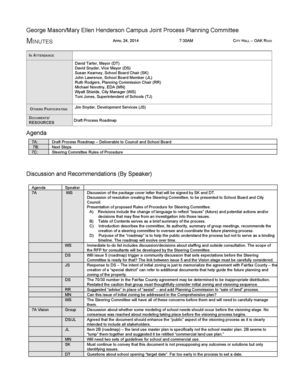
Get the free Text Evidence Attack at Sea February/March 2016 Core Skills WorkoutLL Name: Date: Fi...
Show details
Text Evidence Attack at Sea February×March 2016 Core Skills Workout LL Name: Date: Find the Evidence Directions: Read each question below carefully. Some will ask you to select text evidence or details
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign text evidence attack at

Edit your text evidence attack at form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your text evidence attack at form via URL. You can also download, print, or export forms to your preferred cloud storage service.
Editing text evidence attack at online
To use our professional PDF editor, follow these steps:
1
Create an account. Begin by choosing Start Free Trial and, if you are a new user, establish a profile.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit text evidence attack at. Rearrange and rotate pages, add and edit text, and use additional tools. To save changes and return to your Dashboard, click Done. The Documents tab allows you to merge, divide, lock, or unlock files.
4
Get your file. Select the name of your file in the docs list and choose your preferred exporting method. You can download it as a PDF, save it in another format, send it by email, or transfer it to the cloud.
Dealing with documents is simple using pdfFiller. Now is the time to try it!
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out text evidence attack at

To fill out a text evidence attack at, follow these steps:
01
Begin by identifying the specific text or piece of evidence that you will be analyzing. This could be a passage from a book, an article, or any written material that supports your argument.
02
Next, clearly state your attack on the text evidence. This means explaining how the evidence is flawed, biased, or unreliable. Provide specific examples or reasons to support your attack.
03
Provide additional evidence or examples to refute the credibility of the text evidence. This could involve analyzing the author's credentials, exploring any potential biases, or pointing out logical fallacies within the text.
04
Connect your attack on the text evidence to your overall argument or thesis. Explain why debunking this particular piece of evidence is crucial in weakening the opposing viewpoint or strengthening your own position.
05
Conclude your text evidence attack by summarizing the main points and re-emphasizing the flaws in the evidence. This helps to leave a lasting impact on the reader and reinforce the validity of your argument.
Who needs text evidence attack at?
Text evidence attack can be useful for various individuals and in different situations. Some examples include:
01
Students: Students may need to use text evidence attack in their academic writing, such as when writing essays or research papers. By critically analyzing and challenging the evidence they encounter, students can enhance their analytical skills and demonstrate a deeper understanding of the subject matter.
02
Debaters: In formal debates, being able to effectively attack text evidence is crucial. Debaters use text evidence attack to challenge their opponents' arguments, weaken their evidence, and persuade the audience to support their own viewpoint.
03
Researchers: Researchers often encounter various texts and studies during their research process. They may need to evaluate the credibility and reliability of these texts through text evidence attack, ensuring that they are making informed decisions and forming accurate conclusions based on reliable evidence.
Overall, anyone who wants to critically analyze and challenge the text evidence they encounter can benefit from learning how to perform a text evidence attack. It is a valuable skill that promotes critical thinking, strengthens arguments, and fosters a deeper understanding of a subject matter.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
What is text evidence attack at?
Text evidence attack is an attack that manipulates or fabricates text-based evidence to mislead or deceive others.
Who is required to file text evidence attack at?
Any individual, organization, or entity who has evidence of text manipulation or fabrication is required to file a text evidence attack report.
How to fill out text evidence attack at?
To fill out a text evidence attack report, one must provide detailed information on the manipulated or fabricated text, any suspicious activity related to the text, and any other relevant details.
What is the purpose of text evidence attack at?
The purpose of text evidence attack is to alert authorities and potential victims of the presence of manipulated or fabricated text-based evidence.
What information must be reported on text evidence attack at?
The report must include details of the manipulated or fabricated text, any suspicious activity related to the text, any potential victims or targets of the attack, and any other relevant information.
How can I get text evidence attack at?
It’s easy with pdfFiller, a comprehensive online solution for professional document management. Access our extensive library of online forms (over 25M fillable forms are available) and locate the text evidence attack at in a matter of seconds. Open it right away and start customizing it using advanced editing features.
Can I create an electronic signature for the text evidence attack at in Chrome?
You certainly can. You get not just a feature-rich PDF editor and fillable form builder with pdfFiller, but also a robust e-signature solution that you can add right to your Chrome browser. You may use our addon to produce a legally enforceable eSignature by typing, sketching, or photographing your signature with your webcam. Choose your preferred method and eSign your text evidence attack at in minutes.
How do I fill out text evidence attack at on an Android device?
Complete your text evidence attack at and other papers on your Android device by using the pdfFiller mobile app. The program includes all of the necessary document management tools, such as editing content, eSigning, annotating, sharing files, and so on. You will be able to view your papers at any time as long as you have an internet connection.
Fill out your text evidence attack at online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Text Evidence Attack At is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.