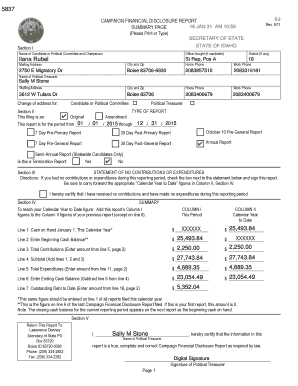
Get the free Web Timing Attacks Made Practical - Black Hat
Show details
Web Timing Attacks Made Practical Timothy D. Morgan Jason W. Morgan August 3, 2015, Abstract This paper addresses the problem of exploiting timing side channels in web applications. To date, differences
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign web timing attacks made

Edit your web timing attacks made form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your web timing attacks made form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing web timing attacks made online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Log into your account. If you don't have a profile yet, click Start Free Trial and sign up for one.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit web timing attacks made. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
pdfFiller makes dealing with documents a breeze. Create an account to find out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out web timing attacks made

How to fill out web timing attacks made:
01
First, it is important to understand what web timing attacks are. A web timing attack is a type of cyber attack that utilizes timing measurements to infer sensitive information about a target system. These attacks exploit timing differences in the response of a target system to gain unauthorized access or extract confidential data.
02
To fill out web timing attacks, you need to have a deep understanding of web application vulnerabilities and the techniques used to exploit them. This includes knowledge of web technologies, network protocols, and programming languages commonly used in web development.
03
Familiarize yourself with the various types of web timing attacks. Some common examples include cross-site scripting (XSS) attacks, SQL injection attacks, and vulnerability scanning attacks. Each of these attacks leverages timing measurements to gather information or exploit vulnerabilities in a web application.
04
Acquire the necessary tools and software to execute web timing attacks. There are numerous open-source and commercial tools available that can assist in identifying and exploiting timing vulnerabilities in web applications. Some popular tools include Burp Suite, OWASP ZAP, and Nessus.
05
Perform a thorough reconnaissance of the target web application. This involves identifying potential entry points, analyzing the structure and functionality of the application, and understanding the user authentication and session management mechanisms.
06
Once you have identified potential vulnerabilities, it is important to test their feasibility through controlled experiments. Timing measurements can be used to determine if an attack is successful or not. Keep in mind that these experiments should only be performed on systems that you have explicit permission to test, as web timing attacks can be highly invasive and may cause harm if not conducted ethically.
Who needs web timing attacks made?
01
Web developers and security professionals can use web timing attacks to assess the security posture of their own applications. By identifying and exploiting vulnerabilities using timing measurements, they can better understand the potential risks and develop appropriate countermeasures.
02
Penetration testers and ethical hackers often utilize web timing attacks as part of their comprehensive security assessments. These experts can simulate real-world attack scenarios to identify weaknesses and help organizations improve their security defenses.
03
Researchers and academics studying web application security may also employ web timing attacks to gain insights into the effectiveness of existing security techniques or to develop new methodologies for defending against such attacks.
In conclusion, filling out web timing attacks requires a combination of technical knowledge, appropriate tools, and ethical consideration. It is essential to have a clear understanding of the attack techniques and their potential impacts. Only through responsible and authorized use can web timing attacks be leveraged effectively to enhance web application security.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I modify my web timing attacks made in Gmail?
Using pdfFiller's Gmail add-on, you can edit, fill out, and sign your web timing attacks made and other papers directly in your email. You may get it through Google Workspace Marketplace. Make better use of your time by handling your papers and eSignatures.
How do I make changes in web timing attacks made?
pdfFiller not only allows you to edit the content of your files but fully rearrange them by changing the number and sequence of pages. Upload your web timing attacks made to the editor and make any required adjustments in a couple of clicks. The editor enables you to blackout, type, and erase text in PDFs, add images, sticky notes and text boxes, and much more.
Can I create an electronic signature for the web timing attacks made in Chrome?
Yes. With pdfFiller for Chrome, you can eSign documents and utilize the PDF editor all in one spot. Create a legally enforceable eSignature by sketching, typing, or uploading a handwritten signature image. You may eSign your web timing attacks made in seconds.
What is web timing attacks made?
Web timing attacks are made by exploiting timing differences in a web application to gather information on the system.
Who is required to file web timing attacks made?
Anyone who discovers or suspects web timing attacks should report them to the appropriate authorities.
How to fill out web timing attacks made?
To report web timing attacks, detailed information on the attack method, target system, and any potential impact must be provided.
What is the purpose of web timing attacks made?
The purpose of web timing attacks is usually to gather sensitive information or to disrupt the normal operation of a web application.
What information must be reported on web timing attacks made?
Information such as the target system, date and time of the attack, and any data gathered during the attack must be reported.
Fill out your web timing attacks made online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Web Timing Attacks Made is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.