Get the free Non-Employee Computer System Access Request Form
Show details
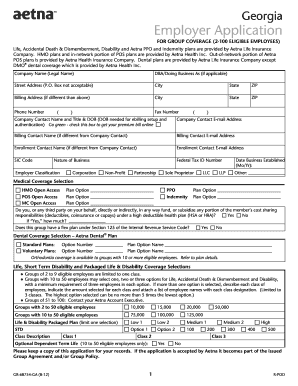
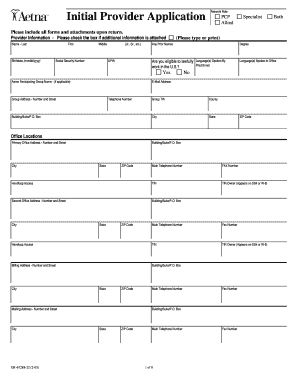
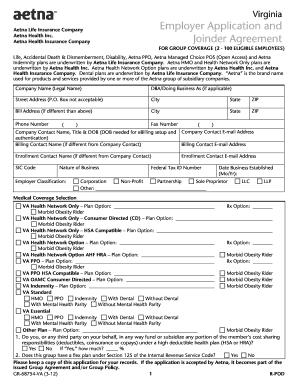
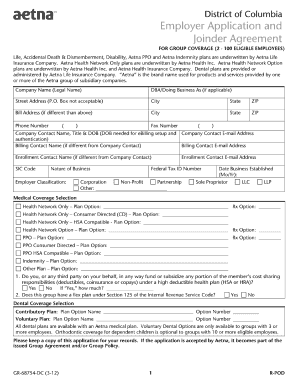
(Please include program name) Employee. Computer System Access Request Form. Activation Deactivation. EMPLOYEE INFORMATION (Please print legibly):
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign non-employee computer system access

Edit your non-employee computer system access form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your non-employee computer system access form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing non-employee computer system access online
To use the services of a skilled PDF editor, follow these steps:
1
Log in. Click Start Free Trial and create a profile if necessary.
2
Upload a document. Select Add New on your Dashboard and transfer a file into the system in one of the following ways: by uploading it from your device or importing from the cloud, web, or internal mail. Then, click Start editing.
3
Edit non-employee computer system access. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
With pdfFiller, it's always easy to work with documents.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out non-employee computer system access

How to fill out non-employee computer system access:
01
Obtain the necessary forms: Start by obtaining the appropriate forms for requesting non-employee computer system access. These forms can usually be obtained from the IT department or the company's HR department.
02
Fill out personal information: Begin by providing your personal information on the form. This typically includes your full name, address, contact details, and any other relevant identification information.
03
Specify the reason for access: Indicate the purpose for which you require non-employee computer system access. It could be for attending a specific training program, conducting temporary work, or any other valid reason that requires access to the company's computer systems.
04
Include details about the duration: State the length of time for which you need access. Specify the start and end dates or mention if it is an ongoing requirement. Make sure to be precise and accurate with these details.
05
Provide references or contacts: Depending on the company's policies, you may need to provide references or contacts who can vouch for your need for access. This can be a supervisor, an employee of the company, or any other relevant individual who can verify your purpose.
06
Sign and submit the form: Once you have completed filling out the form, review it to ensure all information is accurate and complete. Sign the form as required and submit it to the designated department or individual responsible for processing non-employee computer system access requests.
Who needs non-employee computer system access?
01
Contractors and consultants: Many companies hire contractors or consultants for specific projects or tasks. These individuals may require access to the company's computer systems to effectively carry out their work. Non-employee computer system access allows them to perform their duties seamlessly.
02
Temporary employees: When companies hire temporary employees for a short duration, granting them access to the computer systems can enhance their productivity during their assignment. Non-employee computer system access enables temporary employees to perform their work more efficiently.
03
Training program attendees: Some companies offer training programs or workshops to individuals who are not employees but need to access certain computer systems during the training period. Providing non-employee computer system access ensures smooth participation and engagement in the training program.
04
Vendors and business partners: In certain cases, vendors or business partners may require access to specific computer systems to manage inventory, carry out transactions, or collaborate with the company. Granting non-employee computer system access fosters efficient communication and smooth business operations.
05
Freelancers: Freelancers who are hired on a project basis may need access to the company's computer systems to complete their work remotely. Non-employee computer system access allows freelancers to securely connect and contribute to the company's projects.
Remember, the process for filling out non-employee computer system access and the individuals who may need it can vary depending on the company's policies and requirements. It is essential to follow the specific instructions provided by your organization.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Where do I find non-employee computer system access?
It's simple using pdfFiller, an online document management tool. Use our huge online form collection (over 25M fillable forms) to quickly discover the non-employee computer system access. Open it immediately and start altering it with sophisticated capabilities.
How do I make changes in non-employee computer system access?
pdfFiller not only lets you change the content of your files, but you can also change the number and order of pages. Upload your non-employee computer system access to the editor and make any changes in a few clicks. The editor lets you black out, type, and erase text in PDFs. You can also add images, sticky notes, and text boxes, as well as many other things.
Can I sign the non-employee computer system access electronically in Chrome?
Yes. With pdfFiller for Chrome, you can eSign documents and utilize the PDF editor all in one spot. Create a legally enforceable eSignature by sketching, typing, or uploading a handwritten signature image. You may eSign your non-employee computer system access in seconds.
What is non-employee computer system access?
Non-employee computer system access is when individuals who are not employees of a company are granted access to the company's computer systems.
Who is required to file non-employee computer system access?
Any individual or entity that grants non-employees access to their computer systems is required to file non-employee computer system access.
How to fill out non-employee computer system access?
To fill out non-employee computer system access, the individual or entity must provide details of the non-employee accessing the system, the reason for access, and the duration of access.
What is the purpose of non-employee computer system access?
The purpose of non-employee computer system access is to allow external parties such as contractors or vendors to access certain information or systems for specific business purposes.
What information must be reported on non-employee computer system access?
Information such as the name of the non-employee, the reason for access, the duration of access, and any restrictions or limitations imposed must be reported on non-employee computer system access.
Fill out your non-employee computer system access online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Non-Employee Computer System Access is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.