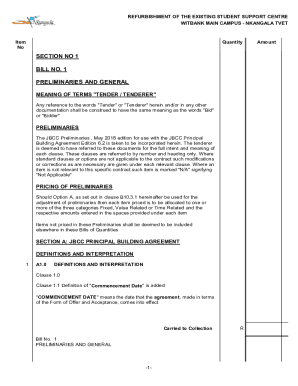
Get the free BEA WebLogic Understanding WebLogic Security
Show details
This document provides detailed information on WebLogic Security, describing its architecture, security service provider interfaces, and various security mechanisms like authentication and authorization
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign bea weblogic understanding weblogic

Edit your bea weblogic understanding weblogic form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your bea weblogic understanding weblogic form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit bea weblogic understanding weblogic online
Follow the guidelines below to benefit from the PDF editor's expertise:
1
Log in. Click Start Free Trial and create a profile if necessary.
2
Prepare a file. Use the Add New button to start a new project. Then, using your device, upload your file to the system by importing it from internal mail, the cloud, or adding its URL.
3
Edit bea weblogic understanding weblogic. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
pdfFiller makes working with documents easier than you could ever imagine. Register for an account and see for yourself!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out bea weblogic understanding weblogic

How to fill out BEA WebLogic Understanding WebLogic Security
01
Access the BEA WebLogic Server console.
02
Navigate to the 'Security Realms' section.
03
Locate and select the security realm you wish to configure.
04
Set up the desired authentication providers under the 'Providers' tab.
05
Configure roles and policies for user access under the 'Authorization' tab.
06
Review and configure SSL settings to ensure secure communications.
07
Save and activate the changes made.
08
Test the security configuration to ensure it operates as expected.
Who needs BEA WebLogic Understanding WebLogic Security?
01
System administrators managing WebLogic Server.
02
Security professionals overseeing application security.
03
Developers implementing security features in applications.
04
Organizations using WebLogic for enterprise applications.
Fill
form
: Try Risk Free






People Also Ask about
What is a role based security role?
In role-based security, access isn't granted to individual users, only to security roles. Users are assigned to roles. A user who is assigned to a security role has access to the set of privileges that is associated with that role. A user who isn't assigned to any role has no privileges.
What is the difference between a security role and a business unit?
A Business unit is all or part of an organization. A security role is a collection of privileges and access levels. An entity is a collection of records, such as a sales deal, or prospect. Privileges allow users in a role to take actions on records in an entity.
How do I change the password for WebLogic?
Sign in to the WebLogic Server Administration Console. Under Domain Structure, click Security Realms. In the Summary of Security Realms page, select myrealm, and then click Users and Groups tab. Click the passwords tab for the weblogic user and update the password.
What is the default authenticator in WebLogic?
The WebLogic Authentication provider (also called the DefaultAuthenticator) uses Oracle WebLogic Server's embedded LDAP server to store user and group membership information and, optionally, a set of user attributes such as phone number, email address, and so on.
What is a secure role?
A security role is a set of privileges and the level of access to various actions/functions within the platform. Security roles allow you to configure the security items, that is, the access privileges on CRUD operations for entities in the data model.
What is a security role in WebLogic?
A security role is an identity granted to users or groups based on specific conditions. Multiple users or groups can be granted the same security role and a user or group can be in more than one security role. Security roles are used by policies to determine who can access a WebLogic resource.
What is the purpose of a security role?
Security roles define how different users access different types of records. To control access to data and resources, you can create or modify security roles and change the security roles that are assigned to users. A user can have multiple security roles. Security role privileges are cumulative.
For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is BEA WebLogic Understanding WebLogic Security?
BEA WebLogic Understanding WebLogic Security refers to the security framework and features provided by WebLogic Server to protect applications and data from unauthorized access and threats, ensuring secure operations and management of resources.
Who is required to file BEA WebLogic Understanding WebLogic Security?
Individuals or organizations deploying applications on the WebLogic Server that require compliance with security standards and best practices are typically required to file BEA WebLogic Understanding WebLogic Security.
How to fill out BEA WebLogic Understanding WebLogic Security?
To fill out BEA WebLogic Understanding WebLogic Security, users should provide detailed information on the security configurations, policies, and practices in place to safeguard their WebLogic applications, focusing on aspects such as authentication, authorization, auditing, and encryption.
What is the purpose of BEA WebLogic Understanding WebLogic Security?
The purpose of BEA WebLogic Understanding WebLogic Security is to establish a clear understanding of the security measures implemented in a WebLogic environment, ensuring compliance, enhancing security posture, and protecting sensitive data from threats.
What information must be reported on BEA WebLogic Understanding WebLogic Security?
Information that must be reported includes security policies, user roles, authentication mechanisms, data encryption methods, audit logs, security vulnerabilities identified, and the measures taken to mitigate them.
Fill out your bea weblogic understanding weblogic online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Bea Weblogic Understanding Weblogic is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.