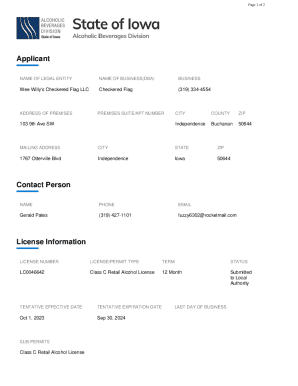
Get the free Rules and Policies for Using the Public Access Computers
Show details
This document outlines the rules and policies for using public access computers at the library, including guidelines for acceptable use, time limits, and responsibilities of users, especially regarding
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign rules and policies for

Edit your rules and policies for form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your rules and policies for form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing rules and policies for online
Use the instructions below to start using our professional PDF editor:
1
Register the account. Begin by clicking Start Free Trial and create a profile if you are a new user.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit rules and policies for. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
With pdfFiller, it's always easy to work with documents. Check it out!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out rules and policies for

How to fill out Rules and Policies for Using the Public Access Computers
01
Begin by reading the overview of the Rules and Policies document.
02
Identify the specific purpose of the public access computers.
03
List acceptable uses of the computers, such as educational, informational, and research purposes.
04
Specify prohibited activities, including illegal downloads, hacking, or harassment.
05
Outline the time limits for computer use to ensure fair access for all users.
06
Include protocols for ensuring data privacy and security for users.
07
Explain the process for reporting issues or violations of the rules.
08
Provide contact information for staff assistance.
09
Review the document for clarity and completeness.
10
Publish the completed Rules and Policies in a visible location near the public access computers.
Who needs Rules and Policies for Using the Public Access Computers?
01
Library staff and administrators who oversee public access computer usage.
02
Users of the public access computers, including students, researchers, and community members.
03
IT personnel responsible for maintaining computer systems and software.
04
Policy makers looking to ensure compliance with regulations and guidelines for public resources.
Fill
form
: Try Risk Free






People Also Ask about
What is a public access computer?
A public access computer is used by many different untrusted individuals throughout the course of the day. The computer must be locked down and secure against both intentional and unintentional abuse. Users typically do not have authority to software or change settings.
What precautions should be taken when using a public computer?
When you use a public computer, be on the lookout for thieves who look over your shoulder or watch as you enter passwords. Don't leave the computer unattended with sensitive information on the screen. If you have to temporarily leave the public computer, log out of all programs and close all windows.
What are the rules for using a computer?
We ask that you follow these rules: Respect the privacy of others. Respect the integrity of the computing systems. Always identify the user accurately. Respect copyrights and licenses. Respect the intellectual property of others. Exhibit responsible, sensible use of computer hardware, software, and data.
What is the policy of computer use?
A computer use policy outlines rules and guidelines for using devices at work. An example includes provisions for acceptable use, password management, software installation remote access, data security, and reporting violations.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is Rules and Policies for Using the Public Access Computers?
Rules and Policies for Using the Public Access Computers are guidelines that outline acceptable and prohibited behaviors for users accessing public computers, ensuring a safe and respectful environment.
Who is required to file Rules and Policies for Using the Public Access Computers?
Typically, library staff or management are required to file and maintain the Rules and Policies for Using the Public Access Computers.
How to fill out Rules and Policies for Using the Public Access Computers?
To fill out the Rules and Policies, a standardized form is completed that includes the guidelines, signatory lines for acknowledgment, and a date of implementation.
What is the purpose of Rules and Policies for Using the Public Access Computers?
The purpose of the Rules and Policies is to promote responsible use of computer resources, to protect users' privacy, and to prevent misuse or damage to the equipment.
What information must be reported on Rules and Policies for Using the Public Access Computers?
The information that must be reported includes the list of acceptable use, prohibited activities, consequences for violations, and contact information for assistance.
Fill out your rules and policies for online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Rules And Policies For is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.