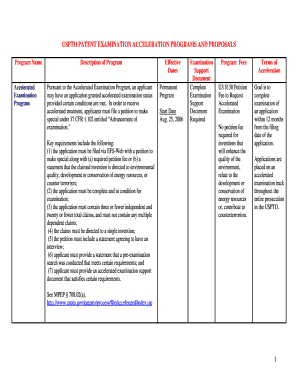
Get the free CYBER SECURITY INCIDENT REQUEST FOR ASSISTANCE FORM - bNCSCb - ncsc govt
Show details
Cybersecurity INCIDENT REQUEST FOR ASSISTANCE FORM (Evaluation Services) This form can be used to request assistance from the National Cyber Security Center (NTSC) in relation to a cybersecurity incident.
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign cyber security incident request

Edit your cyber security incident request form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your cyber security incident request form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit cyber security incident request online
Follow the steps down below to use a professional PDF editor:
1
Log in. Click Start Free Trial and create a profile if necessary.
2
Prepare a file. Use the Add New button to start a new project. Then, using your device, upload your file to the system by importing it from internal mail, the cloud, or adding its URL.
3
Edit cyber security incident request. Text may be added and replaced, new objects can be included, pages can be rearranged, watermarks and page numbers can be added, and so on. When you're done editing, click Done and then go to the Documents tab to combine, divide, lock, or unlock the file.
4
Get your file. When you find your file in the docs list, click on its name and choose how you want to save it. To get the PDF, you can save it, send an email with it, or move it to the cloud.
With pdfFiller, it's always easy to work with documents.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out cyber security incident request

How to fill out a cyber security incident request:
01
Start by gathering all relevant information: Before filling out the incident request, make sure you have all the necessary details of the cyber security incident. This includes information about the affected systems, any suspicious activities or indicators, and any potential impact on the organization.
02
Provide a concise description of the incident: In the incident request, clearly and accurately describe the nature of the cyber security incident. Include details such as the date and time of the incident, the affected systems or assets, and a brief summary of what occurred.
03
Classify the severity and impact of the incident: Assess the severity and potential impact of the cyber security incident. Use predefined categories or levels to classify the incident and its consequences. This information helps prioritize incident response efforts and allocate appropriate resources.
04
Identify the individuals involved or affected: Specify the individuals or departments that are involved or affected by the incident. This can include both internal personnel and external stakeholders. Providing this information helps ensure that the incident response team can notify and involve the right people in the resolution process.
05
Document any evidence or findings: If possible, include any evidence or findings relevant to the incident. This might include logs, screenshots, or any other digital artifacts that can help in investigating and understanding the incident. Providing this information can expedite the incident response process and enable a more accurate analysis.
06
Determine the reporting and escalation procedures: Understand and follow the established reporting and escalation procedures for cyber security incidents in your organization. Ensure that you include the appropriate individuals or teams in the incident request, based on the severity and impact of the incident. Following the proper procedures helps ensure a swift and coordinated response.
Who needs a cyber security incident request?
A cyber security incident request is typically needed by organizations that have experienced a cyber security incident. This can include businesses, government agencies, non-profit organizations, or any other entity that relies on information systems and infrastructure. The incident request is used to notify the organization's incident response team, IT department, or any other relevant parties about the occurrence of the incident, triggering a series of actions to mitigate the impact and investigate the incident further. The request helps ensure that the incident is properly documented and that the appropriate response measures are initiated in a timely manner.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I edit cyber security incident request from Google Drive?
By combining pdfFiller with Google Docs, you can generate fillable forms directly in Google Drive. No need to leave Google Drive to make edits or sign documents, including cyber security incident request. Use pdfFiller's features in Google Drive to handle documents on any internet-connected device.
How do I fill out the cyber security incident request form on my smartphone?
Use the pdfFiller mobile app to complete and sign cyber security incident request on your mobile device. Visit our web page (https://edit-pdf-ios-android.pdffiller.com/) to learn more about our mobile applications, the capabilities you’ll have access to, and the steps to take to get up and running.
How do I fill out cyber security incident request on an Android device?
Use the pdfFiller mobile app to complete your cyber security incident request on an Android device. The application makes it possible to perform all needed document management manipulations, like adding, editing, and removing text, signing, annotating, and more. All you need is your smartphone and an internet connection.
What is cyber security incident request?
Cyber security incident request is a formal notification submitted to report a cyber security incident that has occurred.
Who is required to file cyber security incident request?
Any individual or organization that has experienced a cyber security incident is required to file a cyber security incident request.
How to fill out cyber security incident request?
Cyber security incident request can be filled out by providing details of the incident, impact analysis, and any mitigation measures taken.
What is the purpose of cyber security incident request?
The purpose of cyber security incident request is to allow organizations to report and document cyber security incidents for analysis and improvement of security measures.
What information must be reported on cyber security incident request?
Information that must be reported on cyber security incident request includes details of the incident, impact on operations, and any mitigation steps taken.
Fill out your cyber security incident request online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Cyber Security Incident Request is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.