Get the free REQUIREMENTS IN SECURING - Alaminos Pangasinan - alaminoscity gov
Show details
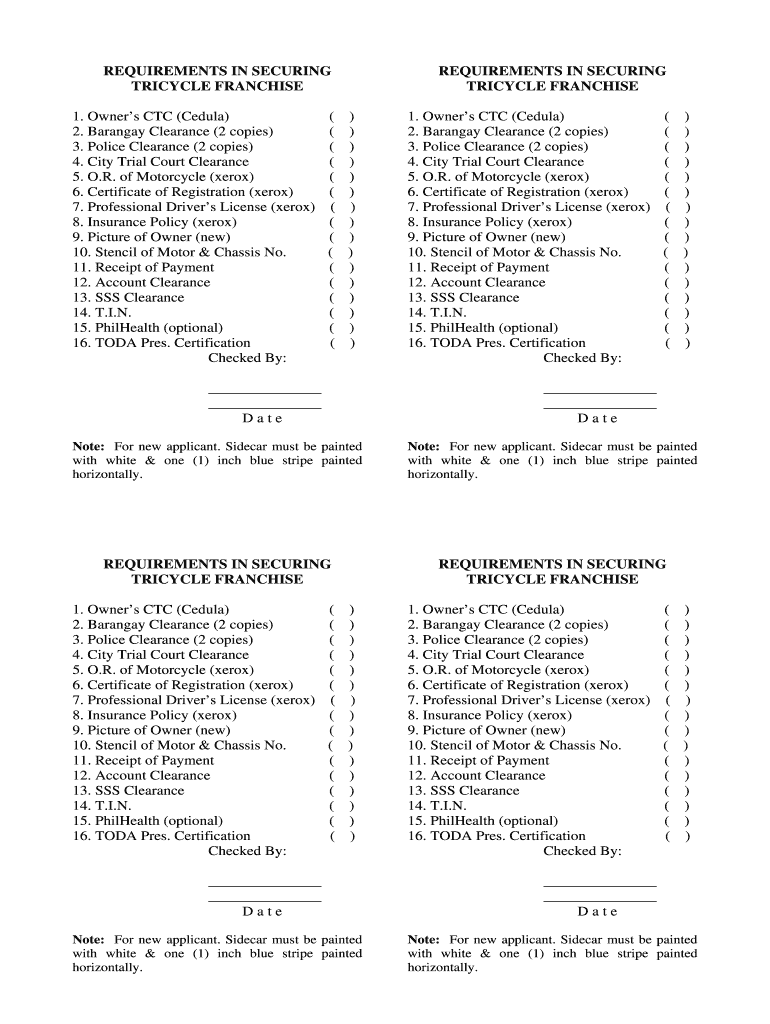
REQUIREMENTS IN SECURING TRICYCLE FRANCHISE 1. Owners CTC (Medulla) 2. Barangay Clearance (2 copies) 3. Police Clearance (2 copies) 4. City Trial Court Clearance 5. O.R. of Motorcycle (xerox) 6. Certificate
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign requirements in securing

Edit your requirements in securing form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your requirements in securing form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing requirements in securing online
Use the instructions below to start using our professional PDF editor:
1
Log in to your account. Start Free Trial and register a profile if you don't have one.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit requirements in securing. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
pdfFiller makes working with documents easier than you could ever imagine. Try it for yourself by creating an account!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out requirements in securing

How to fill out requirements in securing:
01
Identify the objectives: Start by clearly defining the objectives of the securing process. Determine what needs to be protected, the potential threats, and the desired level of security. This will help in establishing the requirements.
02
Involve stakeholders: Engage all relevant stakeholders in the process. This includes representatives from different departments, IT teams, management, and security experts. Their input and expertise will help ensure that all requirements are comprehensive and consider different perspectives.
03
Conduct a risk assessment: Assess the potential risks and vulnerabilities that could impact the security of the system or organization. This analysis will help in determining the necessary requirements to mitigate or address these risks effectively.
