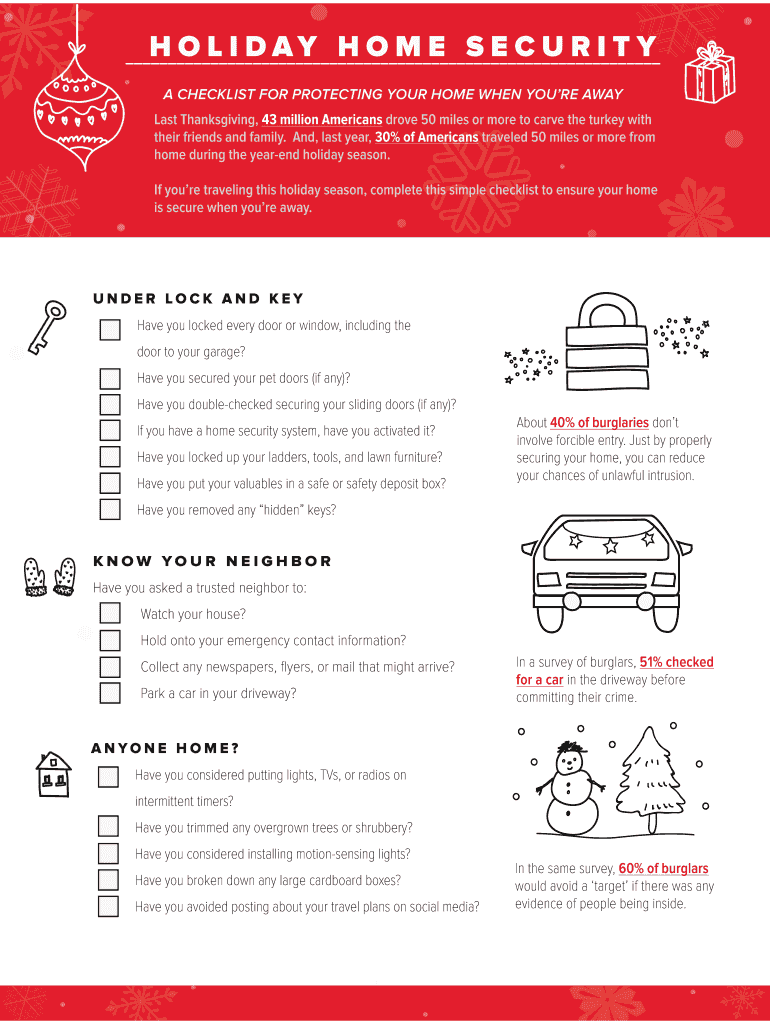
H O L I DAY H O M E S E C U R I T Y A CHECKLIST FOR PROTECTING YOUR HOME WHEN YOU'RE AWAY Last Thanksgiving, 43 million Americans drove 50 miles or more to carve the turkey with their friends and
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign a checklist for protecting

Edit your a checklist for protecting form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your a checklist for protecting form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit a checklist for protecting online
Use the instructions below to start using our professional PDF editor:
1
Log into your account. It's time to start your free trial.
2
Prepare a file. Use the Add New button. Then upload your file to the system from your device, importing it from internal mail, the cloud, or by adding its URL.
3
Edit a checklist for protecting. Add and replace text, insert new objects, rearrange pages, add watermarks and page numbers, and more. Click Done when you are finished editing and go to the Documents tab to merge, split, lock or unlock the file.
4
Save your file. Choose it from the list of records. Then, shift the pointer to the right toolbar and select one of the several exporting methods: save it in multiple formats, download it as a PDF, email it, or save it to the cloud.
It's easier to work with documents with pdfFiller than you could have ever thought. You can sign up for an account to see for yourself.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out a checklist for protecting

How to Fill Out a Checklist for Protecting:
01
Start by identifying the assets or areas you wish to protect. This could include physical assets like buildings or equipment, or digital assets such as data and information.
02
Assess the potential risks and vulnerabilities that these assets may face. This could involve evaluating threats like theft, damage, or cybersecurity breaches.
03
Determine the necessary protective measures for each asset. This may involve implementing security systems, establishing emergency response plans, or implementing cybersecurity protocols.
04
Prioritize your protective measures based on the severity of the risks and the value of the assets. Allocate resources and attention accordingly to ensure the most effective protection.
05
Set up a regular maintenance and review schedule for your checklist. As circumstances change, it is important to update and adapt your protective measures accordingly.
Who Needs a Checklist for Protecting?
01
Businesses: Companies of all sizes can benefit from having a checklist for protecting their assets. This includes physical security measures for their premises, protection against cyber threats, and safeguarding their intellectual property.
02
Homeowners: Homeowners can use a checklist to protect their property from theft, fire, or other potential hazards. This may involve securing windows and doors, installing smoke detectors and fire extinguishers, and implementing home security systems.
03
IT Professionals: IT professionals are responsible for safeguarding digital assets and preventing cybersecurity incidents. They can use a checklist to ensure that appropriate security measures are in place, such as regular software updates, strong passwords, and robust firewalls.
Overall, anyone who has valuable assets or information that they wish to protect can benefit from using a checklist. It serves as a tool to systematically evaluate risks, establish protective measures, and ensure ongoing security.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send a checklist for protecting for eSignature?
Once your a checklist for protecting is ready, you can securely share it with recipients and collect eSignatures in a few clicks with pdfFiller. You can send a PDF by email, text message, fax, USPS mail, or notarize it online - right from your account. Create an account now and try it yourself.
How do I edit a checklist for protecting in Chrome?
Adding the pdfFiller Google Chrome Extension to your web browser will allow you to start editing a checklist for protecting and other documents right away when you search for them on a Google page. People who use Chrome can use the service to make changes to their files while they are on the Chrome browser. pdfFiller lets you make fillable documents and make changes to existing PDFs from any internet-connected device.
Can I create an electronic signature for the a checklist for protecting in Chrome?
You certainly can. You get not just a feature-rich PDF editor and fillable form builder with pdfFiller, but also a robust e-signature solution that you can add right to your Chrome browser. You may use our addon to produce a legally enforceable eSignature by typing, sketching, or photographing your signature with your webcam. Choose your preferred method and eSign your a checklist for protecting in minutes.
What is a checklist for protecting?
A checklist for protecting is a list of security measures and protocols to ensure the safety and security of a specific entity or system.
Who is required to file a checklist for protecting?
Anyone responsible for the security of a particular entity or system may be required to file a checklist for protecting.
How to fill out a checklist for protecting?
To fill out a checklist for protecting, one must carefully review the security requirements and guidelines, and then document the implementation of relevant security measures.
What is the purpose of a checklist for protecting?
The purpose of a checklist for protecting is to provide a structured approach to assessing and enhancing the security posture of a specific entity or system.
What information must be reported on a checklist for protecting?
Information such as security measures implemented, security vulnerabilities identified, and any security incidents or breaches must be reported on a checklist for protecting.
Fill out your a checklist for protecting online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

A Checklist For Protecting is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















