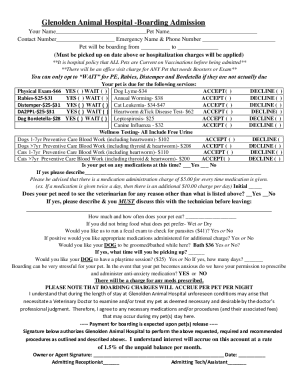
Get the free Breach Reporting and Safeguarding PHI - hipaa uams
Show details
This document outlines the policies and procedures for reporting breaches of Protected Health Information (PHI) at UAMS, including definitions of breaches, notification requirements, and safeguarding
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign breach reporting and safeguarding

Edit your breach reporting and safeguarding form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your breach reporting and safeguarding form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing breach reporting and safeguarding online
Use the instructions below to start using our professional PDF editor:
1
Check your account. If you don't have a profile yet, click Start Free Trial and sign up for one.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit breach reporting and safeguarding. Replace text, adding objects, rearranging pages, and more. Then select the Documents tab to combine, divide, lock or unlock the file.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
It's easier to work with documents with pdfFiller than you could have believed. Sign up for a free account to view.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out breach reporting and safeguarding

How to fill out Breach Reporting and Safeguarding PHI
01
Identify the breach: Determine what happened, including the type and extent of PHI involved.
02
Document the breach: Record all relevant details such as date, time, and how the breach occurred.
03
Notify affected individuals: Inform those whose PHI was compromised about the breach, outlining potential risks and remedies.
04
Report to authorities: Depending on the nature of the breach, report it to the appropriate regulatory bodies as required by law.
05
Assess risk: Conduct a risk assessment to evaluate potential harm to individuals based on the breach.
06
Implement corrective actions: Develop and apply measures to prevent future breaches, including staff training and policy updates.
07
Review and evaluate: Analyze the breach and response after resolution to identify improvements.
Who needs Breach Reporting and Safeguarding PHI?
01
Healthcare providers: Hospitals, clinics, and individual practitioners handling PHI.
02
Health plans: Insurance companies that manage patient data.
03
Business associates: Entities that perform services on behalf of healthcare providers that involve PHI.
04
Compliance officers: Professionals responsible for ensuring adherence to regulations and reporting requirements.
05
Legal advisors: Lawyers who provide guidance on breach notification laws and regulations.
Fill
form
: Try Risk Free






People Also Ask about
What is a breach in PHI?
HIPAA's Breach Notification Rule requires covered entities to notify patients when their unsecured protected heath information (PHI) is impermissibly used or disclosed — or “breached,” — in a way that compromises the privacy and security of the PHI.
What should I do if I suspect a breach involving PHI?
You can submit a complaint online through the OCR's website or by mail, fax, or email. It is essential to file the complaint within 180 days of when you first became aware of the potential violation, although the OCR may grant an extension under certain circumstances.
What steps should be taken if there is a breach of PHI?
Once a covered entity knows or by reasonable diligence should have known (referred to as the “date of discovery”) that a breach of PHI has occurred, the entity has an obligation to notify the relevant parties (individuals, HHS and/or the media) “without unreasonable delay” or up to 60 calendar days following the date
What is the standard for safeguarding PHI?
The HIPAA Security Rule requires physicians to protect patients' electronically stored, protected health information (known as “ePHI”) by using appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity and security of this information.
How do you report a breach of confidentiality?
You must report a notifiable breach to the ICO without undue delay, but not later than 72 hours after becoming aware of it. If you take longer than this, you must give reasons for the delay.
Should a PHI breach be reported?
Breach Notification Requirements Following a breach of Unsecured PHI, Covered Entities must provide notification of the breach to affected individuals, the Secretary of Health and Human Services, and – in some circumstances – to the media.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is Breach Reporting and Safeguarding PHI?
Breach Reporting and Safeguarding PHI refers to the process of notifying relevant authorities and affected individuals when there has been a violation or unauthorized access to Protected Health Information (PHI). It aims to protect the integrity and confidentiality of sensitive health data.
Who is required to file Breach Reporting and Safeguarding PHI?
Covered entities such as healthcare providers, health plans, and healthcare clearinghouses are required to file Breach Reporting and Safeguarding PHI. Business associates that have access to PHI also have obligations in this regard.
How to fill out Breach Reporting and Safeguarding PHI?
To fill out Breach Reporting and Safeguarding PHI, one must collect pertinent details about the breach, including the nature of the violation, the types of PHI affected, the number of individuals impacted, and any steps taken to mitigate harm. This information should be compiled and submitted to the relevant authorities as specified by regulations.
What is the purpose of Breach Reporting and Safeguarding PHI?
The purpose is to ensure transparency, protect individuals' privacy rights, and promote accountability among entities handling PHI. It also helps to prevent further breaches and facilitate safety measures.
What information must be reported on Breach Reporting and Safeguarding PHI?
Information that must be reported includes the nature of the breach, the date it occurred, the date it was discovered, a description of the PHI involved, the number of individuals affected, and actions taken to address the breach and prevent future incidents.
Fill out your breach reporting and safeguarding online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Breach Reporting And Safeguarding is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.