Get the free Wireless Hacking Tablet
Show details
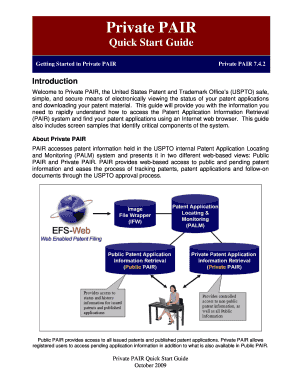
Wireless Hacking Tablet
This document will go into detail configuring Fedora Core 4 on a Motion Computing
m1300 tablet for wireless sniffing, encryption hacking, and client hijacking.
NOTE: Only the
We are not affiliated with any brand or entity on this form
Get, Create, Make and Sign wireless hacking tablet

Edit your wireless hacking tablet form online
Type text, complete fillable fields, insert images, highlight or blackout data for discretion, add comments, and more.

Add your legally-binding signature
Draw or type your signature, upload a signature image, or capture it with your digital camera.

Share your form instantly
Email, fax, or share your wireless hacking tablet form via URL. You can also download, print, or export forms to your preferred cloud storage service.
How to edit wireless hacking tablet online
Here are the steps you need to follow to get started with our professional PDF editor:
1
Log in. Click Start Free Trial and create a profile if necessary.
2
Upload a file. Select Add New on your Dashboard and upload a file from your device or import it from the cloud, online, or internal mail. Then click Edit.
3
Edit wireless hacking tablet. Rearrange and rotate pages, insert new and alter existing texts, add new objects, and take advantage of other helpful tools. Click Done to apply changes and return to your Dashboard. Go to the Documents tab to access merging, splitting, locking, or unlocking functions.
4
Get your file. Select your file from the documents list and pick your export method. You may save it as a PDF, email it, or upload it to the cloud.
With pdfFiller, it's always easy to work with documents.
Uncompromising security for your PDF editing and eSignature needs
Your private information is safe with pdfFiller. We employ end-to-end encryption, secure cloud storage, and advanced access control to protect your documents and maintain regulatory compliance.
How to fill out wireless hacking tablet

How to Fill Out Wireless Hacking Tablet:
01
Start by researching and selecting a reliable wireless hacking tablet that meets your requirements. Consider factors such as processing power, storage capacity, and compatibility with the hacking software you plan to use.
02
Once you have acquired the tablet, unpack it carefully and ensure that all the necessary components are present, such as the charger, stylus, and any additional accessories.
03
Power on the tablet by pressing and holding the power button. Follow the on-screen instructions to set up the device, including connecting to a Wi-Fi network, signing in with your Google or Apple account, and configuring any additional settings according to your preferences.
04
Next, download and install robust hacking software onto the tablet. It is advisable to install reputable and ethical software, as engaging in unauthorized hacking activities can be illegal and unethical. Always ensure that you abide by the laws and guidelines of your jurisdiction.
05
Once the hacking software is installed, familiarize yourself with its interface and features. Take the time to understand the functions and capabilities of the software, as this will enable you to make the most out of your wireless hacking tablet.
06
Before engaging in any hacking activities, ensure that you have obtained the necessary permissions and approvals. Unauthorized hacking can lead to severe legal consequences. Always use the hacking tablet responsibly and for legitimate purposes, such as testing network security or performing authorized penetration testing.
07
Finally, make sure to keep your wireless hacking tablet updated with the latest software patches and security fixes. This will ensure that you can benefit from the latest features and stay protected against any potential vulnerabilities.
Who Needs a Wireless Hacking Tablet?
01
Cybersecurity Professionals: Wireless hacking tablets can be valuable tools for cybersecurity professionals to assess and strengthen the security of computer networks. They can be utilized for tasks like identifying vulnerabilities, testing system defenses, and developing effective security strategies.
02
Ethical Hackers: Individuals who are authorized to hack into systems to identify weaknesses and enhance security use wireless hacking tablets. These ethical hackers work to expose vulnerabilities and help organizations strengthen their defenses against malicious cyber-attacks.
03
Network Administrators: Wireless hacking tablets can aid network administrators in maintaining and securing wireless networks. They can be used to analyze network traffic, identify unauthorized access points, and troubleshoot network issues effectively.
04
IT Security Researchers: Researchers studying computer security and developing innovative security technologies often use wireless hacking tablets to conduct experiments and test their theories. These tablets offer a portable and versatile platform for their research activities.
05
Technology Enthusiasts: Some technology enthusiasts may acquire a wireless hacking tablet to explore and understand the world of cybersecurity better. Such tablets can be used for educational purposes or to learn new hacking techniques in a controlled and responsible manner.
It is important to note that wireless hacking tablets should only be used in ethical and legal contexts, with proper authorization and adherence to applicable laws and regulations.
Fill
form
: Try Risk Free






For pdfFiller’s FAQs
Below is a list of the most common customer questions. If you can’t find an answer to your question, please don’t hesitate to reach out to us.
Can I create an electronic signature for the wireless hacking tablet in Chrome?
You certainly can. You get not just a feature-rich PDF editor and fillable form builder with pdfFiller, but also a robust e-signature solution that you can add right to your Chrome browser. You may use our addon to produce a legally enforceable eSignature by typing, sketching, or photographing your signature with your webcam. Choose your preferred method and eSign your wireless hacking tablet in minutes.
How do I fill out wireless hacking tablet using my mobile device?
Use the pdfFiller mobile app to complete and sign wireless hacking tablet on your mobile device. Visit our web page (https://edit-pdf-ios-android.pdffiller.com/) to learn more about our mobile applications, the capabilities you’ll have access to, and the steps to take to get up and running.
How do I complete wireless hacking tablet on an iOS device?
Install the pdfFiller iOS app. Log in or create an account to access the solution's editing features. Open your wireless hacking tablet by uploading it from your device or online storage. After filling in all relevant fields and eSigning if required, you may save or distribute the document.
What is wireless hacking tablet?
Wireless hacking tablet is a device used for unauthorized access to wireless networks.
Who is required to file wireless hacking tablet?
Individuals or entities who engage in wireless hacking activities are required to file wireless hacking tablet.
How to fill out wireless hacking tablet?
To fill out wireless hacking tablet, provide detailed information about the hacking activities, networks targeted, and methods used.
What is the purpose of wireless hacking tablet?
The purpose of wireless hacking tablet is to document and report illegal hacking activities on wireless networks.
What information must be reported on wireless hacking tablet?
Information such as date and time of hacking activities, affected networks, and tools used must be reported on wireless hacking tablet.
Fill out your wireless hacking tablet online with pdfFiller!
pdfFiller is an end-to-end solution for managing, creating, and editing documents and forms in the cloud. Save time and hassle by preparing your tax forms online.

Wireless Hacking Tablet is not the form you're looking for?Search for another form here.
Relevant keywords
Related Forms
If you believe that this page should be taken down, please follow our DMCA take down process
here
.
This form may include fields for payment information. Data entered in these fields is not covered by PCI DSS compliance.