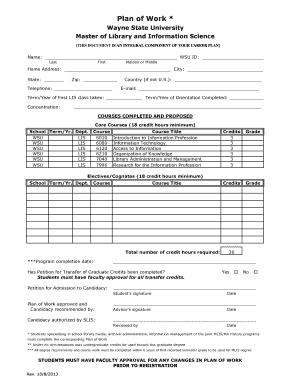
Get the free Secure Coding Practices for .NET ApplicationsWPFinal - CGISecurity
Show details
Secure Coding Practices for Microsoft .NET Applications White Paper Amit Klein, Director of Security and Research Sanctum, Inc. Sanctum, the Sanctum logo, Applied, App Scan, App Scan DE, Policy Recognition
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign secure coding practices for

Edit your secure coding practices for form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your secure coding practices for form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing secure coding practices for online
Use the instructions below to start using our professional PDF editor:
1
Log in to your account. Click on Start Free Trial and sign up a profile if you don't have one yet.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit secure coding practices for. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Save your file. Select it from your list of records. Then, move your cursor to the right toolbar and choose one of the exporting options. You can save it in multiple formats, download it as a PDF, send it by email, or store it in the cloud, among other things.
pdfFiller makes working with documents easier than you could ever imagine. Create an account to find out for yourself how it works!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out secure coding practices for

How to fill out secure coding practices for?
01
First, gather information about the specific coding practices that need to be addressed. This can include guidelines provided by industry standards, regulatory bodies, or best practices recommended by cybersecurity experts.
02
Review the existing codebase and identify any vulnerabilities or weaknesses. This can be done through static code analysis tools or manual code reviews. Pay attention to common security vulnerabilities such as injection attacks, cross-site scripting (XSS), and insecure data storage.
03
Implement security controls and practices that are relevant to the application or system being developed. This may include input validation, output encoding, secure session management, and secure authentication mechanisms.
04
Regularly update and patch the software libraries and dependencies used in the project. Keep track of any security vulnerabilities reported in these components and apply the necessary fixes promptly.
05
Educate the development team about secure coding practices and provide training sessions to improve their awareness of potential security risks. Encourage them to follow coding conventions and adhere to secure coding guidelines.
Who needs secure coding practices for?
01
Software developers and engineers: Secure coding practices are crucial for developers who write and maintain software applications. They are responsible for implementing security controls and ensuring that the code they write is free from vulnerabilities.
02
IT managers and security officers: These professionals play a crucial role in establishing policies and procedures related to secure coding practices. They should enforce strict guidelines and ensure that the development team follows them to mitigate potential security risks.
03
Organizations and businesses: Any organization that develops or uses software applications should prioritize secure coding practices. This includes enterprises, government agencies, and any entity that relies on software to operate their systems or process sensitive data.
In summary, filling out secure coding practices requires gathering information, assessing vulnerabilities, implementing security controls, updating dependencies, and educating the development team. It is essential for developers, IT managers, security officers, and organizations that develop or use software applications.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How do I modify my secure coding practices for in Gmail?
You may use pdfFiller's Gmail add-on to change, fill out, and eSign your secure coding practices for as well as other documents directly in your inbox by using the pdfFiller add-on for Gmail. pdfFiller for Gmail may be found on the Google Workspace Marketplace. Use the time you would have spent dealing with your papers and eSignatures for more vital tasks instead.
How can I edit secure coding practices for from Google Drive?
Using pdfFiller with Google Docs allows you to create, amend, and sign documents straight from your Google Drive. The add-on turns your secure coding practices for into a dynamic fillable form that you can manage and eSign from anywhere.
How do I fill out secure coding practices for on an Android device?
Use the pdfFiller Android app to finish your secure coding practices for and other documents on your Android phone. The app has all the features you need to manage your documents, like editing content, eSigning, annotating, sharing files, and more. At any time, as long as there is an internet connection.
What is secure coding practices for?
Secure coding practices are guidelines and rules that developers follow to write software code that is secure, minimizing vulnerabilities and reducing the risks of security threats.
Who is required to file secure coding practices for?
Secure coding practices are not filed by individuals or organizations. Instead, they are implemented and followed by software developers and development teams to ensure the security of their code.
How to fill out secure coding practices for?
Secure coding practices are not filled out in a traditional sense. Rather, they are adopted and implemented in the development process by following established guidelines, best practices, and security standards.
What is the purpose of secure coding practices for?
The purpose of secure coding practices is to prevent and mitigate security vulnerabilities and threats in software applications. By following secure coding practices, developers can reduce the risk of cyber attacks, data breaches, and unauthorized access to sensitive information.
What information must be reported on secure coding practices for?
Secure coding practices do not require reporting specific information. Instead, they focus on implementing secure coding techniques, secure authentication mechanisms, input validation, secure error handling, and other security practices to minimize vulnerabilities.
Fill out your secure coding practices for online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Secure Coding Practices For is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.