04
Define functional and non-functional requirements: Clearly identify the functional and non-functional requirements for securing the system or organization. Functional requirements include specific features or capabilities needed, while non-functional requirements focus on performance, reliability, and security standards.
05
Prioritize and categorize requirements: Prioritize the identified requirements based on their criticality and impact on securing. Categorize them into different groups, such as high-priority, medium-priority, and low-priority, to effectively allocate resources and ensure the most critical needs are addressed first.
06
Document requirements: Document all the identified requirements in a clear and concise manner. Use a standardized template or format that enables easy understanding and communication of the requirements to everyone involved.
07
Validate and refine requirements: Review the documented requirements with all stakeholders, and gather feedback and suggestions for improvement. Refine the requirements based on this feedback and ensure they align with the overall objectives and risk assessment.
08
Communicate requirements: Communicate the finalized requirements to all relevant parties, including developers, designers, and vendors involved in the securing process. Clear communication of requirements is essential to ensure everyone understands their roles and responsibilities in implementing the necessary security measures.
Who needs requirements in securing?
01
Organizations: Organizations of all sizes and types need requirements in securing to protect their assets, data, and operations from potential threats. Securing requirements help establish guidelines and standards for safeguarding critical information and infrastructure.
02
IT teams: IT teams play a crucial role in implementing and maintaining security measures. They need requirements in securing to guide their efforts in areas such as network security, access control, encryption, and vulnerability management.
03
Management: Management needs requirements in securing to make informed decisions regarding resource allocation, budgeting, and overall strategic planning. Understanding the security requirements helps management prioritize security initiatives and ensure compliance with relevant regulations or standards.
04
System users: Users of secured systems or networks also benefit from clear security requirements. By understanding the requirements, users can adhere to necessary protocols and practices to minimize risk and contribute to the overall security of the organization.
In summary, filling out requirements in securing involves identifying objectives, involving stakeholders, conducting risk assessments, defining functional and non-functional requirements, prioritizing and categorizing requirements, documenting and refining them, and communicating to relevant parties. Organizations, IT teams, management, and system users all need requirements in securing to ensure effective security measures are in place.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is requirements in securing?
Requirements in securing refers to the necessary qualifications, documents, or procedures that need to be fulfilled in order to secure something, such as a loan or a permit.
Who is required to file requirements in securing?
The individual or entity seeking to secure something is required to file requirements in securing.
How to fill out requirements in securing?
Requirements in securing can be filled out by providing the necessary information, documents, and signatures as requested by the governing authority.
What is the purpose of requirements in securing?
The purpose of requirements in securing is to ensure that all necessary criteria are met before securing something, in order to minimize risks and ensure compliance with regulations.
What information must be reported on requirements in securing?
The information that must be reported on requirements in securing may vary depending on the specific context, but typically includes personal or business details, financial information, and supporting documents.
How do I complete requirements in securing online?
pdfFiller makes it easy to finish and sign requirements in securing online. It lets you make changes to original PDF content, highlight, black out, erase, and write text anywhere on a page, legally eSign your form, and more, all from one place. Create a free account and use the web to keep track of professional documents.
Can I create an electronic signature for the requirements in securing in Chrome?
You certainly can. You get not just a feature-rich PDF editor and fillable form builder with pdfFiller, but also a robust e-signature solution that you can add right to your Chrome browser. You may use our addon to produce a legally enforceable eSignature by typing, sketching, or photographing your signature with your webcam. Choose your preferred method and eSign your requirements in securing in minutes.
How do I complete requirements in securing on an iOS device?
Install the pdfFiller app on your iOS device to fill out papers. If you have a subscription to the service, create an account or log in to an existing one. After completing the registration process, upload your requirements in securing. You may now use pdfFiller's advanced features, such as adding fillable fields and eSigning documents, and accessing them from any device, wherever you are.
Fill out your requirements in securing online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Requirements In Securing is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















