
Get the free Targeted Trojan Email Attacks - Security Management
Show details
NI SCC Briefing 08/2005 Issued 16 June 2005 Targeted Trojan Email Attacks Reference to any specific commercial product, process, or service by trade name, trademark manufacturer, or otherwise, does
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign targeted trojan email attacks
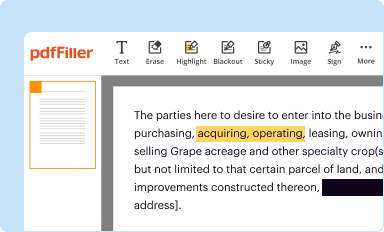
Edit your targeted trojan email attacks form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.
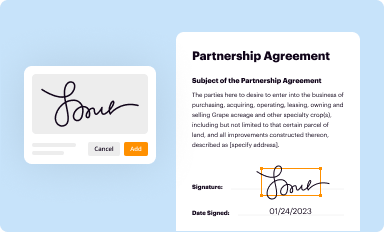
Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your targeted trojan email attacks form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit targeted trojan email attacks online
To use our professional PDF editor, follow these steps:
1
Log in to account. Click Start Free Trial and sign up a profile if you don't have one yet.
2
Simply add a document. Select Add New from your Dashboard and import a file into the system by uploading it from your device or importing it via the cloud, online, or internal mail. Then click Begin editing.
3
Edit targeted trojan email attacks. Rearrange and rotate pages, add new and changed texts, add new objects, and use other useful tools. When you're done, click Done. You can use the Documents tab to merge, split, lock, or unlock your files.
4
Save your file. Select it from your records list. Then, click the right toolbar and select one of the various exporting options: save in numerous formats, download as PDF, email, or cloud.
Dealing with documents is simple using pdfFiller.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out targeted trojan email attacks
01
To initiate targeted trojan email attacks, attackers need to carefully select their victims and collect their email addresses or other contact information.
02
The attackers then need to create a convincing email message that appears trustworthy and enticing to the recipients. This could involve using social engineering techniques, such as impersonating a trusted organization or individual.
03
The email should contain the trojan payload, which is a malicious file or link that, once clicked or opened, infects the victim's computer or steals sensitive information.
04
Attackers may also employ obfuscation techniques to hide the true nature of the email or the trojan payload, increasing the chances of successful infiltration.
05
It is crucial for attackers to continuously update and modify their trojan email attacks to evade detection by security systems and remain effective.
06
The goal of targeted trojan email attacks is often to gain unauthorized access to sensitive data, compromise computer systems, or conduct further malicious activities, such as financial fraud or espionage.
Who needs targeted trojan email attacks?
01
Cybercriminals or hackers who have malicious intent and want to exploit vulnerabilities in computer systems or steal sensitive information may deploy targeted trojan email attacks. These individuals or groups may be motivated by financial gain, political agendas, or personal reasons.
02
Industrial spies or competitors seeking to gain a competitive advantage may also employ targeted trojan email attacks to compromise the security of rival companies or organizations.
03
Advanced persistent threat (APT) groups, which are typically state-sponsored, may use targeted trojan email attacks as part of their sophisticated cyber espionage campaigns, aiming to gather intelligence or disrupt targeted entities.
It is important to note that targeted trojan email attacks are illegal and unethical. This answer is provided solely for informational purposes and does not endorse or support any unlawful activities.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
How can I send targeted trojan email attacks to be eSigned by others?
When your targeted trojan email attacks is finished, send it to recipients securely and gather eSignatures with pdfFiller. You may email, text, fax, mail, or notarize a PDF straight from your account. Create an account today to test it.
How do I make edits in targeted trojan email attacks without leaving Chrome?
Install the pdfFiller Google Chrome Extension to edit targeted trojan email attacks and other documents straight from Google search results. When reading documents in Chrome, you may edit them. Create fillable PDFs and update existing PDFs using pdfFiller.
Can I create an electronic signature for the targeted trojan email attacks in Chrome?
Yes, you can. With pdfFiller, you not only get a feature-rich PDF editor and fillable form builder but a powerful e-signature solution that you can add directly to your Chrome browser. Using our extension, you can create your legally-binding eSignature by typing, drawing, or capturing a photo of your signature using your webcam. Choose whichever method you prefer and eSign your targeted trojan email attacks in minutes.
What is targeted trojan email attacks?
Targeted trojan email attacks refer to cyberattacks where malicious actors send emails containing trojan horse malware to specific individuals or organizations with the intention of stealing sensitive information or gaining unauthorized access to systems.
Who is required to file targeted trojan email attacks?
There is no specific requirement to file targeted trojan email attacks as they are illegal activities conducted by cybercriminals. It is the responsibility of individuals or organizations who fall victim to such attacks to report them to the appropriate law enforcement authorities.
How to fill out targeted trojan email attacks?
Targeted trojan email attacks cannot be filled out as they are criminal acts. However, if you become a victim of such an attack, it is advisable to report it to your local law enforcement agency or cybersecurity incident response team.
What is the purpose of targeted trojan email attacks?
The purpose of targeted trojan email attacks is to gain unauthorized access to systems, steal sensitive information, or perform other malicious activities such as ransomware attacks or espionage.
What information must be reported on targeted trojan email attacks?
If you are a victim of a targeted trojan email attack, it is important to report as much information as possible to assist law enforcement in their investigations. This may include details about the email, any attachments or links involved, information about the sender, and any observations or evidence of suspicious activity.
Fill out your targeted trojan email attacks online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Targeted Trojan Email Attacks is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.





















